US and UK Armed Forces Dating & Social Networking Service Exposed Over 1 Million Records Online

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password-protected database that contained more than 1.1 million records belonging to Conduitor Limited (trading as Forces Penpals) — a service that offers dating services, and social networking for military members and their supporters.
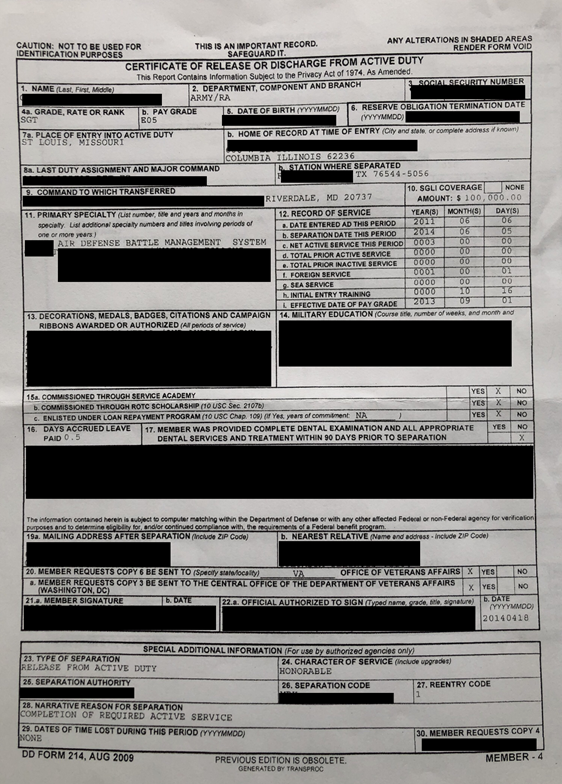
The publicly exposed database was not password-protected or encrypted. It contained a total of 1,187,296 documents. In a limited sampling, a majority of the documents I saw were user images, while others were photos of potentially sensitive proof of service documents. These contained full names (first, last, and middle), mailing addresses, SSN (US), National Insurance Numbers, and Service Numbers (UK). These documents also listed rank, branch of the service, dates, locations, and other information that should not be publicly accessible.
Upon further research, I identified that the records belonged to Forces Penpals, a dating service and social networking community for military service members and their supporters. I immediately sent a responsible disclosure notice, and public access was restricted the following day. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I received a response from Forces Penpals after my disclosure notice stating: “Thank you for contacting us. It is much appreciated. Looks like there was a coding error where the documents were going to the wrong bucket and directory listing was turned on for debugging and never turned off. The photos are public anyway so that's not an issue, but the documents certainly should not be public”. It is not known if the database was owned and managed by Forces Penpals directly or via a third-party contractor.
According to their website, the service operates social networking and support for members of the US and UK armed forces. It claims to have over 290,000 military and civilian users. Founded in 2002, Forces Penpals allowed UK citizens to write to soldiers on active duty in Iraq or Afghanistan. In a 2018 interview, the director of Forces Penpals said “It was specifically about pen pals in the beginning with a little bit of a dating element. It was originally a morale-boosting support service for the armed forces, and a way for us to engage civilians with the military community.” It is unknown if the exposed documents came from the website and forum or from the Forces Penpals dating app, which is available for both iOS or Android devices.
Many individuals choose to remain private online and do not share their image or likeness when using apps or social media. Exposing user images combined with proof of service documents could potentially create significant security and privacy risks. Hypothetically, these documents could contain enough personal information to be a potential identity theft risk, allowing malicious actors to impersonate individuals for fraudulent activities or possible financial crimes. The more information that criminals have on potential targets, the higher the success rate of phishing attacks and social engineering schemes that could deceive people into revealing further confidential data.
For active duty military personnel or those with security clearances, the exposure of their rank, locations, or other details about their service could have potential national security implications. In October 2024, Microsoft and authorities in the United States reported that a hacking group linked to Russian intelligence attempted to infiltrate the systems of numerous Western think tanks, journalists, and former military and intelligence personnel. I am not saying that Forces Penpals’s users were ever at risk of identity theft, phishing, social engineering, or other potential criminal activities. I am only providing a real-world threat scenario for educational purposes.
I recommend companies that provide dating apps or social networking services take additional measures to secure the data they collect and store. This includes:
- Implementing enhanced access controls and authentication requirements for any cloud storage databases where sensitive information is stored.
- Segmenting sensitive documents in a separate location, so that not everything is stored in one place. This can minimize the potential risks of a data exposure and restrict unauthorized access to the most sensitive information that the organization must protect.
- Conducting regular security audits and penetration testing can help identify open ports, misconfigured firewall settings or other vulnerabilities that could result in a data breach.
- Having an incident response plan in place is also important. No organization intentionally exposes potentially sensitive user data online, but having a plan in place is a proactive way to mitigate damage and notify affected users and stakeholders in the event of a data breach.
- Installing a direct communication channel for data incidents helps ensure that responsible disclosure notices reach the correct people or team fast. When it comes to exposed data, time is a critical factor.
I imply no wrongdoing by Conduitor Limited operating as Forces Penpals, and I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by Forces Penpals or the organization that managed the database would be able to identify this information along with any potential suspicious activity related to the breach. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.






Please, comment on how to improve this article. Your feedback matters!