4.6 Million Voter and Election Documents Exposed Online by Technology Contractor

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to VpnMentor about the discovery of 13 non-password-protected databases that contained 4.6 million documents, including voter records, ballots, multiple lists, and election-related records.
I recently discovered a non-password-protected database that contained a collection of different documents including voting records, ballot templates, voter registrations, and numerous lists. All of the physical addresses appeared to be from a single county in the state of Illinois. Upon further analysis, in my attempt to identify the owner of the dataset, I suspected there could be more counties inadvertently exposing voter and election records. So, I took the known database name format and simply replaced the county name. This identified a total of 13 open and publicly accessible databases and an additional 15 databases that exist but are not publicly accessible.
According to multiple news articles and freedom of information act (FOIA) documents posted online, these counties have contracts with a company called Platinum Technology Resource. This company offers a variety of services, ranging from ballot printing to election management and voter registration software. The counties indicated in the exposed databases also offer a voter information portal that redirects to a domain indicating “Platinum vrms” (I can only speculate this stands for “voter record management system"). To verify this, I made phone calls to several county clerks’ offices and was informed that only one vendor (Platinum Technology Resource) manages their voter and election data, and it is known as Platinum Elections Services.
Once I was reasonably sure who managed the database, I sent a responsible disclosure notice to Platinum Technology Resource. However, in a follow up review the next day, I noticed the database was still publicly accessible. In an attempt to identify other contact details, I found several additional FOIA documents indicating an Illinois-based technology company called Magenium is responsible for the technical support of Platinum Elections Services. During a phone call to Magenium, I was told that they are a partner of Platinum Technology Resource and that they would look into my findings. A day after sending Magenium a responsible disclosure notice, the databases were restricted. In a phone call a representative from Magenium confirmed their closure of the databases and that Platinum Election Services was aware of the situation. It is not known how long the documents were exposed or if anyone else gained access. Only an internal forensic audit could identify additional access or suspicious activity.
According to their website, “Platinum Technology Resource has been providing election technology and services to counties throughout the State of Illinois for over thirty-five (35) years. Through voter registration, election-day support, ballot management, tabulation, and election management software, we have incorporated lessons learned into our product PlatinumVR”.
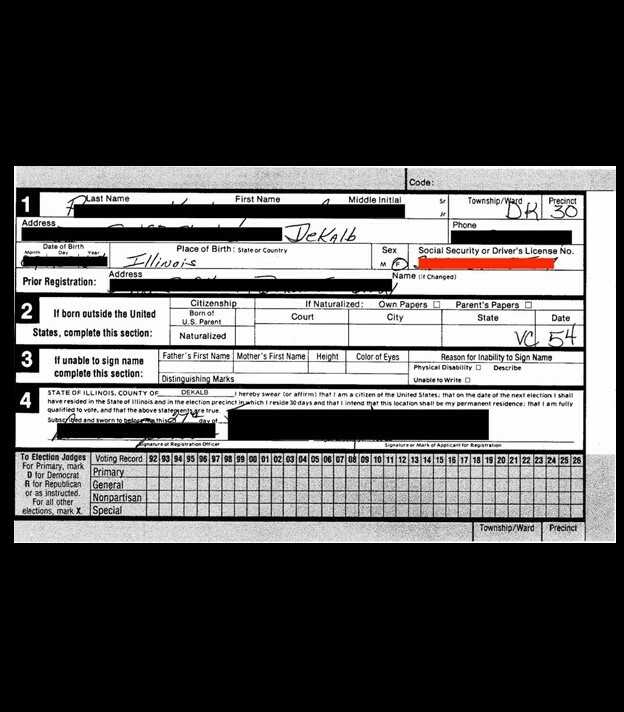
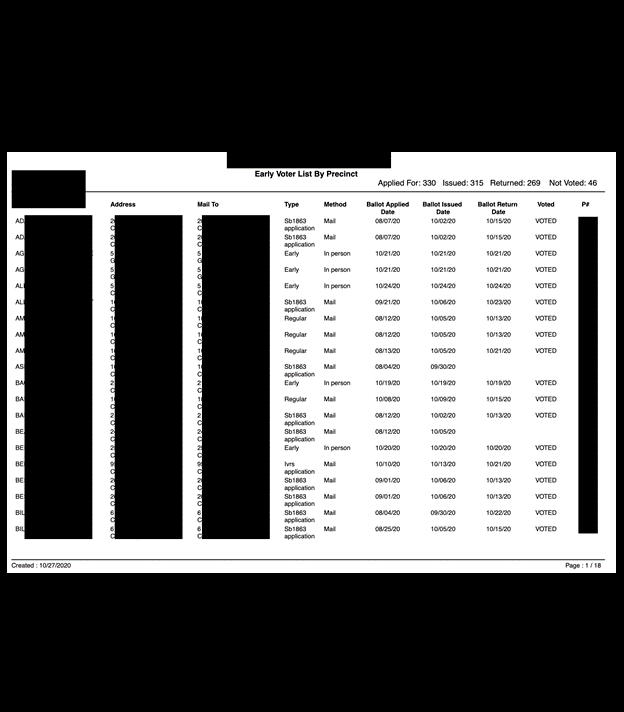
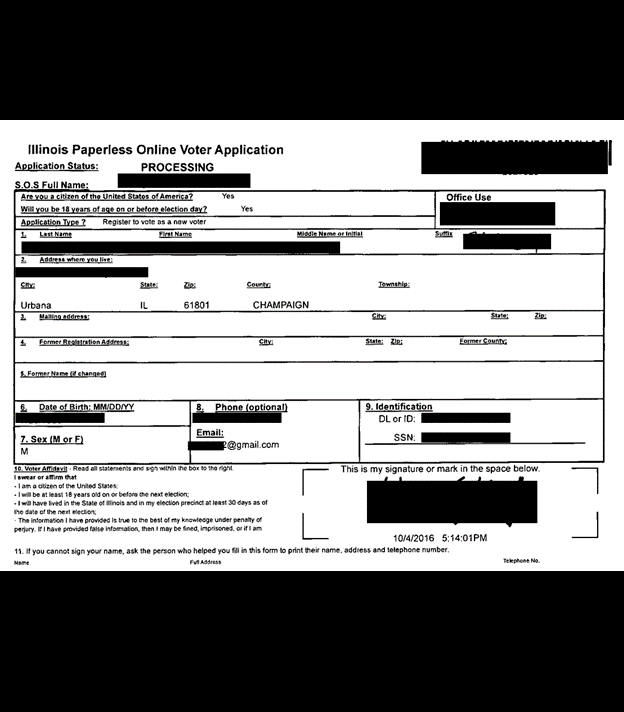
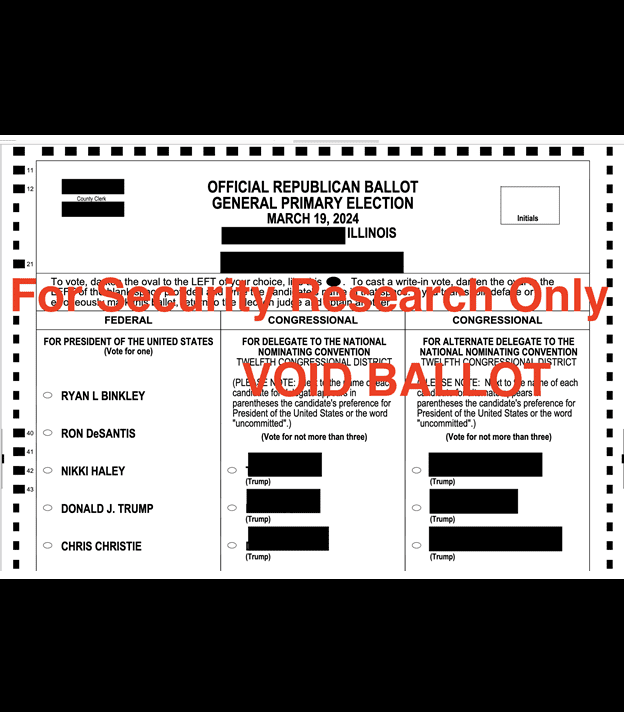
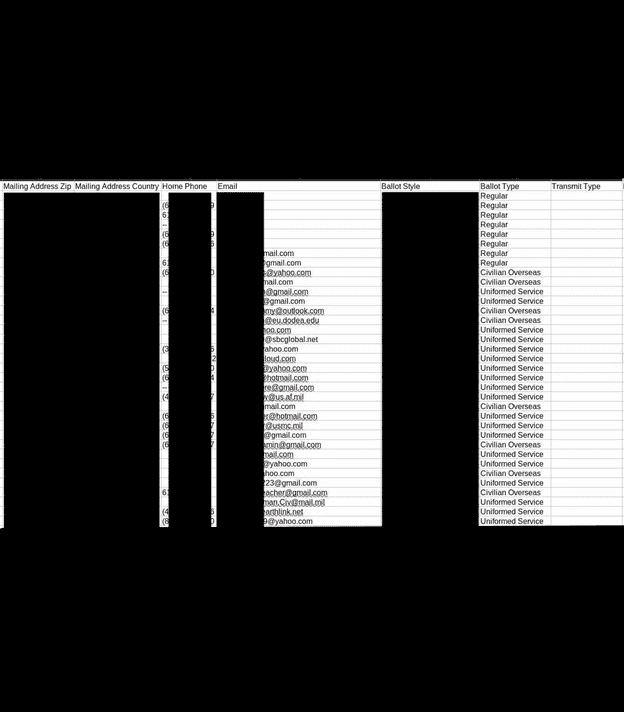
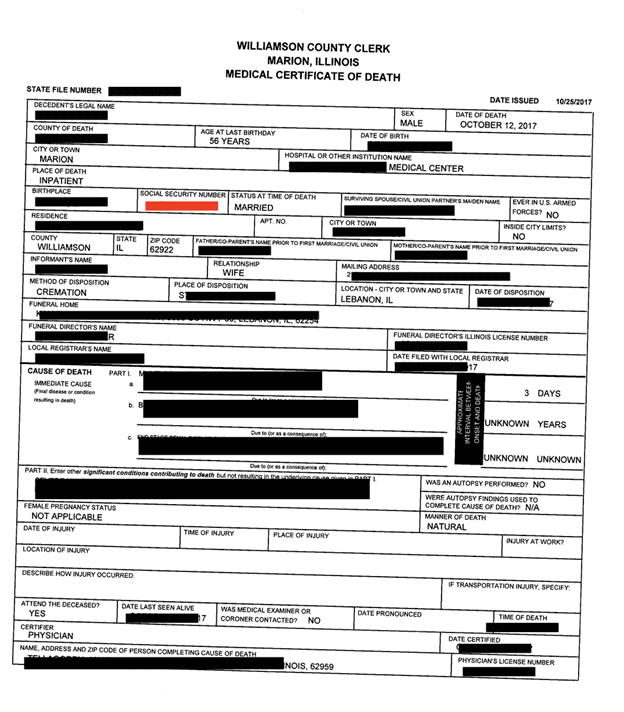
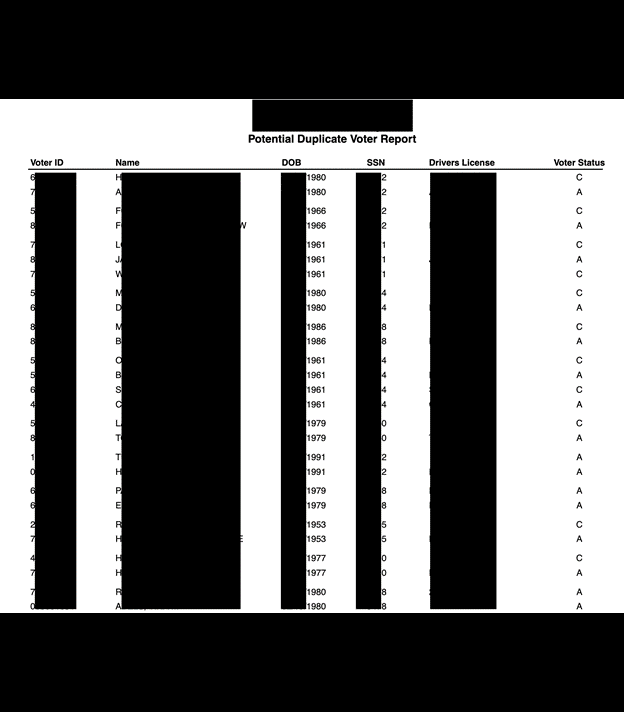
The exposed databases contained.csv documents with lists of available or active voters, absentees, early mail-in voting records, and duplicate voters. Other documents marked as “voter records” contained far more potentially sensitive personal information, including full name, physical address, some email addresses, date of birth, SSN (full and partial) or driver’s license number, and historical voting records. The database also contained copies of voter registration applications, death certificates, and records of change of address, jurisdiction, or state. There were also candidate documents (such as statements of candidacy) detailing personal phone number, email address, and home address. These candidate documents also included petitions with voter signatures, addresses, candidate loyalty oath, economic interest, and additional supporting documentation. There were also documents marked as official ballot templates for primaries and general elections.
There are few things in the US as divisive as politics, but everyone can probably agree that data protection and the security of election systems is a necessity. Since 2017, the Department of Homeland Security classifies election infrastructure as critical, acknowledging that the incapacitation or destruction of election systems would have a devastating effect on the country. According to information published by CISA, this includes voter registration databases and associated IT systems used to manage elections (such as the counting, auditing, and displaying of election results, and the post-election reporting to certify and validate results).
It is important to maintain public trust in the electoral process in the United States and democracies around the world. This trust is especially true in the wake of the 2020 election, when the integrity of the process was called into question. As a non-political person, I believe that no matter what your political beliefs are, all citizens should feel that their votes matter. Any assertions that elections are not fair could potentially harm civic engagement and the overall trust in the democratic process.
It is important to maintain public trust in the electoral process in the United States and democracies around the world. This trust is especially true in the wake of the 2020 election, when the integrity of the process was called into question. As a non-political person, I believe that no matter what your political beliefs are, all citizens should feel that their votes matter. Any assertions that elections are not fair could potentially harm civic engagement and the overall trust in the democratic process.
Many reports on social media claim that the names and voter records of deceased individuals were allegedly used to cast votes in past elections, changing the outcome in favor of one candidate or another. In a limited sample of documents I reviewed, I cross-referenced several exposed death records with active voter lists, and I am happy to report none of those names appeared or were included as active voters. Based on the documents I saw, there was nothing to indicate anything suspicious or that the elections in those jurisdictions were not free and fair. Although there were no signs of any wrongdoing, it is crucial to protect elections and voter data from cyber attacks, which may include tampering with documents or using exposed voter information for fraud or misinformation. Concerns about election tampering through a cyber attack could undermine confidence in the accuracy and fairness of election outcomes, and this is why the US government has deemed election data as critical infrastructure.
The potential risk of a coordinated disinformation campaign using voter lists and voter registrations is a serious concern from both outside actors (such as Russia or China) and domestic activists looking to sway political opinions. According to a study conducted by the Pew Research Center in 2020, 75% of American voters believed there would be outside interference in the presidential election. Having PII of voters would potentially allow malicious actors to send them misleading information (about voting dates, locations, or requirements) based on their party affiliation. Another possible risk is voter intimidation, which includes using past voter history to threaten or harass voters.
Another hypothetical concern would be if a criminal used a voter’s information and voter ID number to cast multiple ballots by mail, triggering potential legal problems for the real voter and invalidating their real vote. These tactics could undermine the democratic process in rural areas where a small number of votes can influence the outcome by reducing voter turnout or manipulating local or state election results in favor of a particular candidate or agenda. I am not saying there is an imminent threat of voter fraud or intimidation based on this data exposure, I am only presenting a hypothetical real-world risk scenario.
Exposed PII combined with highly sensitive information (such as Social Security Numbers and driver's license numbers) poses significant risks beyond the political sphere. Criminals could potentially use information intended for voter registration to commit identity theft and various forms of fraud. Many banks, credit card companies, and loan providers require little more than a matching SSN and date of birth. Additionally, the same information could be used to file fraudulent tax returns. According to the IRS, in 2023, over 1 million tax returns were flagged for additional review for potential identity fraud and totaled more than $6 billion in refunds. Identity theft can have severe financial consequences and leave victims with damaged credit or other legal and financial obligations that could take years to overcome.
Additionally, PII exposure can also possibly be used for targeted social engineering attacks on specific individuals, particularly those with significant wealth. Cyber criminals could also impersonate them in an attempt to gain access to additional personal or financial information. I am not saying that these voters or candidates are at risk of identity theft, impersonation, or other forms of fraud. I am only presenting a hypothetical risk to raise awareness and for citizens to stay vigilant to the real-world threats that can accompany any potential exposure of their PII. Knowing the risks and identifying suspicious activity early can help mitigate the damage of any unauthorized or attempted use of an individual's identity or personal information.
I would advise any organization that manages and stores potentially sensitive documents in multiple databases to use unique formats and names that are not easy to guess. In this case, I was able to simply replace the county name to identify other databases. The additional 15 password-protected databases still pose significant possible risks, as they reveal the filepath of where potential voter or election documents may be stored. Hypothetically, cybercriminals could launch brute force attacks to attempt to gain unauthorized access or socially engineer individuals to provide credentials or other internal information. These databases could also be targeted by denial of service attacks (DDoS) to disrupt access during elections and prevent the necessary sharing of information. Voters and election officials alike need access to documents for tracking and validation purposes, and those documents must be stored somewhere. It is important that these storage areas are fully protected at the database level and not just when using a front-facing password-protected dashboard that still exposes the document itself to anyone who knows the URL address.
To secure documents stored in a cloud database that need to be delivered through a dashboard or application, I would recommend using a combination of access controls and encryption. The best way to protect these documents from being publicly exposed by the URL is to use an access token to generate a unique, time-limited access token for authenticated users when they or the system requests the document. The token ensures that only authorized users can access or view the document and limits the amount of time the file or document can be accessible. This can help mitigate security issues related to direct URL access without proper authentication. It should be noted that the databases I saw contained only documents and did not identify the inner workings of how the Platinum Technology Resource voter systems operate. My recommendations are for general advice and educational purposes for any organization that collects, stores, or distributes potentially sensitive information or documents, and are not specific to Platinum Technology Resource, Platinum Elections Services, Magenium, or any of the associated entities or third-party contractors.
As an ethical cyber security researcher, I never download the data I find and only take a limited number of screenshots to validate and responsibly report my findings to the owner of the data. I redact PII and any information that could be deemed as sensitive information. I do not imply any wrongdoing by Platinum Technology Resource, Platinum Elections Services, their partners, or third-party contractors, nor do I claim the information contained in the exposed files or documents was ever at risk. It is not known how long the documents were exposed or if anyone else gained access to the publicly accessible database. I can confirm that from the time of my discovery and reporting until public access was restricted, the duration was approximately 10 days. Determining detailed access information would require an internal forensic audit. As an ethical security researcher, I publish my findings for educational purposes and to promote cyber security and advocate for data protection best practices.



Please, comment on how to improve this article. Your feedback matters!