What Is a MAC Address? Find it on PC, Phone, and More (2026)
A MAC address is essential for networking control, data sharing, and security. However, most resources or Reddit posts can’t explain “What is a MAC address?” in simple terms. Here, you can find a clear definition, examples, and ways it’s used.
I’ll also cover the differences between MAC addresses and IP addresses. More importantly, this step-by-step guide can help you find a unique MAC address for every popular operating system, including your computer, phone, and printer.
It’s important to note that your MAC code can expose you to security risks on public WiFi networks. To address this, I also provide tips on how to protect your address on various devices.
What is a MAC Address? A Definition in Simple Terms
A MAC (Media Access Control) address is a unique 12-digit code assigned to the devices' network interface controller (NIC). Manufacturers assign these unalterable addresses during the production process.
A single device can possess multiple MAC addresses. For example, if you own a laptop with an Ethernet cable port and built-in WiFi, your system configuration will display 2 distinct MAC codes.
MAC addresses are primarily needed to manage devices in a network, but they have other uses.
What does a MAC address look like?
A MAC address is a 12-digit hexadecimal number, 48 bits in length. An example of a code for a NIC looks like this: e0:1c:2d:3e:a4:b5.
The code consists of 2 parts: the Organizationally Unique Identifier (OUI) and the device-specific portion.
- The OUI is the first six digits that are unique to each manufacturer. They can reveal who made the device (or the network adapter in the device).
- The last six digits are specific to the individual device. The manufacturer assigns these to each device.
What is the MAC address used for?
MAC addresses enable routers and switches to correctly forward data packets between devices in a network. In other words, they are necessary for communication between your router and devices. For this reason, two devices can’t share the same address code. Aside from that, these addresses also have the following uses:
- Connection issue diagnosis. MAC addresses help you troubleshoot network issues. By examining the flow of MAC addresses in the network logs, you can pinpoint connectivity problems and identify which devices are affected to resolve issues.
- Device segmentation. Network segmentation is made easier, especially in Virtual Local Area Networks (VLANs). You can restrict certain devices or groups of devices to certain network sections, improving the network's security and performance.
- Internet setup. Your Internet Service Provider (ISP) may enforce MAC binding, allowing only certain devices to connect to the web. Providers need the address of your router from which other devices will use the Internet.
- Traffic prioritization. MAC addresses help in managing network traffic by prioritizing data delivery. For example, you can prioritize your device over others for high-bandwidth internet activities.
- Network security. By creating a whitelist of MAC addresses, network administrators can significantly enhance network security. This method restricts network access to only those devices whose MAC addresses are on the list, preventing unauthorized access.
How is a MAC address different from an IP address?
MAC and IP addresses are different types of device identifiers with distinct purposes. While your MAC address is tied to your device, your IP address is associated with your network. The following table lists their differences.
| MAC Address | IP Address | |
| Permanence | MAC addresses are permanent and remain constant across networks (but you can artificially spoof or clone them). | IP addresses are dynamically assigned and can change based on network configuration. This address is not tied to the hardware. |
| Naming | Referred to as physical addresses because they are hard-coded into the hardware. | Referred to as logical addresses, indicating their role in logical network organization and routing. |
| Layer | Functions at the data link layer (Layer 2) of the OSI model, handling node-to-node data transfer and error management. | Operates at the network layer (Layer 3), managing packet forwarding and routing across different networks. |
| Applicability | Used within local networks for precise device communication and cannot be routed across the internet. | Used globally, enabling devices to communicate across various networks via the Internet, and is essential for broad connectivity. |
| Function | Crucial for the local delivery of data packets directly to devices within the same network. | Identify devices globally and guide data packets across the Internet. |
Guide: How to Find the MAC Address of Any Device
The MAC address is often printed on a device's bottom label. However, some devices lack labels and require you to inspect them via the system’s settings.
Manufacturers can identify a MAC code by other names, such as hardware ID, physical address, wireless ID, or WiFi address. Remember this when searching for information on your device.
Windows
On Windows, you can inspect your MAC code with and without the command prompt.
Via the command prompt
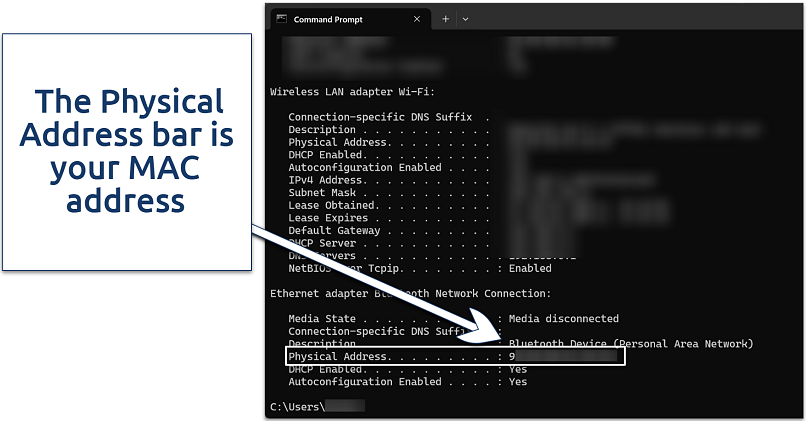 Command prompt allows you to find the MAC address of each network interface in your device
Command prompt allows you to find the MAC address of each network interface in your device
- Open the Command Prompt by typing cmd in the search bar.
- Type ipconfig /all and press Enter to display network details.
- Locate the Physical Address under your web interface (this is your MAC address).
Without the command prompt
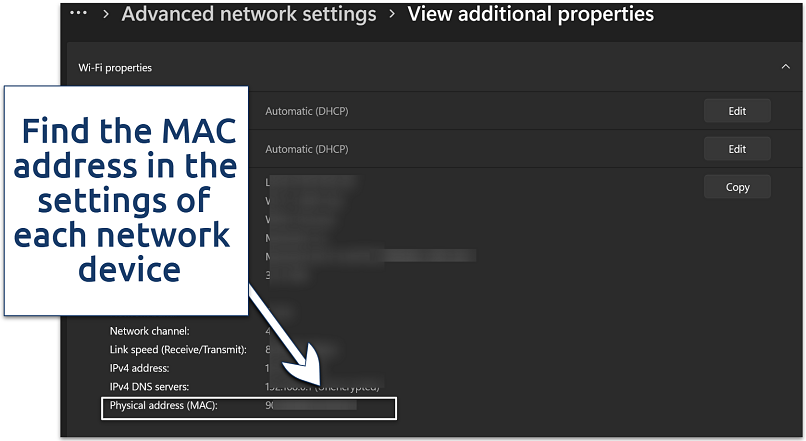 You can check the MAC code through the Windows Control Panel
You can check the MAC code through the Windows Control Panel
- Open the Control Panel by searching the taskbar, then navigate to Network & internet.
- Go to the Network and Sharing Center to find the list of available networks.
- Right-click on your active network connection and select Properties (or View additional properties).
- Find the MAC address listed under the Details of your network device properties.
Mac
MacOS displays the codes via the system interface. Here’s how to find them.
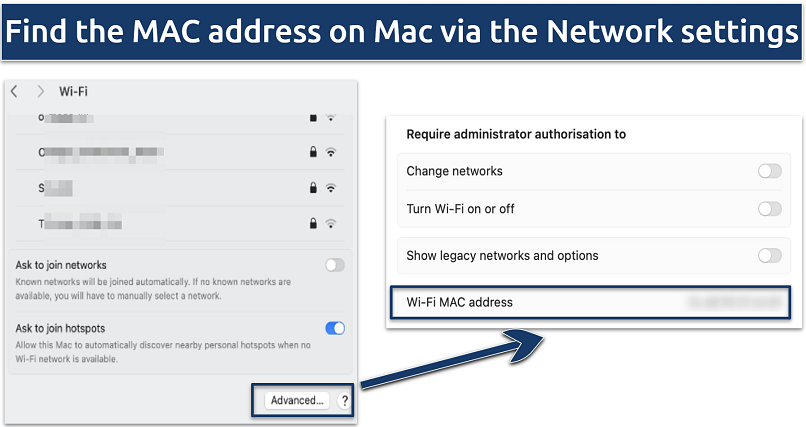 The Advanced setting displays your MAC address for this network
The Advanced setting displays your MAC address for this network
- Click the Apple icon at the top-left, select System Preferences, and then Network.
- Choose the network interface you use from the list and click Advanced.
- View the MAC address. Note that some devices require you to click the Hardware tab to view it.
Linux
You can easily find the Linux MAC code via the terminal window.
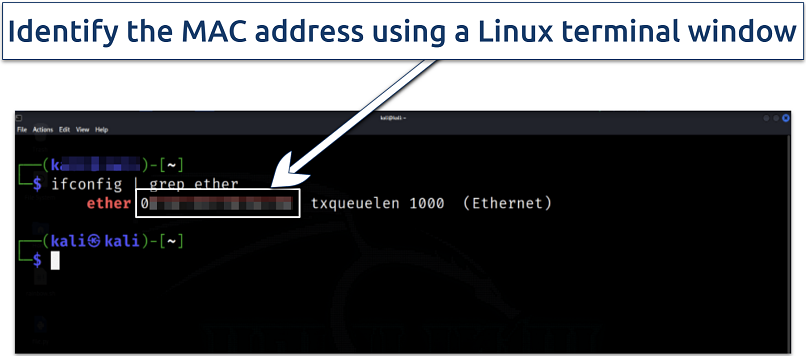 You may need to superuser access to use this command
You may need to superuser access to use this command
- Log in as the superuser by using the su - or sudo -i command (this requires you to enter your password).
- Open a terminal window and type ifconfig (or ifconfig | grep ether), then press Enter.
- Under your WiFi or Ethernet settings, find ether followed by MAC codes.
Chromebook
The Chromebook code can be found easily from the main menu.
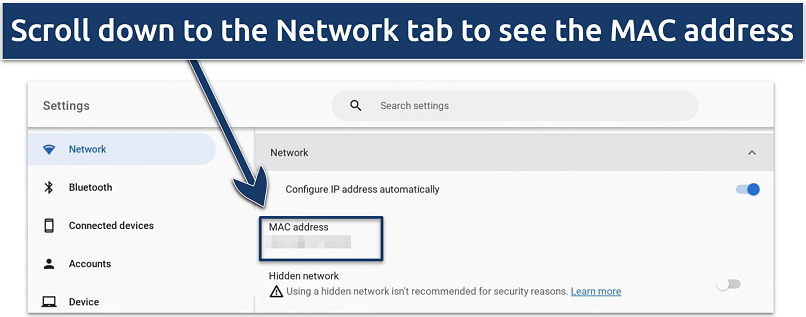 Your other network settings are also displayed in this section
Your other network settings are also displayed in this section
- Open Settings from your Chromebook's menu.
- Navigate to Network and select WiFi.
- Choose your WiFi network to see its address.
Android
Android devices list MAC codes in their settings.
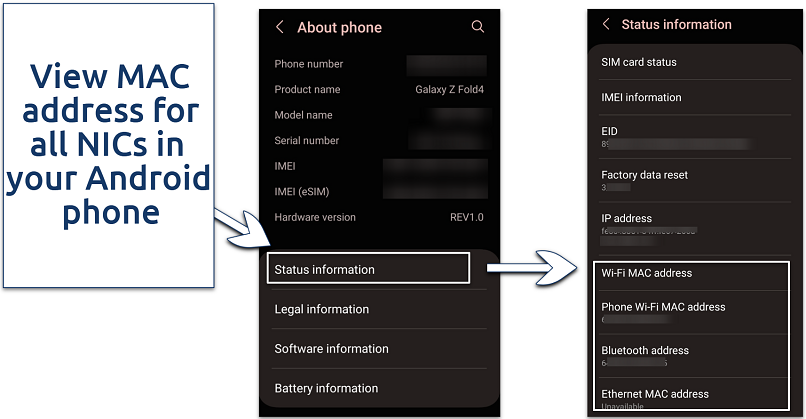 The settings show MAC codes for Ethernet, Bluetooth, and WiFi adapters
The settings show MAC codes for Ethernet, Bluetooth, and WiFi adapters
- Open Settings on your Android smartphone or tablet.
- Scroll to About phone (or About tablet).
- Click Status information to see your MAC addresses.
iPhone & iPad
Finding the code for your Apple smartphone or tablet takes a few seconds.
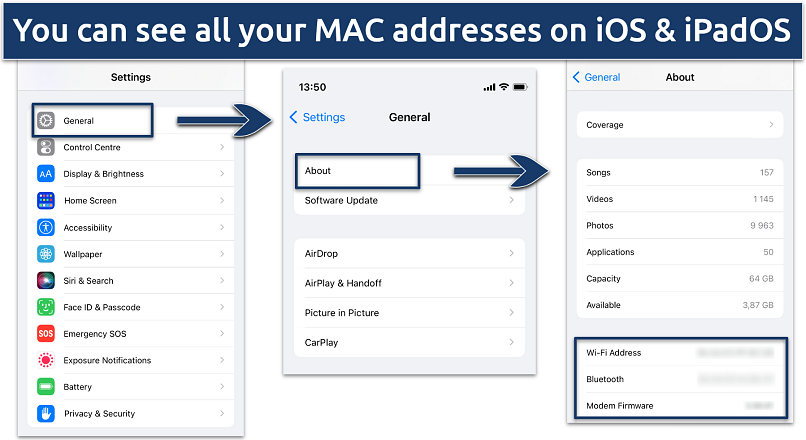 The About section displays your Ethernet (LAN) MAC address when you connect an adapter
The About section displays your Ethernet (LAN) MAC address when you connect an adapter
- Open Settings on your iPhone or iPad.
- Select the General tab and click About.
- Locate your address under the WiFi Address.
Smart TVs
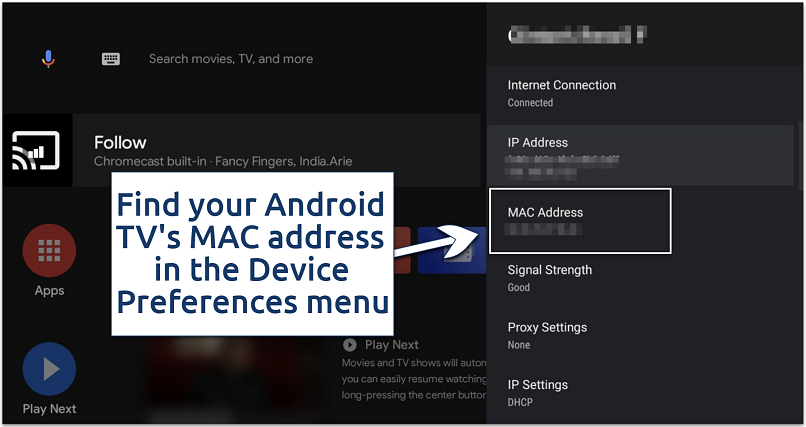 Check the manufacturer's page if your smart TV doesn't have the same settings
Check the manufacturer's page if your smart TV doesn't have the same settings
The instructions for finding a MAC address vary for different manufacturers or TV models. If you can’t find the same settings, please check the official guide for your smart TV.
Android TV
- Go to Settings from your home screen.
- Select Device Preferences and click About.
- Click Status to view your MAC addresses.
Sony TV
- Press the HELP button on your remote control.
- Choose Status & Diagnostics. Depending on your TV's menu, the section can be called View Network Status or Contact & Support.
- Locate System Information to find your wired (Ethernet) or wireless (WiFi) MAC address.
Samsung TV
- Open Settings and go to Support.
- Choose About this TV (or Contact Samsung).
- Scroll to find the Ethernet and WiFi codes.
Apple TV
- Access Settings from the home screen.
- Navigate to Network.
- Find your addresses next to the Ethernet Address and WiFi Address.
Amazon Fire TV
- Navigate to Settings.
- Click My Fire TV and select About.
- Go to Network to see your MAC addresses.
Roku devices
It takes a few steps to find a MAC code on a Roku device.
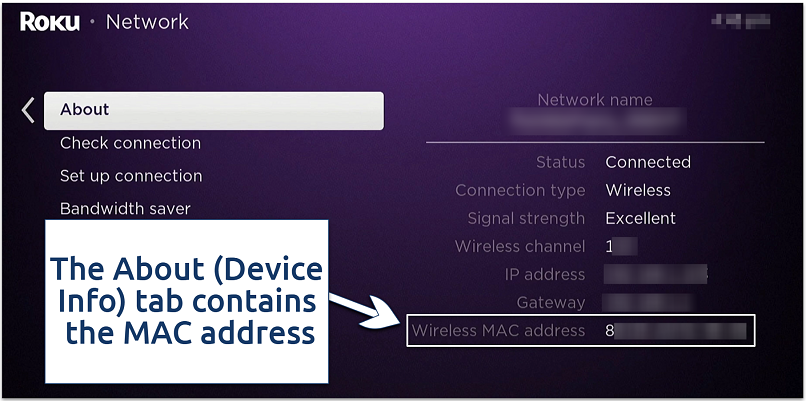 You will see either a WiFi or Ethernet MAC, depending on your connection type
You will see either a WiFi or Ethernet MAC, depending on your connection type
- From the Home screen, navigate to Settings.
- Select Network and then choose Device Info (or About).
- View your MAC address under Ethernet MAC address on the right side.
PlayStation consoles
The steps to find the MAC addresses on PlayStation 3, 4 and 5 are nearly identical.
 Finding the MAC address on older PlayStation consoles is just as easy
Finding the MAC address on older PlayStation consoles is just as easy
- Navigate to Settings from the main menu. On PlayStation 5, click the gear icon in the upper right.
- On PlayStation 5 go to Network, click Connection status, and select View Connection Status. On PS 3 and 4, go to System and select System Information (or Console Information).
- Locate your wired or wireless MAC address.
Xbox consoles
Looking up your address on Xbox gaming consoles is straightforward.
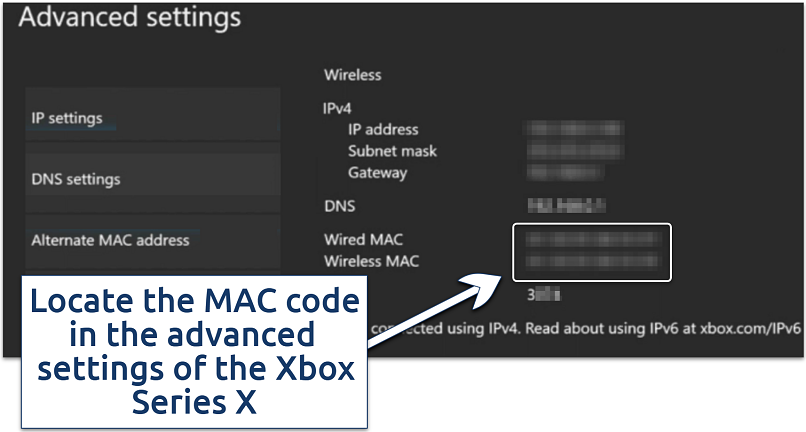 This tab showcases MAC addresses for wired and wireless NICs
This tab showcases MAC addresses for wired and wireless NICs
- Go to Settings from the Xbox console home screen. On Xbox 360, go to My Xbox and select System Settings.
- Select Network (or Network Settings) under the console tab.
- Click Advanced Settings (or Additional Settings) to access the wired and wireless addresses.
Nintendo Switch consoles
You can quickly check your wireless and wired MAC addresses for a Nintendo Switch console.
 If you're connected by wire, you will see a MAC address for a LAN connection
If you're connected by wire, you will see a MAC address for a LAN connection
- Navigate to System Settings from the Home screen.
- Choose Internet Settings (or Internet).
- Find the wireless MAC address under the Connection Status tab.
- Click Wired Connection to see the address for the USB LAN adapter.
Printers
There are several ways to look up a MAC code on a printer.
- Look at the product manual cover. Check your printer's manual cover for a label that lists the address under Physical Address or MAC Address.
- Using the terminal. If your printer is in Developer Mode, open the terminal, type ifconfig -a, and press Enter to display network details with the MAC address.
- Command prompt method. On a network-attached computer, open Command Prompt, type arp -a, hit Enter, and look for the MAC address next to your printer's IP address.
Does the MAC Address Impact Your Security or Privacy?
You should know the security and privacy risks associated with MAC addresses. Understanding these vulnerabilities is a crucial step for protecting your network and personal data from potential threats. However, there are additional safety precautions (like hiding your IP) that you should take in conjunction.
- Tracking. Each network you connect to identifies your device using its unique MAC address. This feature allows entities to track your location as you move between different networks, raising significant privacy concerns, as highlighted by the reports about MAC address usage in tracking by government agencies.
- Unauthorized access. MAC spoofing (MAC cloning) is a technique for impersonating another code. It can be exploited to gain unauthorized network access or bypass MAC filtering.
- Security exploitation. The Organizationally Unique Identifier (OUI) in your MAC address reveals the device's manufacturer. This information can be used to target specific vulnerabilities associated with that manufacturer.
- MAC flooding. Attackers use MAC flooding to disrupt the normal operation of network switches by overwhelming them with numerous MAC addresses. This attack can lead to network instability and unauthorized data access, compromising network security.
Ways to Hide (Change) Your Unique MAC Address
You can hide or change your MAC address to protect your privacy on public networks. Some devices have this option by default, while others require enabling it.
Windows
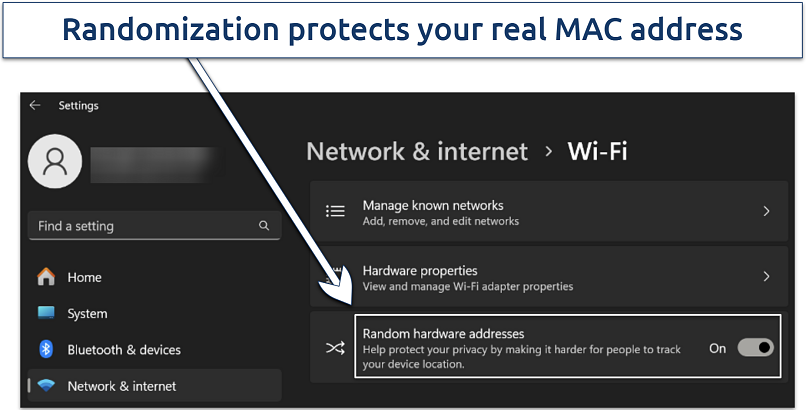 The MAC spoofing is enabled on Windows 11 by default
The MAC spoofing is enabled on Windows 11 by default
Hardware address randomization on Windows changes your device's address on WiFi networks. This feature prevents passive observers from using your MAC address to track your device, even when connected to other networks like cellular. Here’s how to enable it:
- Go to Settings on your Windows 10 or 11 device.
- Navigate to Network & Internet and select WiFi. On Windows 10, you need to select Advanced options.
- Toggle on Random hardware addresses.
Mac
Apple devices automatically use a randomized MAC address during WiFi scans when they are not connected to a network. To spoof your address manually:
 Make sure you have an administrative privileges to spoof the MAC address
Make sure you have an administrative privileges to spoof the MAC address
- Open the Applications folder with the WiFi turned off.
- Navigate to Utilities and launch the Terminal app.
- Type sudo ifconfig en0 ether XX:XX:XX:YY:YY:YY in Terminal to replace XX:XX:XX:YY:YY:YY with your desired MAC address.
- Press return and enter your password for the changes to take effect.
Linux
Support for MAC address randomization in Linux depends on the desktop environment. Here’s how you can enable it on GNOME and KDE Plasma:
- Open Settings and navigate to Network.
- Click the gear icon next to your active connection and select WiFi.
- Go to Identity and find Cloned Address.
- Select Random to spoof your MAC address.
Android
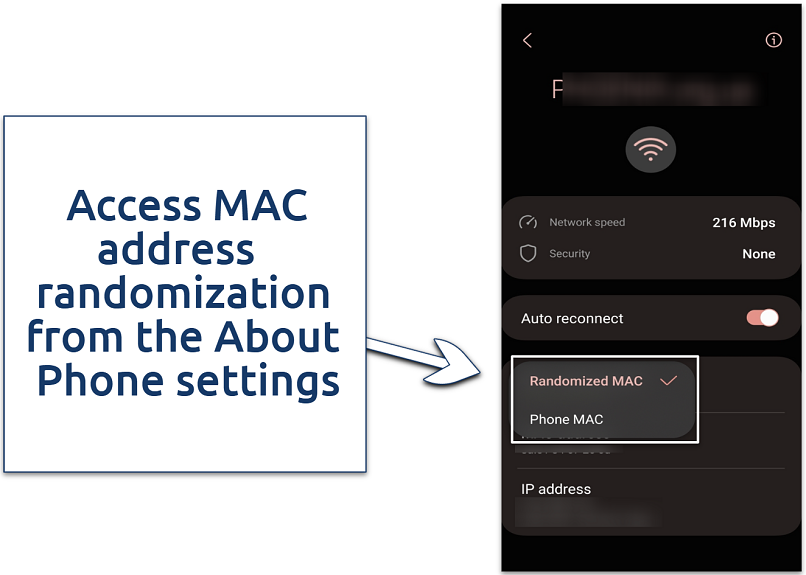 Setting to Phone MAC makes your real address visible on public WiFi
Setting to Phone MAC makes your real address visible on public WiFi
Android 10 and newer versions automatically generate random MAC addresses for each WiFi network. To make sure the feature is enabled:
- Navigate to Status information in the About phone section of the device’s Settings.
- Select WiFi MAC address, choose your current or another saved network, and click View more.
- Ensure MAC address type is set to Randomized MAC.
iOS & iPad
MAC address randomization is active by default on iOS and iPadOS 14+ devices. Like Android, Apple products spoof your MAC code for new networks. Here’s how to ensure the randomization is on:
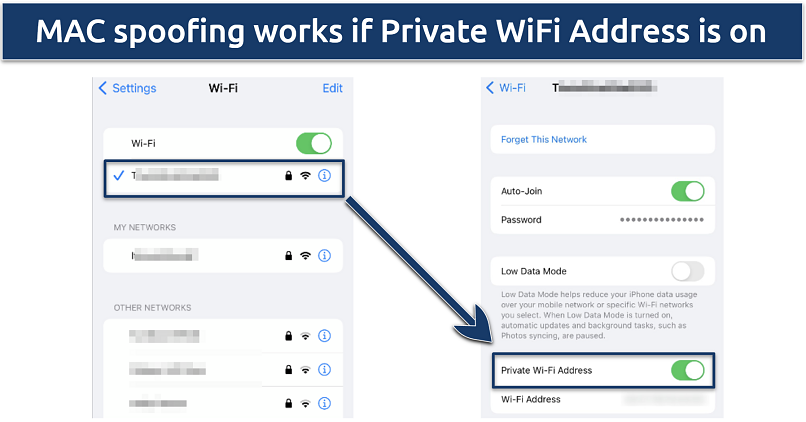 By default, your MAC address is hidden on public WiFi on the latest iOS
By default, your MAC address is hidden on public WiFi on the latest iOS
- Open Settings.
- Navigate to WiFi and select your network.
- Check if the Private WiFi Address is enabled.
Chromebook
Chrome OS automatically uses MAC address randomization, which is impossible to disable.
Want to learn more about ways you can safeguard your online privacy? Here are a few helpful articles to get you started.
- Best Ad Blockers — We tested and ranked the best blockers to prevent ads, malware, and trackers from invading your digital privacy.
- Best VPNs — These are our top picks for shielding your IP address and preventing third parties from spying on your online activities.
- How to Hide Your IP Address — Explore the various ways to hide your IP address and safeguard your personal data.
FAQs About MAC Address
Will my MAC address change?
Manufacturers hard-code MAC addresses into NICs and do not change them under normal circumstances. However, you can temporarily hide or spoof your MAC address for privacy purposes. Most operating systems automatically randomize your code for public WiFi networks by default for extra security.
Can my device have more than one MAC address?
Yes, each network interface in your device has a unique MAC address. For example, if your laptop has an Ethernet port, Bluetooth, and WiFi adapters, it will have 3 distinct addresses. Unique MAC codes ensure that each interface can communicate on a network.
What is MAC cloning (spoofing)?
MAC cloning involves changing the address of a device within its network settings or using third-party software. MAC spoofing helps enhance your device’s security, among other things. On routers, MAC cloning can typically be configured through the administrative interface under network settings. Here’s how to clone a MAC address on Windows:
- On the source service: Open the Start menu, type Cmd in the search box, and press Enter. In the Command Prompt, type ipconfig /all and press Enter. Locate and copy the MAC address listed next to Physical Address.
- On the target device: Click Start, then type and select View Network Connections. Right-click on the relevant Wireless Network Adapter (or Local Area Connection). Select Properties, click Configure, and navigate to the Advanced tab.
- Find and select Network Address from the list, click the value field next to it, and enter the MAC address you copied earlier. Click OK to save the changes.
Which part of a MAC address is unique to each manufacturer?
The OUI — the first six hexadecimal digits of a MAC address — is unique to each manufacturer. This part of the MAC address ensures that each network device has a unique identifier, at least in the context of who manufactured it.
Can a VPN protect my MAC address?
No, a VPN cannot protect your MAC address. However, VPNs encrypt your internet traffic and protect your IP address, adding a layer of security against online tracking and hackers. Additionally, you can hide your MAC address manually to safeguard your device.
Identify and Hide Your MAC Address in Seconds
Finding your MAC address can be done in less than a minute. To make it easier for you, I have provided detailed instructions for all popular operating systems.
Knowing how to protect your MAC address is crucial for maintaining your security. It shields your device from potential tracking and unauthorized network access. While this is one key step in protecting your online privacy, it’s also worth taking additional precautions, such as shielding your IP address.



Please, comment on how to improve this article. Your feedback matters!