Nearly 39 Million Records Were Exposed Online by Legal Services and Technology Company

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password-protected database that contained 38.6 million records belonging to Rapid Legal — a legal support services company that offers court filing, process serving, and document retrieval services for law firms, legal departments, and self-represented litigants. The database contained court documents, service agreements, and payment information (all showing partial credit card details and PII).
The non-password-protected database contained 38TB of data and totaled 38,648,733 records. These included a wide range of legal documents, court filings, and other information that should not have been publicly exposed. The documents and name of the database indicated they belonged to California-based legal services provider Rapid Legal. Upon further investigation, I found references and links to an additional storage repository. It was listed as Legal Connect, and it contained 89,745 records with a total size of 249.9 GB. Based on a public web search, both companies appear to share the same corporate leadership and seem to be connected. Legal Connect is presented as the back-end technology provider while Rapid Legal provides filing services to customers and partner affiliates. I immediately sent a responsible disclosure notice to both Rapid Legal and Legal Connect, and both databases were secured from public access the same day. It is not clear how long the data was exposed or if anyone else may have had access. Only an internal forensic audit could identify this information or any suspicious activity within the cloud storage environment. I did not receive any response from either Rapid Legal or Legal Connect by the time of publication.
The documents ranged from 2009 to 2024 and were segregated by year, month, and day. In the folders, there were case documents, filed documents, notices, receipts, declarations, exhibit evidence, judgements, and other relevant case files that could potentially contain information that may have not been intended to be public. According to their website, the service has allowed more than 32,000 law firms to file or transmit over 7 million orders and 11 million legal documents both to and from a wide variety of court systems. In the United States, most court documents are considered public records; however, even in publicly accessible court documents, some details remain inaccessible and will not be publicly available. Federal regulations mandate that individuals submitting documents to a federal court must redact specific personal information to protect privacy. This includes social security or taxpayer identification numbers, birth dates, the names of minors, financial account details, and, in criminal cases, residential addresses.
According to a 2023 press release, the company planned a “national expansion of its LegalConnect platform, with California and Texas immediately available for eFiling, service of process, and other court services. By the first half of 2024, the LegalConnect platform will be available in a dozen eFiling states including Illinois, New York, and Florida. LegalConnect is the leading eFiling and litigation support services platform for white-labeled service providers and legal technology companies looking to provide eFiling, service of process, and other court services for their law firm customers”.
Potential Security Risks
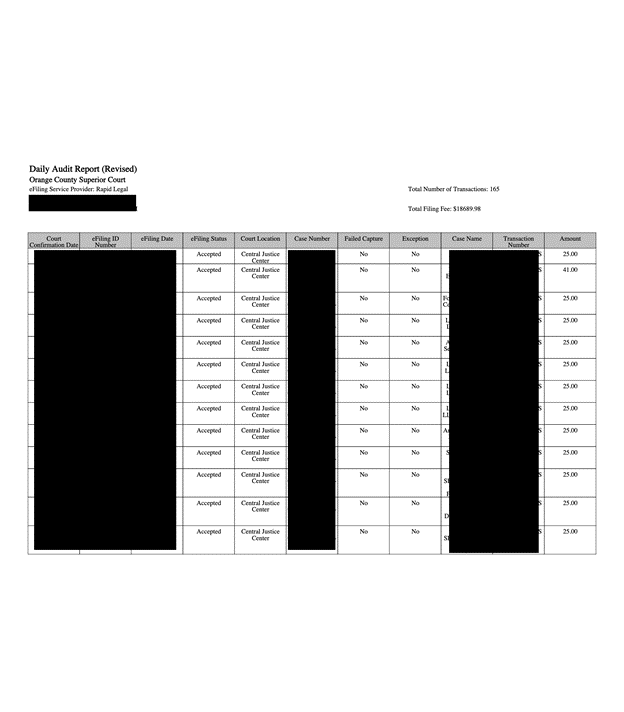
The most concerning documents were in a folder named “Payments”, which contained 737,389 files in.jsn format. The JSON or JavaScript Object Notation file stores data in a structured, easy-to-read text format. In the context of logging online payments, the.jsn files are used to record and organize transaction details such as payment amounts, timestamps, payer information, and status updates. These files are used for simplifying data management and retrieval, but should not be publicly accessible. Each file could be opened using only an internet browser to view the publicly accessible url address — no specialized software required.
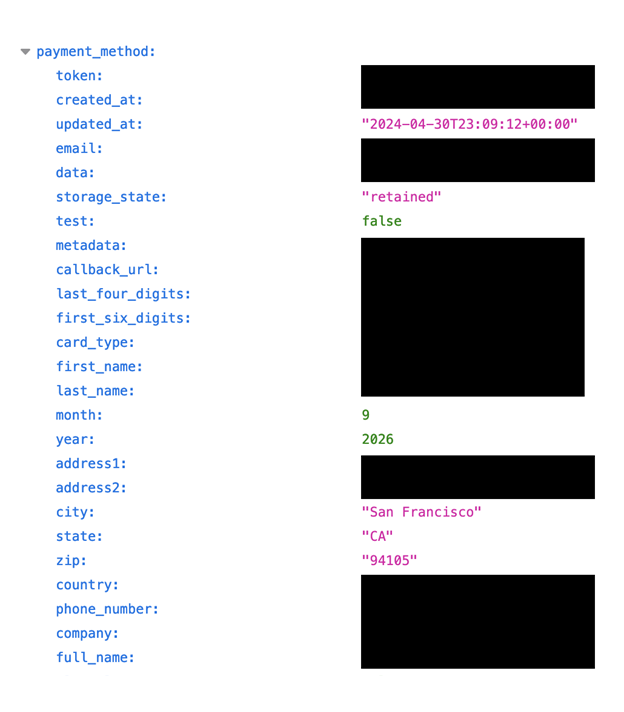
The payment records included names, addresses, card type, partial credit card numbers, and more. While nearly all of the records I saw contained the last four digits, there were some that indicated the first six digits and the last four digits of the card. This means that, in some cases, 10 out of 16 numbers were exposed. Although this alone is not sufficient for completing transactions, this information could potentially be combined with other personal data to facilitate fraud or targeted phishing attacks. Some records also contained merchant tokens, gateway data, and issuer authorization codes that could potentially represent additional security concerns. I am not saying that customer payment data was ever at risk or that there is any imminent threat of fraudulent activity. I am only stating facts regarding what I saw in a limited sample of records when I was trying to identify the owner of the data and responsibly report the exposure so the database could be secured from public access.
I also saw numerous.pfx files with what appeared to be server names or possibly the names of partner services using Legal Connect’s technology. These.pfx files can sometimes contain private keys and certificates that are used in secure or encrypted communications. Hypothetically, cyber criminals could use private keys or certificates to decrypt sensitive data, impersonate the real certificate owner, or — in a worse case scenario — launch man-in-the-middle attacks to intercept encrypted communications. It should be noted that I did not analyze or view these files as I only access data which is strictly necessary to facilitate responsible disclosure, so I cannot confirm or deny what the files contained. I am only providing a hypothetical risk scenario of exposed private keys and certificates. Any organization that stores such files must take every possible step to ensure proper security measures are taken, such as implementing access controls and secure storage practices to protect.pfx files from public access. I would recommend segmenting private keys and certificates and avoid storing them in the same database if possible.
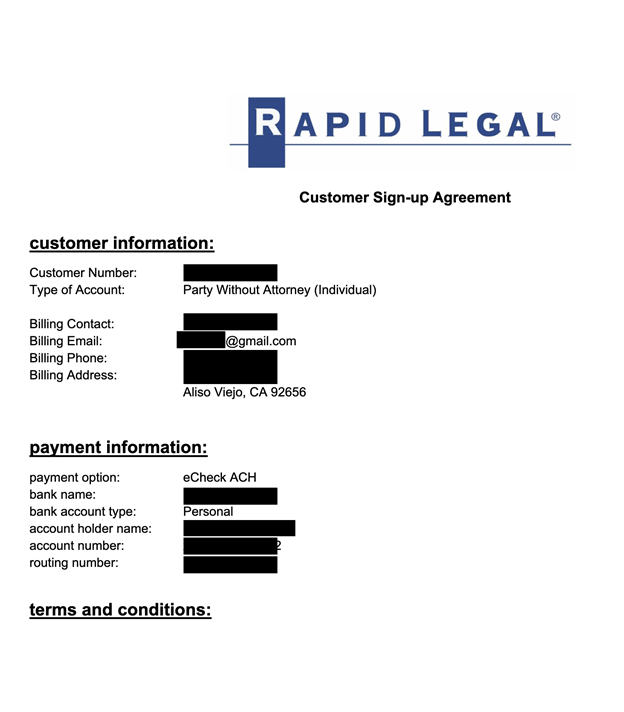
The database also contained an estimated 146,000 signed customer service agreements that included contact and partial payment information or bank account data. The exposure of thousands of email addresses, home or business addresses, phone numbers, case details, and other information raises numerous potential privacy concerns. Any exposure of contact information combined with PII could be potentially used for targeted phishing attacks, harassment, malware and spam emails, or other fraudulent activities. As a hypothetical example, criminals could contact individuals and reference court cases, document details, and known payment information in an attempt to use social engineering tactics to get them to reveal additional personal or financial information. I am not saying that customers or users of the services are at risk of this type of activity. I am only providing a real-world scenario of a common tactic used by criminals for awareness and educational purposes.
Legal filing service providers such as Rapid Legal and Legal Connect play a crucial role in the legal industry by offering electronic submission of legal documents to courts and other relevant entities. These companies offer a variety of services, including e-filing, document management, and process serving, which help legal professionals streamline their workflows and ensure timely submissions. Legal filing services handle a wide range of potentially sensitive information that is necessary for court cases. These could include court filings, motions, and evidence that may contain confidential information. Another potential concern would be the confidentiality between the law firms and the clients they represent. According to the California State Bar, “in the legal realm, confidentiality refers to ‘the relation between lawyer and client which guarantees any information shared by the client is treated as private and as such cannot be divulged to third parties without the client's consent.’ This is known as the attorney-client privilege”.
In the cyber security world, we always say it’s not if there will be a breach, but when there will be a breach. No matter what the cause, data incidents do happen, and it is important to learn from those mistakes and be more resilient in our cyber security posture. These lessons can be learned by companies in any industry and members of the cyber security community. By implementing basic security measures and taking proactive risk-management strategies, companies can be prepared at every step of the way. Having an end-to-end strategy (from prevention, to identification, mitigation, response, and recovery) makes a major difference in the severity of an incident.
I recommend the following steps as a minimum requirement to any organization that collects and stores potentially sensitive documents in cloud storage databases.
- Encryption: Protect your sensitive data against unauthorized access by making the information inaccessible and highly unlikely to be decrypted. In the unfortunate event of a data breach or a malicious attack, encrypted data adds an additional layer of protection and greatly reduces the chances of information falling into the wrong hands.
- Access Controls: Limit data access to authorized personnel only and ensure that access is restricted to an as-needed basis and not left open to everyone. Knowing who in your organization has access to sensitive documents and internal information can help prevent an insider data leak.
- Regular Audits: Vulnerability assessments are the best defense to proactively identify and address potential weaknesses before they become a critical issue or can be exploited by malicious actors. This includes misconfigurations, firewall errors, patch management, and other vulnerabilities.
- Incident Response Planning: Having a plan in place can eliminate mistakes and confusion during and after a data incident. With proper incident response planning, companies can quickly and effectively follow a step-by-step plan that details who will do what. This will also help convey the correct message to stakeholders, customers, authorities, and the general public.
- Education: In my decade of experience as a security researcher, I have seen countless data incidents that could have been prevented by training employees and users on data security best practices. In any organization, employees, customers, or users are the first line of defense to prevent inadvertent data exposure, report suspicious activity, and vulnerabilities.
I imply no wrongdoing by Rapid Legal or Legal Connect, nor do I claim that any records, documents, or confidentiality agreements were ever at risk. It is not known how long the databases were exposed and publicly accessible, or if anyone else accessed them. It is also not known if the exposure was reported to the authorities or potentially affected individuals as required by California law and the California Consumer Privacy Act (CCPA). As an ethical cyber security researcher, I do not download or extract the data I discover; I only take a small number of redacted screenshots for validation and notification purposes. I publish my findings to raise awareness of important cyber security issues and promote best practices in terms of data protection.






Please, comment on how to improve this article. Your feedback matters!