Facial DNA Service Provider Exposed Thousands of Records Online

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about the discovery of thousands of non-password-protected biometric images and metadata records belonging to ChoiceDNA — a company that offers genetic DNA testing and DNA Face Matching services.
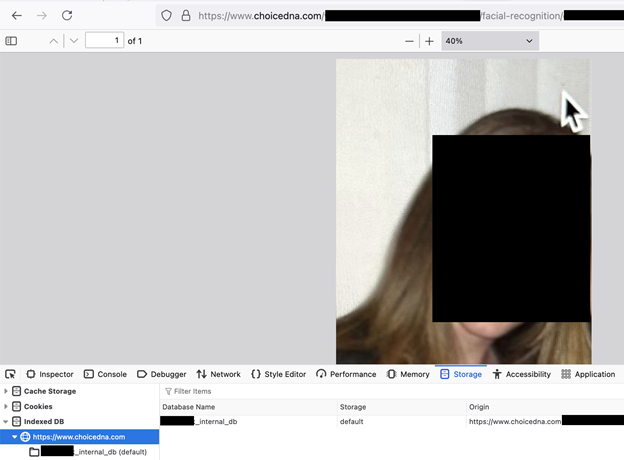
Recently, I discovered a trove of publicly accessible biometric images and metadata that contained names, phone numbers, email addresses, racial or ethnic identities, and notes indicating personal reasons for obtaining facial DNA analysis. The documents were stored in a non-secure WordPress folder that was accessible using nothing more than a web browser. The single folder contained an estimated 8,000 documents marked as “Facial Recognition Uploads”.
The records belonged to Indiana-based ChoiceDNA, a company that provides traditional DNA testing and offers a facial recognition service called FACE IT DNA. According to their website, the DNA Face Matching process calculates 68+ points of facial connectivity to aid in determining the genetic relationship of an alleged family member. I immediately sent a responsible disclosure notice of my findings, and the files were restricted from public access roughly a week later. I did not receive a reply to my disclosure notice and it is not known how long the biometric images were exposed or if anyone else accessed them. Only an internal forensic audit can identify additional access or suspicious activity. It is not known if ChoiceDNA managed the website or a third party.
Any company that offers facial recognition services based on a photo that is uploaded without the photo subject's consent raises potential ethical and privacy concerns. Collecting, storing, and analyzing biometric data or facial features without the knowledge or permission of these individuals is a serious potential risk to their personal autonomy and privacy. It is unknown if all individuals had given consent to have their biometric used by this service. Several U.S. states have enacted biometric privacy laws to regulate the collection and use of biometric data such as fingerprints, facial recognition data, and iris scans. These include Illinois, Texas, Washington, California, and New York. The states of Arkansas, Maryland, and Florida are in the process of developing biometric privacy regulations.
According to a 2023 policy statement by the Federal Trade Commission (FTC), facial images and descriptions are considered biometric data even if not processed to identify a person. The report also states that: “Consumers, businesses, and society now face new and increasing risks associated with the collection and use of biometric information. For example, biometric information can be used for the production of counterfeit videos or voice recordings (so-called “deepfakes”) that would allow bad actors to convincingly impersonate individuals in order to commit fraud or to defame or harass the individuals depicted. Large databases of biometric information may also be attractive targets for malicious actors because of the information’s potential to be used for other illicit purposes.”
The facial comparison technology used by ChoiceDNA is meant to analyze images to help assess the likelihood of a genetic link between potential family members. According to their website, the BASIC package is available for $38, while the PRO package is priced at $63 at the time of writing. However, ChoiceDNA’s terms and conditions policy contains a disclaimer: It is impossible to examine photographs and determine beyond any doubt whether a paternal (or other) relationship exists.
Potential Risks of Metadata Exposure
Metadata provides information such as structure, format, and context to help describe, organize, and manage the primary data source. Metadata is often embedded in documents, images, or other files and can increase the potential risks of sensitive information being exploited for phishing, social engineering schemes, or blackmail attempts. In this case, the exposed metadata contained names, emails, phone numbers, and other possible PII or personal information.
I saw numerous customers’ descriptions of sensitive family issues in their order notes for the facial DNA services. For example, one user uploaded images of multiple men and the same child, indicating the possible uncertainty of who could be the child’s biological father. Other information indicated concerns about family history and suspected infidelity, suspected siblings, parents, or other relatives. These are deeply personal issues that could also be leveraged by cyber criminals for potential extortion or social engineering attempts based on privileged or secret information. I am not saying nor implying that ChoiceDNA or their customers are or were ever at risk; I am only providing hypothetical threat scenarios for educational purposes.
Potential Risks of WordPress and Data Storage
It is estimated that nearly half of all websites online are powered by WordPress, making it the most popular content management software (CMS) globally. Wordfence, the makers of a popular security plugin for WordPress, released a report in 2020 claiming that they had blocked an estimated 90 billion malicious WordPress login attempts — an average of nearly 2,800 attacks per second. In 2023, Wordfence blocked more than 100 billion credential stuffing attacks originating from more than 74 million unique IP addresses.
In terms of secure data storage, other cloud storage providers such as AWS or Azure are generally considered more secure than a self-hosted WordPress CMS. When properly configured, cloud storage repositories offer advanced security features like encryption, frequent security updates, and threat or access monitoring. Additionally, these providers also have multiple datacenter locations globally that provide redundancy and protect against server downtime. In comparison, WordPress sites running on non-enterprise-grade hosting may often lack the more advanced security measures to store sensitive files, potentially leaving them more susceptible to vulnerabilities.
WordPress is a great platform for a wide range of business or ecommerce needs. By being aware of the potential vulnerabilities, organizations can take steps to protect their customers’ data no matter what CMS system they use. The most common potential risks of a CMS platform include brute force attacks, malware infections, SQL injections, cross-site scripting (XSS), and known vulnerabilities in outdated themes or plugins. Brute force attacks target login credentials, while malware can easily be injected through vulnerable plugins. To protect WordPress websites, admins should change the location of the default administrative login, use strong passwords, and regularly update plugins and themes. I also recommend installing additional security plugins, enabling two-factor authentication (2FA), and using Web Application Firewall (WAF) to block potentially malicious traffic. Geographical IP blocking can also be useful if your organization only provides services in a single country or location.
In my personal experience, it is rare to see exposed files stored in a self-managed WordPress folder, especially after using a third-party form submission plugin that allows files to be uploaded by customers. The plugins only provide the functionality — it is up to the administrator to secure any potentially sensitive user-submitted documents. In many instances, the WordPress uploads folder is not secure by default, and files stored there are often publicly accessible to anyone who knows or guesses the URL structure. WordPress must be configured to solely confine access to admins and credentialed users to view files or images located inside the uploads folder or any additional folders that contain data that should not be publicly accessible.
I would recommend for users or customers of any company that has a known data exposure to take action and change any passwords immediately. As a general rule, never reuse the same passwords for multiple accounts, create strong and unique passwords for each account, and enable two-factor authentication (2FA) as an added layer of security if it is offered. In incidents where emails and phone numbers are exposed, be cautious about any potential phishing attempts or suspicious requests for additional information. When personal or family details are exposed, criminals could potentially use this information posing as friends, family members, or representatives of the company you shared personal information with. Always verify requests for banking or credit card information, SSN, or other sensitive information to ensure that the person on the other end is who they say they are and that the request is legitimate.
I imply no wrongdoing by ChoiceDNA, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the files were publicly accessible, as only an internal forensic investigation conducted by ChoiceDNA would be able to identify this information along with any potential suspicious activity related to the breach. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties, and I disclaim any responsibility for actions that may be taken as a result of this disclosure. I publish my findings solely to raise awareness on data security and privacy issues.





Please, comment on how to improve this article. Your feedback matters!