2.7 Billion Records Exposed in IoT Devices Data Breach

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password-protected database that contained nearly 2.7 billion records belonging to Mars Hydro — a China-based company offering IoT grow lights and software applications that allow users worldwide to control devices, timers, and settings remotely.
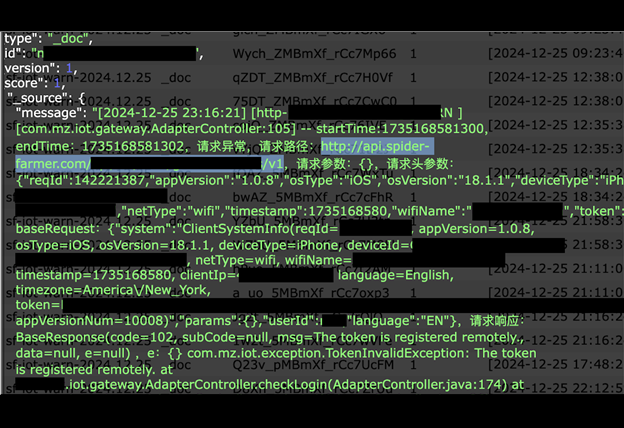
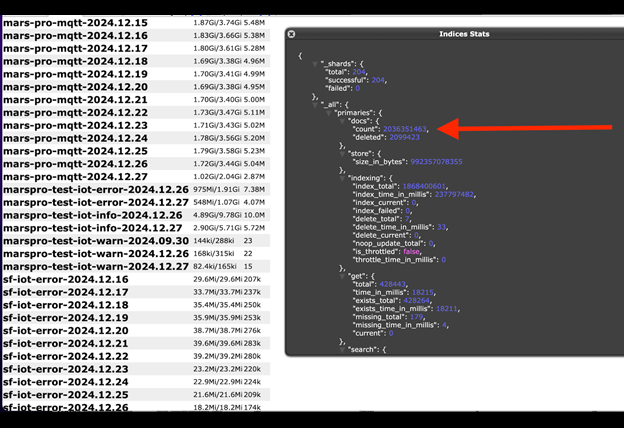
The publicly exposed database was not password-protected or encrypted. It contained 2,734,819,501 records with a total size of 1.17 TB. There were folders inside the database indicating logging, monitoring, and error records for IoT (Internet of Things) devices sold worldwide. In a limited sampling of the exposed documents, I saw 13 folders with over 100 million records containing SSID (service set identifier), more commonly known as your Wi-Fi network name. Apart from these Wi-Fi network names, the records also included the Wi-Fi network's passwords, IP addresses, device ID numbers, and much more. These appeared to be details of connected IoT devices as well as references to the control device (smartphone) running the IoT software application, indicating details about the operating systems (e.g., iOS, Android).
Upon further research, the records indicated they belonged to a California-registered company called LG-LED SOLUTIONS LIMITED. The exposed records also contained API details and URL links to LG-LED SOLUTIONS, Mars Hydro, and Spider Farmer. These companies manufacture and sell grow lights, fans, and cooling systems for agricultural purposes. Many of the records I saw were labeled as “Mars-pro-iot-error” or “SF-iot-error”. In addition to the SSID credentials, the error logs included potentially sensitive information like tokens, app version, device type, and IP addresses. According to a listing on the ecommerce website Made in China, Mars Hydro is a LED grow light manufacturer that develops, produces, and manufactures products in Shenzhen, China. The company has warehouses in the United Kingdom, United States, and Australia.
I immediately sent a responsible disclosure notice to LG-LED SOLUTIONS and Mars Hydro. Within hours the database was restricted from public access and no longer publicly accessible. Although I did not receive any reply to my initial responsible disclosure notification, in a follow-up email to Mars Pro’s customer support, I inquired whether the company and the app are connected or whether the application was developed by a third party. I received a reply stating: “This app is the official product of Mars Hydro”.
Although I received confirmation that the app is an official product, it is not currently known if the database was owned and managed directly by LG-LED SOLUTIONS or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
The Mars Pro application is available for both iOS and Android devices and offered in English, French, German, and Chinese. According to the Mars Hydro data privacy notices on both Google Play and Apple’s App store that the app collects no user data, so it is unclear how the log records contain details of connectivity and credentials. One possibility could be that they are captured and recorded by the IoT devices once they are connected to the user’s local network. No matter how this information was collected, it raises potential concerns over IoT device security and network privacy. The Mars Pro app’s data privacy policy links to the LG-LED SOLUTIONS as well as the Android application.apk file on Mars Hydro’s official website.
IoT security (or lack of security) is a serious concern. Many devices were not designed with data protection as a primary focus or with long-term patch management solutions. In a threat report published by Palo Alto Networks, researchers found that, across all industries, an estimated 57% of IoT devices were considered highly vulnerable — and even more shocking is that 98% of data transmitted by these devices is unencrypted. The study also found that 83% of connected devices run unsupported or outdated operating systems, leaving them open to attacks using known vulnerabilities. Many IoT devices have limited processing capabilities that limit the ability to implement additional security features, encryption tools, or install important security or firmware updates.
Another concern is that many IoT devices use default credentials. This can add another layer of vulnerability simply because the average users do not have the technical skills needed to change the default passwords to something more complex. Worst of all, some IoT devices have no authentication — once they are connected to the network, they are completely vulnerable to attacks.
Finally, where does all of this data go? When user data is stored in a centralized cloud server, it creates a single point of failure that could potentially expose massive amounts of user and device data in the event of a data breach.
Users of apps and devices have become more aware of the potential risks in the wake of the recent news surrounding TikTok. The app’s ability to track users’ behaviors and access metadata, device identifiers, and details about Wi-Fi networks have raised privacy and possible national security risks. There is a real concern that user data could be accessed by foreign governments under national security laws and used for surveillance or intelligence gathering.
Based on the internal logs that I saw in this exposed database, the Mars Pro connected devices and application also gather a wealth of information. The hypothetical worst case scenario would be if this information was used for surveillance, man-in-the-middle (MITM) attacks, mapping of networks and critical infrastructure, or other potential misuse. I am not stating nor implying that these companies are engaged in any of these activities or that their users are at risk. I am not claiming that just because an application was made in China or has Chinese ownership there is an imminent risk. I am only highlighting what data is collected and how it could be a potential security risk in the wrong hands. In addition to cyber risks, there is a risk in real life that a malicious actor could impersonate the user and manipulate devices such as lights, fans, or temperature controls, potentially causing harm to crops. I only provide real-world risk scenarios for educational purposes based on data that is publicly accessible.
There are documented cases of remote network intrusions that highlight the risks of using unsecured Wi-Fi as an entry point. In November 2024, it was reported that Russian military hackers from the GRU's Unit 26165, also known as APT28 or Fancy Bear, used a little-known method called "nearest neighbor attack" to breach an organization based in Washington, D.C. that was focused on supporting Ukraine. The hackers compromised a nearby organization's network that was simply in range of the target's Wi-Fi and then gained access to the victim's network. This method allowed the attackers to remotely exploit Wi-Fi networks from thousands of miles away.
The “nearest neighbor attack” method provides a clear understanding of how cybercriminals and nationstates could potentially attack targets by identifying a weak link and simply jumping to nearby networks. The fact that these nearby networks are usually known or trusted makes the detection of this type of attack much more difficult if they are not actively monitored for suspicious activity.
There are serious potential risks of exposed Wi-Fi SSID and credentials. In this discovery, I saw a massive amount of exposed SSID names, passwords, MAC addresses, and user IP addresses that could potentially allow unauthorized remote access to the device's Wi-Fi network. Theoretically, using the exposed credentials, an attacker could connect to the network and compromise other devices or attempt a nearest neighbor attack. Once connected to the device, it could be possible to intercept data or harvest packet sniffing data. Packet sniffing refers to data packets that are transmitted between connected devices and the network; these packets are captured and analyzed to gather information that can also be used to steal additional login credentials, identify sensitive files, or other confidential data. Another potential risk would be to target the device directly, install malware, custom exploits to known vulnerabilities in the firmware version, or hijack the device to be used in a botnet for DDoS attacks.
To mitigate these risks, IoT device makers and app developers should avoid logging sensitive information like Wi-Fi passwords in plain text. Error and monitoring logs provide important information and are often not treated as sensitive data. This is a serious issue when these logs also contain ancillary information such as device identifiers, authorization credentials or other customer information. Potentially sensitive data should always be encrypted or, at a minimum, the identifiable device information should be replaced with hashed or tokenized values.
Additionally, internal cloud storage repositories should be restricted to not allow public access and trigger an alert when an unauthorized access is detected. Device makers should also have a long term plan on how to maintain security updates and patch management. Finally, they should also conduct regular audits and penetration tests to identify vulnerabilities before they are exploited or result in a data breach.
I imply no wrongdoing by LG-LED SOLUTIONS, Spider Farmer, Mars Hydro, or any of its contractors or affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.





Please, comment on how to improve this article. Your feedback matters!