Nearly 500k UK Health Club Chain Members' Images Exposed in a Data Breach

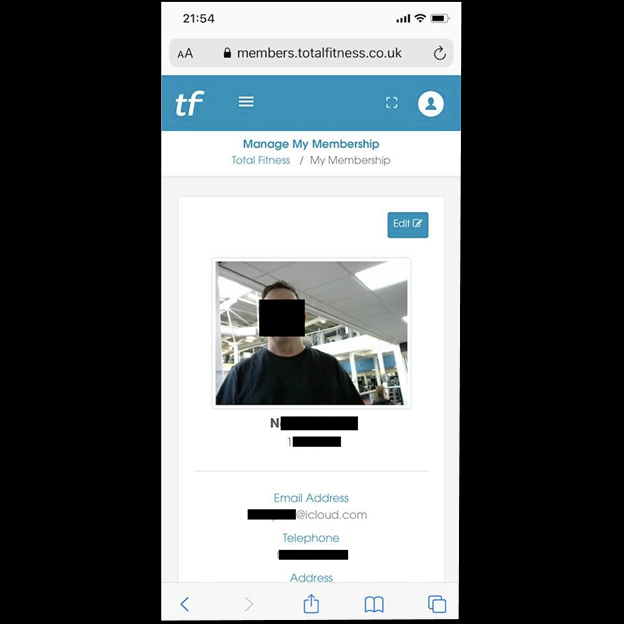
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password-protected database that contained 474k images belonging to Total Fitness — a chain of health clubs with 15 locations across North England and Wales, over 100,000 members, and about 600 employees. The images included personal screenshots (some containing PII), as well as profile pictures of members and their children.
The non-password-protected database contained 474,651 images with a total size of 47.7 GB. The database was marked as production and included facial images of gym employees, members, and children. Upon further research, there were numerous indicators that the images belonged to UK-based Total Fitness. For instance, some images appeared to be taken by staff inside the gym while completing the membership process; the Total Fitness logo could be seen in the background and on the shirts of employees. The vast majority of images, however, appeared to be self-submitted by members for their account profiles or in the case of children by their parents or guardians.
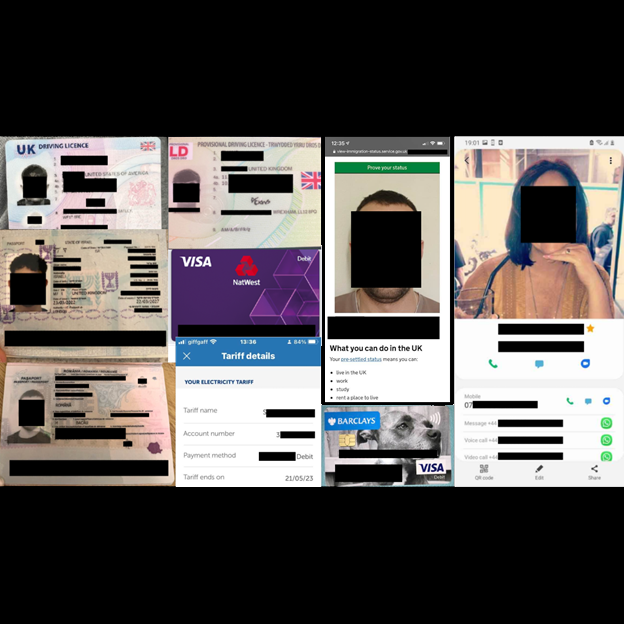
The most concerning images I saw were uploaded by users and contained highly sensitive information. Among the sample of pictures I reviewed there were a few sensitive documents like passports, credit cards, and utility bills that should be kept confidential. It is not clear how many images contained sensitive data or if these images were from the online member portal or the Total Fitness mobile app.
I immediately sent a responsible disclosure notice to Total Fitness, and the database was closed nearly a week later. It is not clear how long the database was publicly accessible or if anyone else gained access. Only an internal forensic audit would determine the timeline and any suspicious activity. I received a detailed reply regarding my discovery that indicated Total Fitness is conducting a full audit of all member images. “We are a members-only club and as part of our joining and access control processes we ask our members to provide a photo of themselves. This protects their membership from being used by someone else and helps us to identify members should we need to locate them in one of our facilities. We are communicating to all members whose images we have identified, and such images have been removed. We have also notified the ICO and will work with them on any enquiries they have on the matter”. In my opinion it shows professionalism and responsibility when an organization has a data incident and takes proper steps to address the issue publicly and to notify potentially affected individuals.
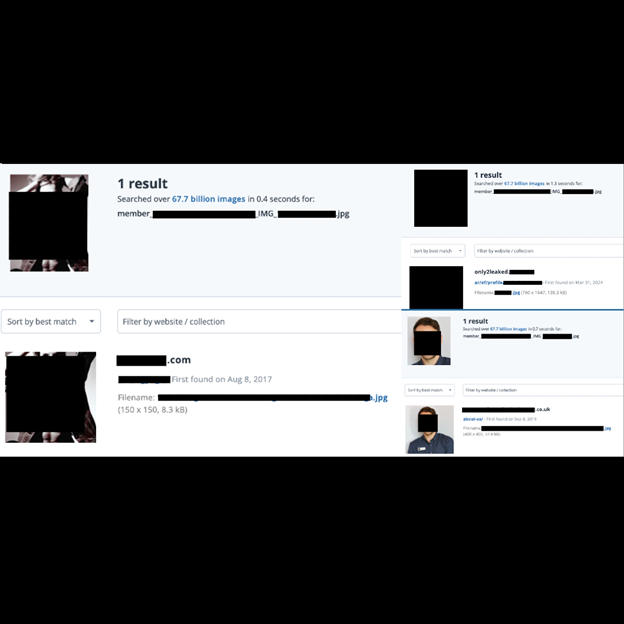
Now that artificial intelligence (AI) and facial recognition tech are practically available to anyone, finding the identity of someone based on a picture is the new normal. In an effort to ascertain the potential risks associated with the breach, I randomly selected a limited sample of images from the database and ran them through an open-source reverse image search tool. I was able to easily identify several members from their profile pictures alone. For example using such tools led me to a member’s Only Fans content disclosing more PII.
This raises privacy concerns regarding how companies in general collect images of members or customers, how they are stored, how long they are kept, and who has access to them. Many people choose to stay private online and do not publicly share images of themselves, their friends, families, or children. Nearly all social media accounts offer users the ability to have a private profile and have strict control over who can access their content.
Total Fitness UK offers member applications on both Google Play Store and Apple’s App Store. The application has over 50,000 downloads on Google’s store alone. According to their LinkedIn page: “Total Fitness is a leading health club brand in the North of England and Wales. Our 15 large health clubs offer many ways of working out; extensive gym floors, over 70 classes a week, impressive swimming pools, expert personal trainers, alongside supporting digital content- allowing our members to continue their fitness journey at home”.
Potential Risks of Impersonation and Blackmail
In the modern age of technology, even an image of your face can raise serious privacy concerns. There are numerous potential risks associated with exposed images, especially when combined with additional ancillary information such as fitness club memberships or other identifiers. The potential risks of AI raise the stakes. Hypothetically, the worst case scenario would be if criminals used the exposed images for impersonation, fraud, blackmail, or other nefarious purposes. I am not saying that members or employees of Total Fitness are at risk, I am only providing a few real-world potential threats that businesses and individuals should be aware of.
There have been several well-known incidents where cybercriminals used AI to create deepfake images and videos to defraud both businesses and individuals. The easy access to this new and emerging AI technology makes it possible for criminals with minimal technical expertise to create exceedingly convincing images or videos and use them for a wide range of malicious activities. For instance, extortion and blackmail attempts using deepfake technology have also been on the rise. Criminals can use images of individuals to create compromising or sexually explicit content involving the victim’s likeness and threaten to release it unless a ransom is paid. False images or videos can cause serious harm to the victim’s reputation, which can be particularly damaging for regular citizens who often don’t know how to handle the situation — especially so when the victims are young. In late April 2024, the UK’s National Crime Agency (NCA) issued an urgent warning about the rise in financial sextortion schemes targeting underage children. Many parents choose to not post images of their children online to protect their privacy and prevent the potential misuse of the child’s image and likeness.
In response to these rising threats, changes in legislation have been pushed forward. Under the Online Safety Act that was passed in 2023, sharing deepfakes was made illegal. As of 2024, there is an amendment to the Criminal Justice Bill making its way through Parliament in England and Wales. The bill aims to take it a step further by stating that the creation of sexually explicit "deepfake" images will be made a criminal offense in England and Wales, even if the image is not publically shared.
Another growing concern is criminals using stolen images to impersonate victims on dating websites or social media, conducting romance scams or “catfishing” for financial gain. Using someone's image identity for fraudulent activities can be traumatic for both the victim and the unsuspecting individuals who interact with the impostor. When someone has their identity used by criminals to scam others there is also a risk of legal problems and other potential dangers which may extend beyond reputation damage.
This is a personal issue for me. I recently received several messages from people that I do not know informing me that my information and pictures were being used to contact multiple women in an attempted romance scam. I have no idea why they chose me when they could have probably had a better success rate using pictures of Brad Pitt or Jeremy Clarkson, but luckily, as a public person in my role as a cyber security researcher, I am easy to contact. When the potential victims became suspicious, they reached out to me directly using an official channel, and I confirmed that I was being impersonated. I know firsthand that knowing someone is attempting to use your identity and images to harm others can be quite upsetting. This is why awareness is an important first step to protecting digital identities online.
What Can You Do if Your Image is Used Without Your Consent?
If a person discovers their picture has been stolen and used by cyber criminals to make deepfakes or impersonate them, I recommend taking immediate action to mitigate the damage and prevent further criminal activity. Here are my recommendations:
- Report the misuse to the website, social media platform, or applications where the impersonation or deepfake is being posted or used.
- Contact local law enforcement to officially document any unauthorized use of your images or videos. Having a police report on record could prevent serious legal problems in the future if, for example, the impersonator were to conduct criminal activities under your name.
- Document all evidence, including website addresses, fake accounts, communication, or any relevant details related to the impersonation or deepfake content. As a potential victim, it’s a good idea to be proactive and have this information at hand in case you need it down the line.
- Inform your friends, family members, or business contacts that someone is using your images or identity. If friends and associates are aware of the situation, they can avoid being scammed by the impostor.
- Use the advanced privacy settings in social media accounts to restrict access to your photos and personal information. Adding a watermark to images with a name or logo can help deter misuse because they can easily be identified or traced back to a real person.
- Run reverse image searches. Doing this regularly can help identify any unauthorized use of your images and limit the extent to which criminals misuse your information freely.
I imply no wrongdoing by Total Fitness UK, LTD, nor do I claim that member data was or is presently at imminent risk. The hypothetical scenarios presented are for educational purposes. I am not saying or implying members of Total Fitness fitness clubs are at risk of having their pictures being used in the creation of deepfake content or impersonation attempts.
As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots for verification purposes. The open source reverse image search tool does not retain search history, and there is no risk associated with the terms and conditions of the service. It is not known how long the database was publicly accessible; only an internal forensic investigation conducted by Total Fitness UK, LTD would be able to identify this information and any potential suspicious activity related to the breach. I publish my findings to raise awareness on issues of data security and privacy.






Please, comment on how to improve this article. Your feedback matters!