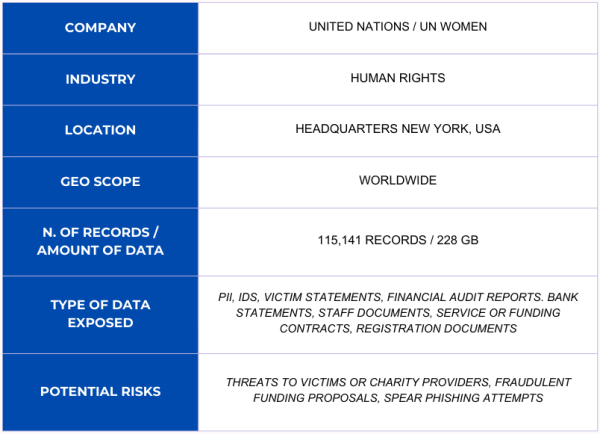
Over 115,000 United Nations Documents Associated to Gender Equality Exposed Online

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password-protected database that contained 115,000 records associated with the UN Trust Fund to End Violence against Women — aimed at preventing and addressing violence against women and girls by providing financial and technical support to local, national, and regional organizations working to eliminate gender-based violence and promote women's rights.
The non-password protected, non encrypted/clear text database contained financial reports and audits (including bank account information), staff documents, email addresses, contracts, certifications, registration documents, and much more. In total, the database held 115,141 files in.PDF,.xml,.jpg,,png, or other formats, amounting to 228 GB. Many of the documents I saw were marked as confidential and should have not been made publicly available. One single.xls file contained a list of 1,611 civil society organizations, including their internal UN application numbers, whether they are eligible for support, the status of their applications, whether they are local or national, and a range of detailed answers regarding the groups’ missions.
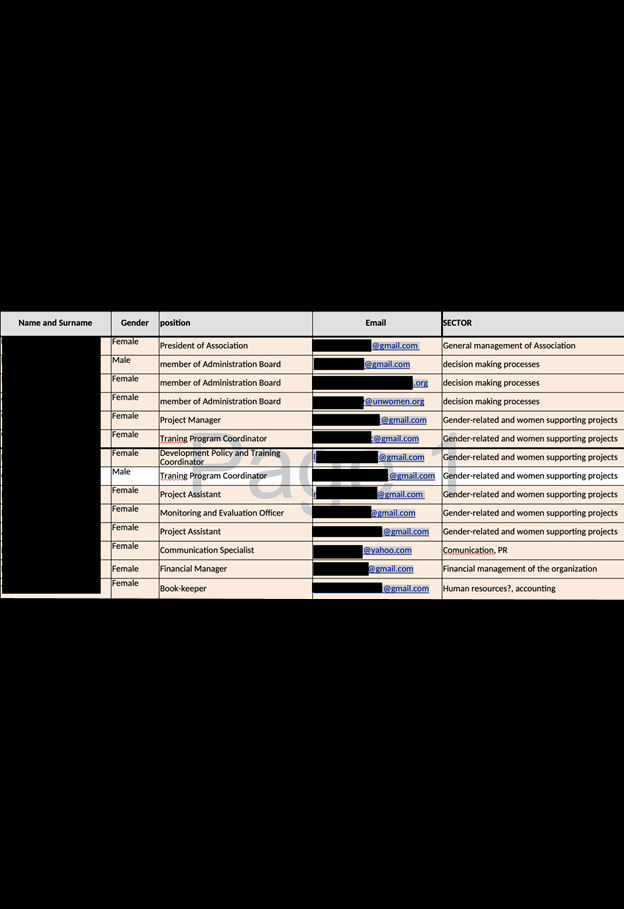
I also saw numerous scanned passports, ID cards, and staff directories of individual organizations. The staff documents included staff names, tax data, salary information, and job roles. There were also documents labeled as “victim success stories” or testimonies. Some of these contained the names and email addresses of those helped by the programs, as well as details of their personal experiences. For instance, one of the letters purported to be from a Chibok schoolgirl who was one of the 276 individuals kidnapped by Boko Haram in 2014. Exposure of this information could potentially have serious privacy or safety implications to charity workers and those individuals they provide assistance or services to.
The records indicated an association with UN Women and the UN Trust Fund to End Violence against Women. For instance, there were reference letters addressed directly to the UN, documents stamped with UN logos, and file names indicating the UN Women organization. I immediately sent a responsible disclosure notice of my findings to the general UN InfoSec address and UN Women, and public access to the database was restricted the following day. I received an immediate reply to my disclosure notice from the UN Information Security team stating “The reported vulnerability does not pertain to us (the United Nations Secretariat) and is for UN Women. Please report the vulnerability to UN WOMEN”.
Although the records indicated the files belonged to the UN Women agency, it is not known if they owned and managed the non-password protected database or if it was under the control of a third-party contractor. It is also unknown how long the records were exposed or if anyone else accessed them, as only an internal forensic audit can identify that information. I did not receive a reply from UN Women at the time of publication.
According to their website, “the UN Trust Fund to End Violence against Women (UN Trust Fund) awards grants to initiatives demonstrating that violence against women and girls can be systematically addressed, reduced, and, with persistence, eliminated”. The fund is managed by UN Women on behalf of the UN system. It provides financial support to initiatives and organizations, particularly those led by women, working to end gender-based violence. The fund has awarded an estimated $225 million USD to 670 initiatives in 140 countries and territories.
A scam alert was issued in an undated post on their website that reads “UN Women has been made aware of various correspondences—circulated via email, websites, social media, regular mail, or facsimile—falsely stating that they are issued by, or in association with UN Women, the United Nations, and/or its officials. These scams, which may seek to obtain money and/or, in many cases, personal details from the recipients of such correspondence, are fraudulent”. These scams typically operate by impersonating reputable organizations or individuals and requesting application fees, dues, or other payments.
I would advise any charity to be vigilant and take extra caution when receiving suspicious requests for personal or financial information, especially if they are unsolicited payment requests. One way to do this is by carefully verifying the source of any communications. Ensure that information requests originate from official email addresses and validate any change in payment methods or accounts. Implementing additional security measures can also help reduce the chances of the organization being the victim of a cybercrime. Furthermore, training staff on the risks of fraud and common social engineering tactics can help prevent the unwitting sharing of potentially sensitive information to unauthorized individuals.
In this case, there were thousands of internal documents that were accessible to anyone with an internet connection. They were not password-protected. These documents could potentially provide criminals with insights into how the organizations operate, their key management, financial structures, and other details that may not have been intended to be public. With insider knowledge of names, accounts, partnerships, and audit records criminals could build trust and potentially launch targeted spear phishing campaigns using information that no one outside of the organization or UN should know. Hypothetically, criminals could use or alter exposed documents to gain additional personal information from charity workers and staff.
Many of the charities operate in countries and regions where the potential threat of violence against women and members of the LGBTQ community is a serious safety concern. Protecting the privacy and identities of these individuals is extremely important. Criminals could potentially use social engineering methods to target charity workers — not only for financial gain, but in an effort to obtain the identities of vulnerable individuals who receive assistance from an organization. I am not saying that these organizations or individuals were ever at risk of social engineering, phishing, or any other criminal activities. I am only providing a real-world threat scenario in hopes of raising awareness of the importance of data security.
It should be noted that when researching UN Women for this report, I did not find any public cases of fraud or misuse directly linked to the UN Trust Fund. However, no system is completely immune to fraud or attempts to obtain funds from agencies like the UN or other civil society organizations. The audits and accounting documents I saw in the non-password-protected database indicate there are strict oversight systems in place to ensure that funds are allocated properly. I am not implying any wrongdoing by UN Women, their associates, partners, donors, recipients, or third-party contractors, nor do I claim that internal data or organization-level data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification and reporting purposes. It is not known how long the files were publicly accessible, as only an internal forensic investigation conducted by UN Women or the responsible database management provider would be able to identify this information along with any potential suspicious activity related to the breach. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties, and I expressly disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not perform any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues. It is essential for relevant parties to conduct their own investigations and take appropriate security measures.








Please, comment on how to improve this article. Your feedback matters!