Online AI Mental Health and Addiction Treatment Provider Exposed Patient Data

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password-protected database that contained thousands of records belonging to Confidant Health — an AI-powered platform offering mental health and addiction treatment. The database contained patient PII, psychosocial assessments including details about mental health or substance abuse, ID cards, health insurance information, and more.
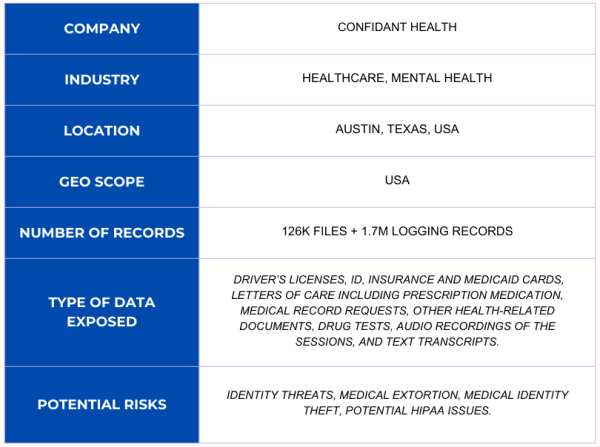
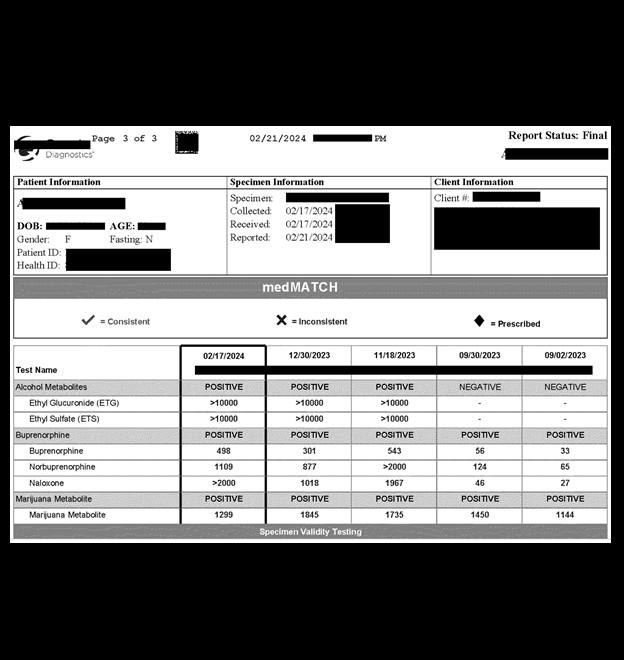
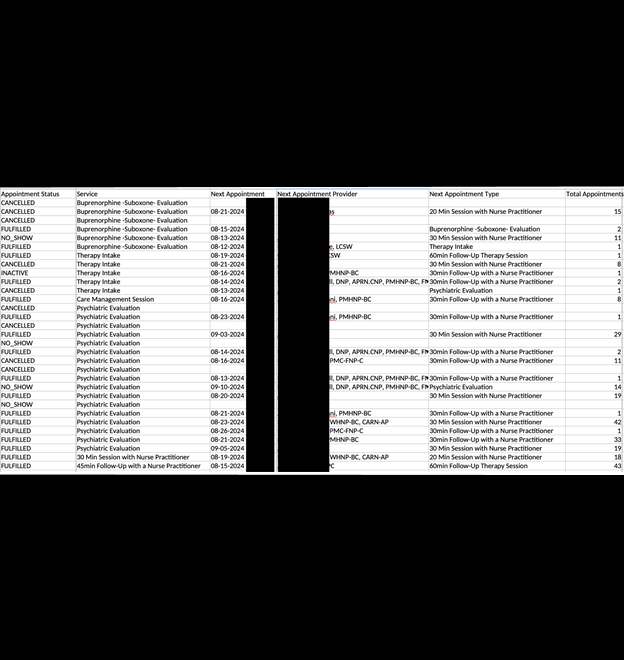
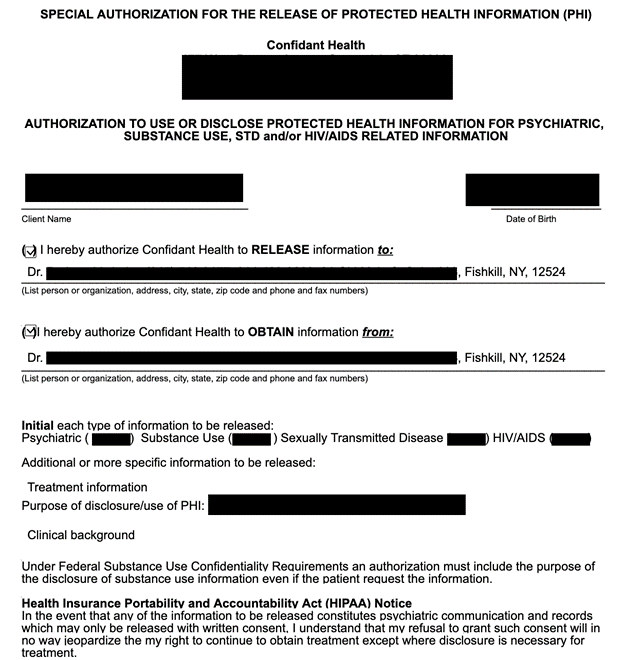
I recently discovered a trove of publicly exposed mental health and substance treatment records. Some of these documents contained the names and PII of the patients, counselors, and medical professionals. The patients’ records contained images of driver’s licenses, ID cards, insurance cards, medicaid cards, letters of care listing prescription medication, and medical record requests or waivers. The database also contained diagnostic drug tests indicating names, addresses, and test results for specific substances.
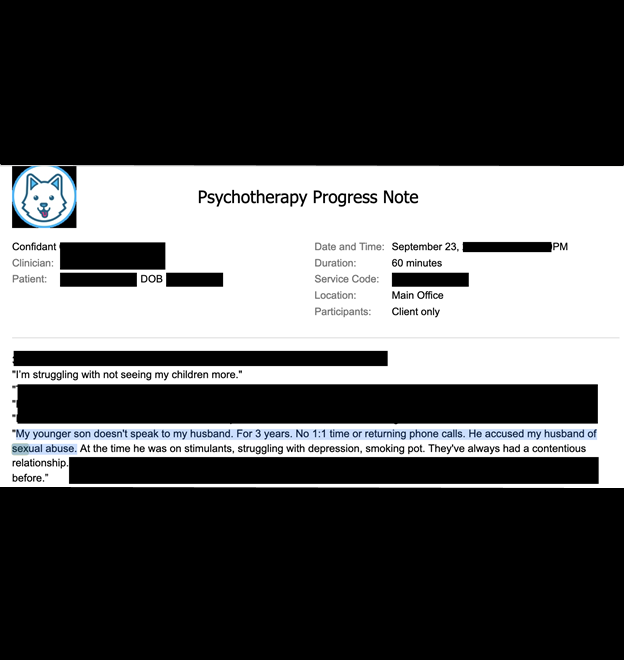
I saw documents indicating psychotherapy intake notes and psychosocial assessments that provided details about mental health or substance abuse, touching upon the patients’ family issues, psychiatric history, trauma history, medical conditions, and additional diagnoses. I also saw references to audio and video recordings of the sessions and text transcripts. These reports are highly detailed and discuss deeply personal family topics, disclosing names of children, parents, partners, and the nature of conflicts or other private issues.
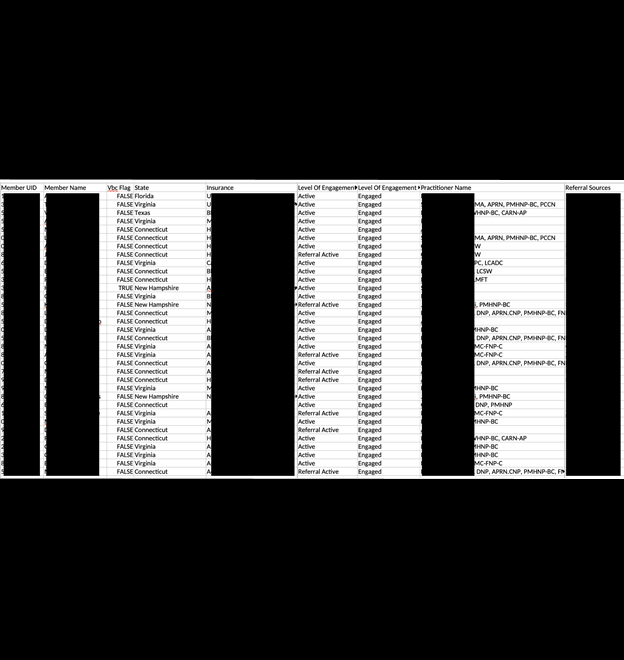
Upon further research, it appeared that the documents belonged to Texas-based Confidant Health. The company provides services to residents of Connecticut, Florida, New Hampshire, Texas, and Virgina. I immediately sent a responsible disclosure notice, and public access to the documents was restricted within hours. I received a reply thanking me for the notification and saying that they would investigate. It is not known how long the documents were exposed or if anyone else may have gained access to the database. Only an internal forensic audit would be able to identify additional access or suspicious activity. It is also not known if the database was managed directly by Confidant Health or a third party.
The database contained 126,276 files (totaling 5.3 TB) and a separate folder held 1,755,571 logging records. The size is likely due to the large audio and video files. It should be noted that it appears not every document in the database was exposed, and that a portion of the files were restricted and not publicly viewable. However, even if the data in these restricted files cannot be viewed, there is a potential risk of malicious actors knowing the file paths and storage locations of additional patient data. As an ethical security researcher, I never bypass any security credentials and identify only publicly accessible data. However, cyber criminals have a range of tools at their disposal including brute force attacks and social engineering attempts that could potentially result in unauthorized access to those protected files and documents. In a random sample I reviewed, the open and publicly accessible files (which I was able to view using only a web browser) contained what could be considered a very serious potential risk to the personal privacy and PII of those individuals.
According to their website, Confidant Health offers a range of services including: alcohol rehab, online suboxone clinic, pre-addiction treatment, addiction treatment, behavior change program, recovery coach, opioid withdrawal management, medication assisted treatment. Confidant Health offers a Telehealth Addiction Recovery application that is available for iOS and Android with over 10,000 downloads on the Google Play Store.
There is a precedent of how online counseling and therapy data could be misused by cyber criminals. In 2021, Wired reported that a mental health startup called Vastaamo provided services with easy-to-use technology and ran the largest network of private mental-health providers in Finland. Hackers had compromised and downloaded their entire client database. Next, the criminals contacted the CEO of Vastaamo and demanded 40 Bitcoin (500k USD in 2020) in ransom or they would leak 100 patient records each day.
After the CEO stopped communicating with the criminals, they began contacting individual patients and demanding they pay a ransom of €200 in Bitcoin within 24 hours or else the extortion fee would increase to over €500 in 48 hours. If the victims failed to pay the ransom, the criminals threatened to publish their private mental health information online. It is not known how many people actually paid the ransom, but the entire Vastaamo database was publicly released and made available on 11 anonymous file-sharing services at the time of Wired’s report.
For both the patients and the company, the incident was a devastating reminder of how criminals can weaponize confidential health data. I am not implying that Confidant Health or their clients are at a similar risk of the same misuse and only use this as a real-world example of how leaked mental health and substance abuse data was used in the past.
Any organization that provides telehealth services and that manages sensitive patient information through a platform or app must take every possible step to protect the data they collect and store. Health records are valued quite highly on the dark web, selling for as much as $1,000 a piece. For comparison, credit card numbers sell for an estimated $5, while Social Security numbers are sold for as low as $1.
Health data alone is highly valuable to criminals, but when it is combined with the patient’s fear over the possible exposure of their sensitive personal mental health data or substance abuse, it could hypothetically increase the risk of successful extortion attempts. In the wrong hands, this information could have far-reaching and devastating consequences.
In any data exposure that contains PII there is the potential risk of criminals using the identities of those individuals to open fraudulent accounts, file false insurance claims, or apply for loans and credit cards. The exposure of health insurance cards or policy information could lead to what is known as “medical identity theft” where an uninsured patient poses as the policyholder and receives benefits they are not entitled to. This has been a growing trend in recent years, and it is estimated that overall insurance fraud (including Medicaid and Medicare insurance fraud) costs consumers as much as $105 billion per year. I am not stating nor implying that Confidant Health or their customers are at risk of extortion attempts, fraud, or any similar misuse of their personal or medical data. I am only providing a real-world risk scenario for educational purposes of how criminals could hypothetically exploit this information.
To anyone who believes their medical or personal information may have been potentially exposed online, my advice would be to take additional steps to protect yourself. Contact the healthcare provider or company responsible to understand the extent of the possible data exposure as well as the measures being taken to take control of the situation. Change all passwords for any online accounts or applications that may be linked to the potential exposure. It is also a good idea to contact your insurance company to issue a new account number.
In cases where PII such as SSN, DOB, and banking data has been exposed, I would recommend monitoring financial accounts and credit reports for signs of identity theft or other suspicious activity. If someone is using your personal information or identity, report it to the relevant authorities immediately. These steps can help to quickly address potential misuse, prevent further damages, and protect your personal information or health data.
Companies that provide medical or telehealth services can protect client data and prevent exposure online by encrypting all sensitive files and restricting access. I recommend giving sensitive records, such as health data, a limited lifespan. This way, once the documents are no longer in active use, they can be stored offline or in a secure cloud environment. These documents should only be available to authorized individuals and on an as-needed basis. Regular security audits and vulnerability assessments can identify potential weaknesses within the internal network. These audits can also identify documents or storage repositories that should be restricted and not publicly accessible.
Ensure that customers, or patients are required to use additional authentication measures, such as multi-factor authentication (MFA). The healthcare industry is a prime target for cyber criminals due to the fact that patient data — which is quite valuable — is required for their business to function and to accurately provide care. This is why the security of medical data is extremely important from both a technical and human standpoint. Service providers must handle sensitive information securely and train employees to recognize common traits of phishing attempts, social engineering, and other cyber security risks. Additionally, having an internal communication channel for data security and having an incident response plan in place can help mitigate the impact of a data incident.
Companies like Confidant Health provide valuable services to the communities and individuals they serve. The documents I personally saw detailed problems and treatment solutions for some very complex situations. For individuals who struggle with mental health or substance abuse issues, telehealth technology offers an affordable solution that can provide them with the help they need and that otherwise may be out of reach. There are many benefits to using technology to help those in need, but with those benefits comes the need to collect and store massive amounts of sensitive patient data. The days of patient’s files being stored in a physical file cabinet are virtually over, and as more medical records are stored online it is more important than ever to ensure the protection and security of health data.
Medical-related information in the U.S. is regulated by HIPAA (Health Insurance Portability and Accountability Act). The law establishes strict standards for the confidentiality, security, and protection of sensitive patient health information. HIPAA sets the basis of how healthcare providers, insurers, and other entities (such as mental health and substance use treatment providers) handle, store, and share potentially sensitive medical data. Additionally, the Federal Substance Use Confidentiality Requirements protect the privacy of individuals who have applied for or received services related to alcohol, drug, or other substance use disorders. These regulations restrict the disclosure of information related to substance use treatment; patient records are to be kept confidential and only used for medical or legal purposes.
I imply no wrongdoing by Confidant Health, their partners, or third-party contractors, nor do I claim that internal data or personal health data was ever at risk of being misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by Confidant Health would be able to identify this information along with any potential suspicious activity related to the breach. I publish my findings solely to raise awareness on issues of data security and privacy issues. This disclaimer does not intend to suggest that Confidant Health or its associated entities have not adequately safeguarded their data.




Please, comment on how to improve this article. Your feedback matters!