How To Access the Dark Web Safely in 2025: An Easy Guide
- How To Protect Yourself on the Dark Web?
- Pro Tip: Use a VPN To Access the Dark Web Safely
- What is the Dark Web?
- How Do I Access the Dark Web in 2025?
- How To Access the Dark Web on Android and iOS
- Dangers of the Dark Web
- Tips to Stay Safe on the Dark Web
- Is the Dark Web Illegal?
- What Can I Do on the Dark Web?
- FAQs on Accessing the Dark Web Safely
- Conclusion
How do you enter the dark web? Accessing the dark web requires special tools and precautions, like using the Tor browser. However, the Tor network can be hacked, as evidenced by the 7 months of DDOS attacks experienced in 2022 (Securityaffairs)1.
I've listed the best ways to access the dark web safely, including connecting to a VPN server and using private search engines. The dark web is not illegal, but many activities are. Still, there are plenty of good reasons to access it, like research, whistleblowing, journalism, and financial privacy.
How To Protect Yourself on the Dark Web?
- Download the Tor browser.
This specialized browser allows you to access dark websites, which can't be done with a standard browser. For safety purposes, only download the browser from Tor's official website. - Set up the connection.
Connect to a VPN server to encrypt your traffic before using Tor. Then, Configure Tor based on your security preferences, click the connect button and wait for Tor to connect you to the node network. - Access the dark web.
Type in the onion address of your desired site, or use dark web search engines to find different sites on the dark web.
Pro Tip: Use a VPN To Access the Dark Web Safely
While Tor is designed to give you privacy while browsing the dark web, it’s not entirely safe. There might be malicious nodes with the Tor network, and there’s always the risk of your IP address leaking. Third parties like your ISP can also see when you access Tor and report it to the authorities, even if you’re not doing anything illegal. It’s essential to have additional security measures in place when using Tor.
The best way to stay anonymous on the dark web is to use a VPN with Tor. This easy-to-use app encrypts your internet traffic, rerouting it through its private servers and concealing your IP address. This hides your personal data from prying eyes, hackers, trackers, and other cyber threats associated with the dark web.
Editor's Note: Transparency is one of our core values at vpnMentor, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process.
What is the Dark Web?
The dark web is the 3rd layer of the internet, after the surface web and deep web. Here’s a general explanation of what you can find on each layer:
The Surface Web
The surface web — or clean web — is the part of the internet you can access anytime using mainstream browsers (like Chrome, Firefox, Safari, etc.). It includes any page that you can find with a simple Google search. However, your access is limited to the information that the website's administrator permits you to see. You can't access the backend files, account pages, or archives.
Take online stores like eBay as an example. You can freely browse products on the surface web. But to see your personal account details or to make a purchase, you need to log in. Once you log in, you're moving beyond the surface web and into the deep web.
The Deep Web
The deep web is the private layer, and it’s often password-protected. Deep web pages can’t be accessed through a simple search, as search engines do not index them — it’s a layer of the internet only accessible to people with a specific link or login credentials.
This category includes cloud drives, account pages on different websites, medical records, credit card information, reports, etc. You often need a specific URL and a password to access pages on the deep web. For example, your company database would be on the deep web.
The Dark Web
The dark web is the third layer of the internet and the hardest to find. It consists of websites that use the “.onion” top-level domain instead of “.com”, “.net”, etc. You can’t access “.onion” sites through regular browsers like Chrome and Firefox.
While the surface and deep web can be accessed this way, the dark web requires special software. Tor (The Onion Router) is the most commonly used browser for the dark web; however, it’s also accessible through networks like Freenet, Riffle, and I2P. You can find both legal and illegal websites/activities on the dark web, as it isn’t regulated in any way.
How Do I Access the Dark Web in 2025?
Accessing the dark web requires the right privacy and security tools to protect your online anonymity. Here’s a step-by-step guide to doing it legally and safely:
Secure Web Browsers
You cannot access the dark web using regular browsers like Chrome, Edge, or Safari. You must use a secure web browser that prioritizes privacy and security and can access onion sites. Even though it's possible to access the dark web using incognito mode, this does not protect your online identity and activities.
The best browser for safely accessing the dark web is the Tor browser. Download the official Tor Browser from torproject.org. Install and open the Tor browser, then configure your connection (default settings work for most users). However, disable JavaScript in the security settings to prevent tracking and vulnerabilities.
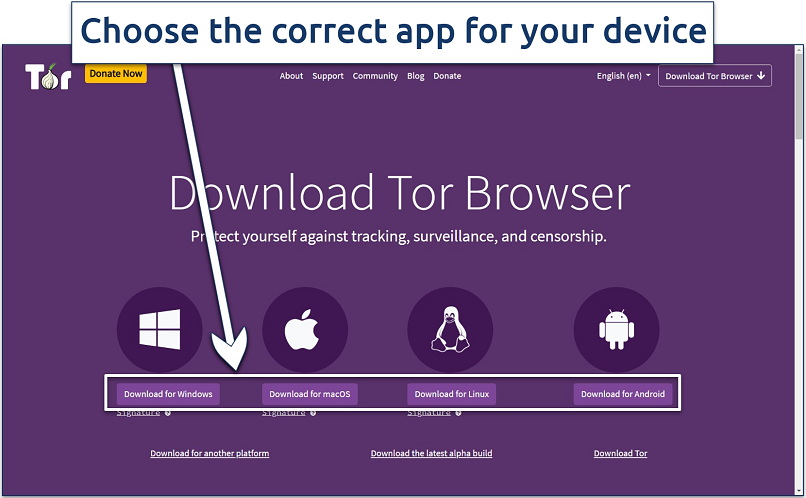 Simply run the downloaded installer and follow the prompts
Simply run the downloaded installer and follow the prompts
The Brave browser offers a built-in Tor mode, allowing access to .onion sites without installing the Tor browser. While convenient, Brave’s Tor mode does not provide the same level of anonymity as the standalone Tor browser, as Brave still connects to some standard web services. It’s best suited for light dark web browsing rather than heavy use.
Use a VPN
Before accessing the dark web, use a secure Tor VPN to hide your IP address and data from ISPs and potential malicious nodes on the dark web. You can download native VPN apps for different devices from its website or official app stores. Install it like any other app.
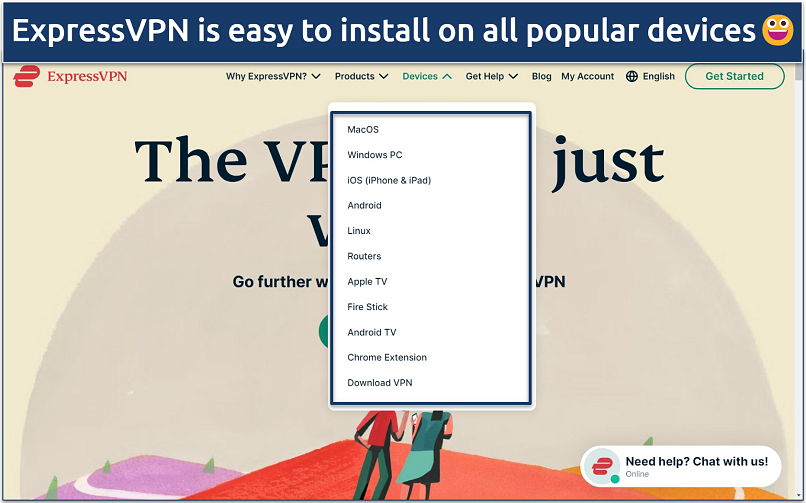 You can use it's 30-day money-back guarantee to test it risk-free
You can use it's 30-day money-back guarantee to test it risk-free
Install the VPN and connect to a server before opening Tor to prevent IP leaks. The nearest server will typically provide the fastest and most stable connection speeds.
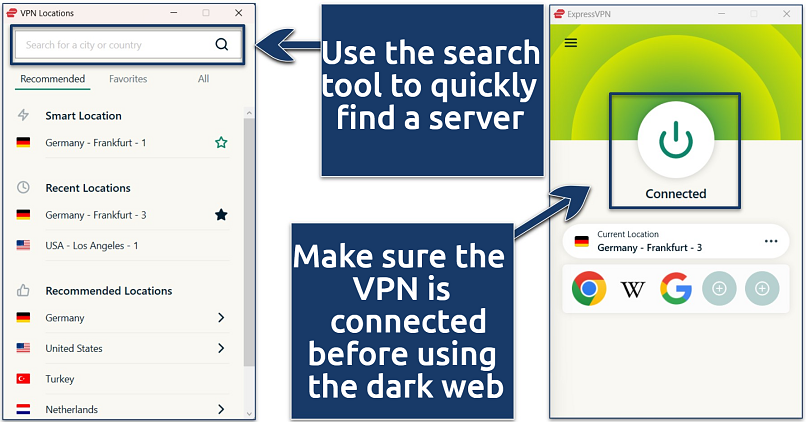 Or, just click the power button to connect to the nearest server
Or, just click the power button to connect to the nearest server
Use a Dark Web Search Engine
Regular search engines like Google don’t index dark websites. Instead, use dedicated search engines, like DuckDuckGo (.onion version), Ahmia, Not Evil, or Torch. When using dark web search engines, it’s important to exercise caution and refrain from clicking on suspicious links or accessing illegal content.
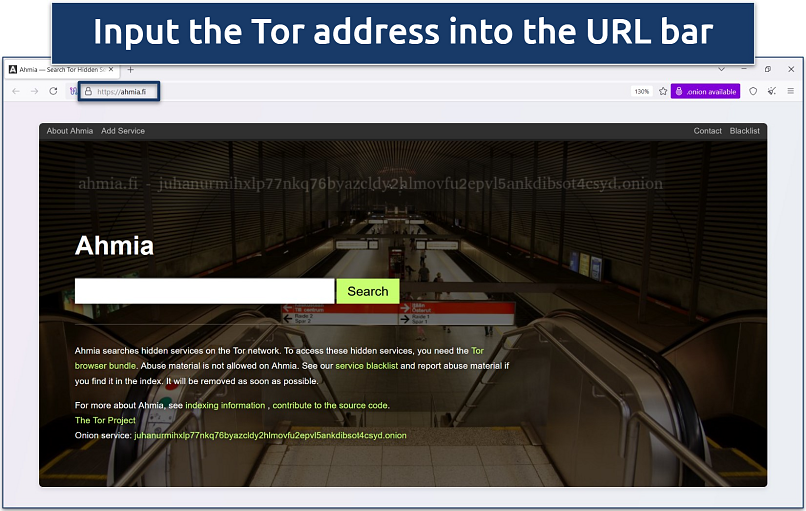 Once you're on the search engine, type in the domain or keyword
Once you're on the search engine, type in the domain or keyword
Find Trusted .onion Sites
Before engaging in any dark web activities, I recommend researching sites ahead of time — use your regular browser to look online and see which sites are reputable. There’s tons of information provided online by security experts recommending trustworthy .onion links.
Here are some safe and useful links for the dark web:
- ProPublica. Here you can find excellent pieces of investigative journalism.
- Hidden Answers. This is a dark web version of Quora where you can ask any question anonymously.
- Imperial Library. If you love reading, this dark website is great for you. You can find thousands of free books of any genre here.
- Hidden Wiki and TorLinks. These host libraries of dark web links, but it’s not as useful as Daniel since its links don’t work sometimes.
- SecureDrop. If you have some information that you want to share with a journalist, this is the website to visit.
- Dread. This is a Reddit-like dark web forum where you can take part in uncensored discussions.
 You should be careful of which links you click or info you give
You should be careful of which links you click or info you give
Use Alternative Dark Web Networks (I2P & Freenet)
IP2 is faster than Tor and offers stronger peer-to-peer security, as it uses one-way tunnels to encrypt traffic — meaning, only inbound or outbound traffic could be intercepted, not both. In addition, it uses a distributed network database which is harder to attack than Tor’s fixed, trusted Directory servers.
However, you won’t be able to use I2P to access as many sites as Tor. You can only access its specific sites (called “eepsites”). In addition, it’s a bit more difficult to configure; after downloading and installing, you’ll also have to manually configure it through the router, individual applications, and/or browser proxy settings.
Freenet is another Tor alternative but more of an anonymous place for peer-to-peer content sharing. Users can form their own private groups for content sharing, called darknet mode. Or, they can use opennet mode to be randomly assigned to other peers on the network. Like I2P, it uses a distributed network database for added assurance against cyber attacks.
You don’t need a server to upload content to Freenet; it will keep your content as long as it's popular. But, like I2P, Freenet won’t give you access to .onion links — only content uploaded to Freenet.
Use a Privacy-Focused Operating System (TAILS, Whonix, Linux)
Using a privacy-focused operating system adds an extra layer of security when accessing the dark web. TAILS (The Amnesic Incognito Live System) is a portable OS that runs from a USB or DVD, leaving no trace on your device. It forces all connections through Tor by default, ensuring complete anonymity while automatically deleting all activity upon shutdown.
Whonix is a Debian-based OS that runs inside a virtual machine. It routes all traffic through Tor, preventing IP leaks and offering stronger protection against tracking. Alternatively, Linux distributions like Qubes OS provide advanced security features for those needing long-term privacy-focused computing.
How To Access the Dark Web on Android and iOS
Accessing the dark web on mobile devices comes with greater security risks compared to using a desktop. You can access the dark web on both Android and iOS, but their limitations make it less secure. The best Android option is the Tor Browser, available on Google Play. For added privacy, use Orbot, which enables system-wide Tor routing for other apps.
On iOS, the recommended option is Onion Browser, but due to Apple’s restrictions, it lacks full Tor functionality. To improve security on mobile, you should always use a smartphone VPN, disabling JavaScript, and avoiding sensitive activities on mobile.
Dangers of the Dark Web
Due to the lack of regulations on the dark web, you are vulnerable to cyber threats any time you visit. These risks can be avoided when you are well-informed and know how to protect yourself against them.
Below are some of the most frequently encountered risks and measures you can take to protect yourself from them:
Potential malware
Browsing the dark web puts you at risk of cyberattacks such as DDoS attacks, botnets, and other malware or viruses. By simply entering the wrong URL or accidentally downloading a malicious file, you could install infectious viruses or malware. This can have a detrimental impact on your device or, even worse, expose your personal information.
To prevent these types of dangers, I recommend browsing the dark web with a direct goal in mind — research specific sites ahead of time and keep a list of links that you can trust.
Dangerous activities
The dark web is the home of many criminal activities — from the use of stolen or fake documents to drug and weapon dealing. What’s more, it’s a network that includes assassins for hire, child pornography, and even live streams of murders. If you accidentally end up on one of those pages, you may face legal charges should someone find out.
To avoid encountering disturbing or illegal situations, I advise against entering darknet sites before thoroughly researching them. I also recommend that you browse the dark web with complete anonymity by using a VPN — just to be safe.
Fraudulent sites
Hackers on the dark web can easily access your personal data using trojans, phishing, and other types of fraudulent websites or programs. Sometimes, all it takes is a simple misclick before all the information stored on your computer gets leaked. Even worse — cybercriminals have been known to activate computer cameras and microphones to get live streams from unsuspecting victims.
Most URLs on the dark web have unrecognizable names, so it’s easy to fall for this trap — putting your private files, financial data, keystrokes, and other personal information at risk. Social engineering tactics are also common, where bad actors try to get you to willingly give up sensitive information, like login details, financial information, etc.
Surveillance
In an attempt to stop criminal organizations operating on the dark web, authorities are setting up fake websites to track possible criminal activity. By doing this, they get access to whoever is visiting the sites — including you if you accidentally end up there. In some parts of the world, simply using a browser like Tor can get you flagged by these agencies, even if you don’t partake in illegal activity.
While Tor is an open-source project, your activity can still be traced back to your IP address. The best way to prevent your browsing activity from alerting authorities is to avoid sites with illegal activity altogether — another reason to only visit sites you’ve researched and trust.
Tips to Stay Safe on the Dark Web
To boost your overall safety while navigating the dark web, it's important to adhere to certain protective measures. The following are some recommended precautions to take:
- Use antivirus software. This will add a layer of protection to help keep you and your devices safe from cyberattacks. Keep up with the software updates — if a newer version comes out and you’re still running an old version, it won’t be equipped to block the latest cyber threats.
- Use a different email. Instead of using your actual email address, sign up for a different one you can use solely for your dark web activity. You can even get an encrypted email address — for example, through ProtonMail.
- Keep your identity private. Don’t use your real photo, phone number, or name. Don’t share any personally identifiable information or sensitive data while on the dark web.
- Use Bitcoin. Instead of using your personal credit cards, use Bitcoin — this offers an extra layer of anonymity when you make purchases on the dark web and protects you from having your financial information stolen. Also, exercise caution with services that demand upfront payment.
- Only shop on trusted sites. Research the sites you plan to make purchases through ahead of time. Research vendors thoroughly, read user reviews, and be skeptical of any too-good-to-be-true deals. Consider using escrow services to mitigate the risk of scams.
- Avoid add-ons. Tor automatically blocks some plug-ins (like Flash, RealPlayer, and Quicktime) — hackers have manipulated these to get users’ real IP addresses in the past since they are out of Tor developers’ control. Add-ons and browser extensions can also lead to tracking through browser fingerprinting.
- Cover your camera and your microphone. You can do this with a bit of opaque tape. This protects you from cybercriminals attempting to hijack your device to collect unsolicited recordings of you.
- Open your downloads offline. If you download a file from the dark web, disable the internet before opening it. Opening it while you're connected could potentially leak your real IP address.
- Don’t change the size of your Tor window. This can lead to someone tracking you through browser fingerprinting. You can disable browser resizing entirely in the settings.
- Use Tor Bridges or obfuscated nodes. If Tor is blocked in your country, enable Tor Bridges in the settings or use obfuscated VPN servers to mask your Tor traffic from ISPs.
- Use multi-signature cryptocurrency wallets. Instead of Bitcoin, consider using Monero (XMR) for better anonymity or a multi-signature wallet like Electrum to prevent unauthorized access.
- Set up a virtual machine (VM). Adds an extra layer of security by isolating your activities from your main operating system in case your VM gets infected.
Editor's Note: Transparency is one of our core values at vpnMentor, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process.
Is the Dark Web Illegal?
The dark web is legal in most countries, provided you do not engage in illegal activities. However, in countries with strict censorship laws — such as China, the UAE, and Pakistan — accessing the dark web is considered a crime. In Russia and India, authorities closely monitor dark web traffic.
Even in countries like the US and Europe where it’s legal, you may be put under surveillance for simply using a dark web browser like Tor. Authorities use the dark web as a tool to catch criminals participating in illegal activities such as human trafficking, drug or weapon deals, and more.
Several Major Dark Web Marketplaces Have Been Shut Down:
- The Silk Road Case. This site was like the Amazon of the dark web. It started with a good cause in mind but ended up being a host for the sale of illegal goods — such as drugs, weapons, and forged paperwork. The person behind the website got caught because he promoted his website on the surface web using his real email address.
- AlphaBay Case. This website continued where the Silk Road stopped — it sold and traded drugs, weapons, and other illegal products. The owner ended up getting caught because he used weak passwords, his real email address, zero encryption, and more.
- The Ashley Madison Case. This one went viral. Ashley Madison was a website for extramarital affairs. Hackers released the information of people using this website, ruining a lot of lives. The hackers were never caught.
- DarkMarket. Seized in 2021, DarkMarket was one of the largest illicit marketplaces, hosting nearly 500,000 users trading stolen data, drugs, and counterfeit currency³. Europol and global agencies coordinated its shutdown.
While such stories can cast the dark web in a negative light, it's worth noting that there are numerous legal and beneficial activities accessible through it. I advise sticking to well-known, reliable sites and taking extra precautions to ensure your security.
What Can I Do on the Dark Web?
There are many beneficial activities and resources available on the dark web, but it’s important to keep your identity anonymous nonetheless. Using Tor without precautions can make you vulnerable to several cyber threats, such as hackers, trackers, and malware. However, when you practice safety while visiting the dark web, you can enjoy its many positives, such as:
- Free speech. The dark web gives people living in countries under heavy censorship a chance to communicate openly without risk of exposure.
- Exposing criminals or corrupt public figures. Journalists and whistleblowers turn to the dark web as a safe place to share/receive anonymous tips online or investigate controversial situations.
- Buying products cheaper. Some products can be found on the dark web for less money, such as electronics or security software — making purchases on the dark web is risky, so you should always use Bitcoin and buy from credible sources.
- Research material. You can find free resources such as digital books and research papers on the dark web.
Communicating anonymously. There are online communities and support websites available on the dark web where you can get tips and advice without revealing your identity. - Get medical advice. If you’re experiencing symptoms or have a health concern, there are doctors available on the dark web that can offer you their expertise. This is especially helpful for those who want to keep their health concerns personal or simply don’t have the funds to visit a clinic.
Best VPNs for the Dark Web in 2025
- ExpressVPN — Follows a strict no-logs policy and uses RAM-based servers that erase all your data upon reboot. Plus, it routes all your dark web traffic safely through its encrypted DNS servers, so no one can intercept or see your activity on the dark web.
- CyberGhost — State-of-the-art security features like AES 256-bit encryption, DNS/IP leak protection, and a kill switch keep your dark web activity from being exposed.
- NordVPN — Threat Protection feature safeguards against various online and offline threats, while Dark Web Monitor alerts you if your info is leaked on the dark web.
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: Intego, Cyberghost, ExpressVPN, and Private Internet Access. However, this does not affect our review process, as we adhere to a strict testing methodology.
FAQs on Accessing the Dark Web Safely
Why was the dark web created?
The US military created the dark web to protect US intelligence communications online. It was later released to the public in 2000, where its ability to offer a high level of anonymity has led to various use cases. While it has legitimate uses, the dark web's anonymity also makes it a hotbed for illicit activities, contributing to its infamous reputation.
Can I access websites on the dark web on my phone, iPad, or Chromebook?
Yes, but there isn’t native support for Chrome OS. The Tor Project endorses the Tor Browser or Orbot for Android or the Onion Browser and Orbot for iOS. The Android app may work on Chrome OS, but it hasn’t been audited, and not all features may function properly.
Is due to the ever-evolving nature of the dark web — search engines there simply can’t keep up with the changes, often providing irrelevant or repetitive results.
What's The Difference Between Tor Over VPN And VPN Over Tor?
The difference is the order in which your internet traffic travels. Tor over VPN directs your traffic through the VPN server before going through Tor’s network — while VPN over Tor directs your traffic through Tor’s browser first. While both are better than not using a VPN, it's safer to use Tor with a VPN that doesn’t keep logs — this way, prying eyes won’t know that you’re on Tor; they’ll just know that you’re using a VPN.
Keep in mind that using a VPN over Tor is not advised — even by the Tor browser itself. In this case, your traffic goes through Tor’s network first before going through a VPN. Your internet service provider still won’t see your IP address, but they will know that you are using Tor.
Is Tor completely anonymous?
No, while it hides your IP address and traffic, there are still vulnerabilities. Malicious exit nodes can monitor your traffic, and browser fingerprinting can track you. Governments also often monitor Tor usage, even if they can’t see your activity. It’s recommended to take safety precautions when accessing the dark web, even if you’re after legitimate content.
Can my ISP see if I use the dark web?
Yes, your ISP can see if you access the dark web, but not what you do on it. Tor traffic has a distinct fingerprint, allowing ISPs and governments to detect its usage. While they can’t see your browsing activity, some countries monitor or flag Tor users. Use a VPN before connecting to Tor (Tor over VPN) or an obfuscated bridge, which makes Tor traffic look likfe normal web traffic.
Conclusion
How big is the dark web? Although the dark web is a small portion of the internet, experts estimate it to account for 5% of all internet content (Spiceworks, 2025)2. According to McAfee, the deep web is about 10 to 20 times larger than the surface web, making up 90 to 96% of the internet3.
To safely access the deep or dark web, always verify sites before visiting, disable JavaScript, and avoid sharing personal information. Privacy-focused tools like Tor, a VPN, TAILS OS, or Whonix can further enhance your security and anonymity.
References
- https://securityaffairs.com/142215/hacking/tor-network-under-ddos-attacks.html/
- https://www.spiceworks.com/it-security/security-general/articles/dark-web-vs-deep-web/#:~:text=Some%20experts%20peg%20the%20size,exist%20on%20the%20deep%20web/
- https://www.mcafee.com/learn/the-dark-web-a-definitive-guide/
Your data is exposed to the websites you visit!
Your IP Address:
3.138.143.105
Your Location:
US, undefined, undefined
Your Internet Provider:
The information above can be used to track you, target you for ads, and monitor what you do online.
VPNs can help you hide this information from websites so that you are protected at all times. We recommend ExpressVPN — the #1 VPN out of over 350 providers we've tested. It has military-grade encryption and privacy features that will ensure your digital security, plus — it's currently offering 61% off. Editor's Note: ExpressVPN and this site are in the same ownership group.



Please, comment on how to improve this article. Your feedback matters!