The Ultimate Guide to Ethical Hacking | What You Need to Know in 2026
Can hacking ever be a good thing? What is ethical hacking and how is it different from other kinds of hacking? How can you be an ethical hacker and why would a company willingly say yes to being hacked?
In this article, we will dive into the field of ethical hacking to answer all of these questions and more. We’ll discuss what hacking really means and explore the real techniques used by both ethical and malicious hackers. We will also go over some resources that can help you understand how to ethically hack if you’re just getting started. It’s easier than you may think to get involved in ethical hacking.
What is Hacking?
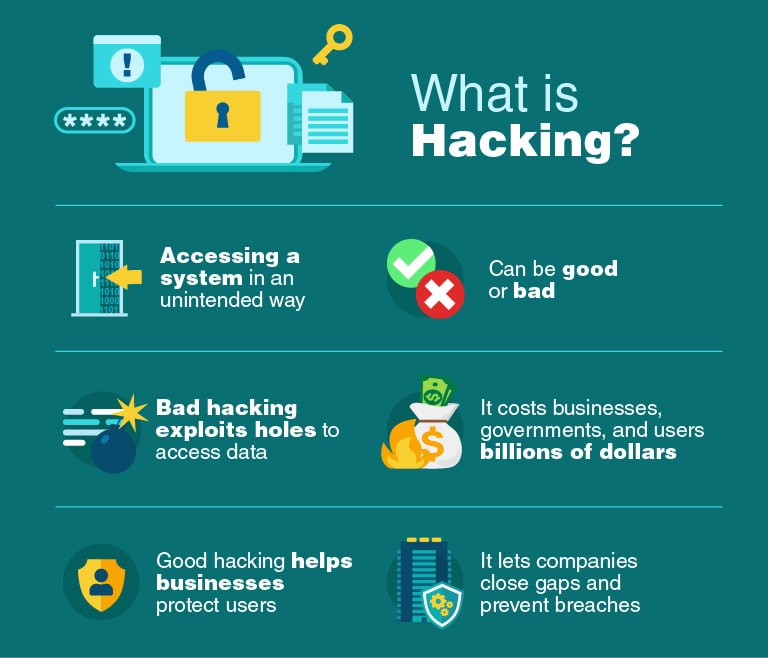
At its simplest, hacking is gaining access to a digital device, computer system, or network in an unauthorized or unintended way.
Hacking has a wide variety of applications — both good and bad — but it’s easy to see how hacking could be used for malicious purposes.
Similar to how leaving your door unlocked or your window wide open could leave you vulnerable to burglars, hackers can exploit security vulnerabilities in a device, network, or software.
The impact of malicious hacking can be very powerful. Cybercrime is projected to cost nearly $100 trillion between 2018 and 2029.
Some businesses have been hit by cyber attacks more than once, which means there's a surprising 1 in 5 chance that your business could face a cyber incident.
In 2023, the worldwide average cost for a data breach reached $4.45 million, a 15% increase over the previous three years.
Given these statistics, it’s no wonder that the word “hacking” makes many people nervous. However, there is a whole different side to hacking that is gaining more recognition in recent years: ethical hacking.
Ethical hacking is one of the most effective ways for a business to protect itself from vulnerabilities that could be exploited by black hat hackers for malicious purposes.
What is Ethical Hacking?
An ethical hacker, also known as a white hat hacker, is a cybersecurity expert who tries to find security vulnerabilities to gain access to a digital device, computer system, or network.
Sounds like any other kind of hacking, right?
The difference is that a white hat hacker uses their hacking skills to help companies find ways to strengthen their security. A black hat hacker uses hacking skills to exploit weaknesses for personal gain.
An ethical hacker only starts hacking after receiving explicit permission from the owner.
The goal of ethical hacking is to evaluate the existing security system and find ways to fortify its processes and systems. When an ethical hacker finds vulnerabilities in a company’s software, the company can then resolve the issues before a malicious hacker can exploit them.
If you are still confused about the difference between black hat and white hat hackers, it can be helpful to imagine the system being hacked as a physical building. Consider the following examples.
Example 1: Black Hat Hackers

Late one night, a group of people sneaks into a museum without setting off the alarm. They avoid detection by sneaking in at the perfect time while the security guards are changing shifts.
The group manages to steal several rare and expensive paintings and get away without being caught. They make a large amount of money by selling the paintings on the black market.
It’s pretty obvious that this scenario describes illegal and malicious activities. This example is similar to how a black hat hacker could bypass a business’s cybersecurity system to gain unauthorized access to confidential files in order to sell the illegally obtained information.
Black hat hackers are those who hack illegally for self-gain or malicious purposes. This includes anyone who steals, leaks, or accesses data, or disrupts computer devices and systems, for malicious intent, financial gain, or any other motive.
The term “black hat” stems from old western movies where the criminal would be identified by his black attire and the hero would be recognized by his white hat.
Example 2: White Hat Hackers

A museum wants to know how well its security systems function. The museum director is concerned that the museum may be vulnerable to thieves but doesn’t know the best way to improve security.
The museum director hires a security expert to help detect vulnerabilities in the system. The security expert will recreate a real-life scenario by trying to break into the museum. The security expert and the museum director both sign a written agreement.
The security expert is able to break in one night by bypassing the alarm and avoiding the security guards while they change shifts.
The following morning, the security expert delivers a report to the museum director explaining how he was able to sneak in and outlining ways that the museum could fix the vulnerabilities that he identified.
In this example, no laws were broken and no malicious activity occurred. This is similar to how a white hat hacker can use ethical hacking to help businesses improve their cybersecurity and avoid future malicious hacking.
It’s easy to see how true white hat hackers are completely different from black hat hackers. But what about scenarios where things aren’t so black and white?
There are other kinds of hackers who don’t have malicious intentions but don’t hold themselves to the same moral standards as true ethical hackers. We call these people gray hat hackers.
Example 3: Gray Hat Hackers

An art-loving security expert is concerned that a local museum doesn’t have strong enough security to protect its rare collection. The security expert writes a letter to the museum director but receives no response.
The security expert is worried that valuable paintings will be stolen if the museum’s security isn’t improved soon. To prove his point, the security expert disables the museum’s security alarm and sneaks into the museum.
The security expert doesn’t break or harm anything. Instead, he leaves an anonymous letter on the museum director’s desk explaining how he was able to bypass the security system and outlining ways to improve the museum’s security.
If no changes are made, the security expert plans to announce the museum’s security flaws to the public in the hopes that the museum director will be forced to finally improve security.
This example makes it clear how the line between black hat and white hat hackers can get blurry. Ethical hacking is about more than just having good intentions.
As we will see later on, an unauthorized intrusion is still an unauthorized intrusion regardless of whether or not the hacker was trying to be helpful.
Although all hackers draw from the same skills and knowledge, true ethical hackers only use their abilities to gain access to systems with the explicit permission of the owners.
Types of Ethical Hacking
Okay, so now we know how to be an ethical hacker and how companies can benefit from hiring one. But what do ethical hackers actually do?
There are a wide range of hacking tools and techniques that are commonly used by white hat hackers. Ethical hackers often specialize in certain domains, but most highly skilled hackers are flexible and constantly learning new strategies.

Vulnerability assessments, penetration testing, and red teaming are three terms that are often confused with one another. They actually represent three completely different approaches that ethical hackers can take. We will discuss them in more detail below.
Each one of these domains can take years to master, and — like the cyber world — is constantly evolving.
I. Vulnerability Assessment
A vulnerability assessment (VA) is a method used by ethical hackers and other information security experts to identify, rank, and communicate any vulnerabilities present in a system.
Security researchers, hackers, and end-users can all play a role in finding vulnerabilities in a company’s software, network, and hardware.
No software is perfect, and with every update or new release there are bound to be some bugs. Because of this, most reputable software and hardware development companies recognize the value of frequent vulnerability assessments.
A company may hire an ethical hacker to perform a VA in order to find and repair any problems with the software before they can be exploited by a malicious hacker.
If a software vulnerability isn’t quickly addressed and dealt with, the consequences can be catastrophic. It is therefore in the best interest of all software vendors to discover and address vulnerabilities before criminal hackers do.
Although each VA can vary in scope, timeline, and approach, most ethical hackers follow these four main stages:
- Create a thorough catalog of all resources and assets in the system.
- Rank the assets by their value or importance to the overall system.
- Find and define any existing or potential vulnerabilities in each asset.
- Work with the company to fix all security issues that were identified in the assessment.
The main difference between a vulnerability assessment and other common ethical hacking techniques is that vulnerability assessments do not recreate a real-world hacking scenario.
In a VA approach, the client and the ethical hacker usually work closely together throughout the entire process.
The client provides the ethical hacker with lots of information and access to resources before the assessment begins, rather than having the ethical hacker gather information from the outside.
Finding Vulnerabilities
There are many tools that hackers use in a vulnerability assessment, often including programs that scan the system environment, analyze network protocols, and audit Android or web application security.
Another way to find vulnerabilities is by analyzing the source code. However, this is probably the most tedious way to find vulnerabilities, and you need to have access to the source code, which is not always given.
A popular way to find vulnerabilities is via a technique called fuzzing. Fuzzing is when you purposefully interfere with a program and its input in order to make it crash, which tends to help reveal vulnerabilities.
One common fuzzer is a program called Radamsa, which has been used to find a vulnerability in Apple QuickTime that allowed remote attackers to create a denial of service (DoS) attack via a corrupted movie file.
II. Penetration Testing
A penetration test is a method used by ethical hackers to test the defenses and security procedures of a device, network, or system to find any vulnerabilities that can be exploited.
Penetration testing is what most people think of when they picture an ethical hacker. The ethical hacker has to get into the mindset of a black hat hacker and simulate a real-world attack.
Although vulnerability assessments can usually cover a wider range of information, penetration testing is a more realistic way to evaluate specific system weaknesses.
The difference between the two approaches comes down to breadth vs. depth — and this difference is why the two methods are often used together.
There are two types of penetration tests:
- White box test: Before the penetration test, the ethical hacker is given detailed information about the system being tested. This often involves the hacker performing a vulnerability test. The penetration test is then performed after the ethical hacker has been given an inside look at the system.
- Black box test: The ethical hacker is given little or no information about the system before starting the penetration test. This is usually done to recreate a real-world scenario and find out how much damage could be done by a malicious hacker from the outside. In this case, the ethical hacker has to perform reconnaissance on their own.
If you were an ethical hacker performing a penetration test, you would need to go through the following steps:
Phase 1: Intelligence Gathering
This stage involves gathering as much information about a target as possible. This information will help you design and execute your attacks in the subsequent phases.
Good intelligence gathering enables you to determine what entry points and potential weaknesses exist in a system. Entry points can be physical (e.g. service door), electronic (e.g. login prompt), or human (e.g. John M. the receptionist).
There are four categories of intelligence gathering:
- Open Source Intelligence (OSINT): Researching publicly available information about a target.
- Passive Intelligence: Gathering information in a way that can’t be detected. This is usually limited to caches or archived information.
- Semi-Passive Intelligence: Gathering information while trying to remain undetected by hiding or camouflaging your actions to look like normal internet traffic on the target network.
- Active Intelligence: Gathering intelligence so that your actions should trigger alerts and alarms. This allows you to see how your client’s security systems detect attacks and defend themselves.
Phase 2: Scanning
After gathering as much information as possible, you will begin to probe the system to understand how it behaves and find out how it will respond to an attack.
You will probably take advantage of software tools to scan the target’s network and infrastructure. You might want to monitor the network over a period of time to gather as much data as possible.
You may also spend time inspecting and analyzing the software’s code while it is static and while it is running, which is called dynamic analysis.
Phase 3: Gaining Access and Exploiting
In this phase, you will attempt to enter and exploit the vulnerabilities that you have discovered.
Here are some techniques that you might use during a penetration test to try to gain entry:
- Bypassing network or web application firewalls
- Exploiting cloud services
- SSH attacks
- Exploiting poor or default passwords
- SQL injections
- Cross-site scripting
- Denial of Service (DoS) attacks
- MAC address spoofing
You may also use social engineering to gain access. This involves misleading or manipulating people, typically employees of the company, to infiltrate the environment.
Examples of social engineering include:
- Phishing attacks
- Vishing, or impersonating a company employee
- Tailgating, where the hacker manipulates an authorized person into giving restricted access
- Quid pro quo, where the hacker poses as technical support
In order to successfully exploit any vulnerability, you have to first evade or bypass any countermeasures or defense mechanisms that might be present.
As part of this phase, you can also try to assess how much damage can be done by exploiting the vulnerability.
You may try to see if you can steal data, intercept traffic, or crash processes. However, take care not to overstep the boundaries of your ethical hacking agreement with the client.
Phase 4: Maintaining Access and Covering Tracks
The goal of this fourth phase is to find out how long you can maintain your connection without being detected.
Some kinds of attacks take place over the course of days, weeks, or even months. You may want to see if you can hide the intrusion and maintain access over a period of time.
Phase 5: Analysis and Report
At the end of your penetration test, you will create an in-depth report of everything that you learned during the test.
This includes a description of all vulnerabilities discovered, how critical they are, how they can be exploited, possible consequences, and recommendations for how to improve security.
III. Red Teaming
Red teaming is similar to a standard penetration test, with a few important differences.
A red team is a group of ethical hackers or cybersecurity specialists who test a specific product, service, or physical facility to test the environment’s defenses.
A red team tries to recreate a real-world invasion as much as possible. Because of this, the majority of the company’s IT and security teams aren’t given details about the test beforehand unless absolutely necessary.
The test often takes place over a longer period of time than other methods. Red teams usually use a combination of software tools, social engineering techniques, and exploits of the physical environment.
Benefits of Ethical Hacking
On the surface, it might seem crazy for a company to hire someone to try to breach their own system. But getting into the mindset of a black hat hacker is the only way for a business to truly test their defenses.
A company that does not want to hire an ethical hacker has to rely on having a perfect defense for every possible attack. This leaves the company at a constant disadvantage.
Even if a company has the best defenses in the world, the reality is that a hacker only needs to find one weak spot to compromise the whole system.
It’s nearly impossible to find out what that weak spot is without putting your defenses to a realistic test. A person who knows how to ethically hack can save a company a significant amount of time, money, and effort.
Imagine that an IT company is designing new software for the market. They are on a tight schedule, but skipping security testing could have serious consequences in the future.
Which is easier: including every kind of defense imaginable so that the software is immune to every possible attack, or hiring an ethical hacker to identify the software’s most vulnerable areas?
Consider the following real-world example of what can motivate an organization to work with ethical hackers:
- In 2017, a ransomware attack known as WannaCry compromised dozens of hospitals across the UK. Hospital employees were locked out of their computers, and over 19,000 appointments had to be canceled. It’s estimated that the attack cost the UK’s National Health Service (NHS) £92 million in IT repairs and lost revenue. Following the attack, the UK’s National Health Service created a new Security Operations Center with £20 million in funding to improve and evaluate security using ethical hacking.
Adding an ethical hacker to the software design team makes the process of security testing faster, more efficient, and more effective.
That means that a company that hires someone who knows how to ethically hack is both saving money and creating a stronger product.
What Do Clients Look For in an Ethical Hacker?
When a company hires someone who knows how to ethically, they are looking for someone with cybersecurity expertise who can fully take on the perspective of a malicious hacker in order to replicate realistic attacks.
Ethical hackers need to have advanced knowledge about the methods, skills, and mindset that black hat hackers use to compromise security defenses.
Companies are also looking for someone who is professional, communicative, and transparent. Companies often have to place a lot of trust in ethical hackers. It is a role that comes with a lot of responsibility.
Ethical hackers have a responsibility to fully inform the company of everything that they discover during testing.
Ideally, the ethical hacker will also work with the company to ensure that all problems and vulnerabilities are safely resolved after the testing is complete.
Is Ethical Hacking Legal?
Ethical hacking can be a legal gray area. In some jurisdictions, laws on ethical hacking are ambiguous, unclear, and don’t cover all possible scenarios. In others, ethical hackers have to stay within strict legal frameworks that outline what’s acceptable and what isn’t.
Both hackers and companies must take steps to protect themselves and make sure no laws are broken.
Conditions for Legal Hacking

In general, the best way for both parties to make sure they are legally in the clear is to sign a written agreement that defines the job that the ethical hacker is being hired to do.
One of the main differences between legal and illegal hacking is whether the hacking was authorized or unauthorized.
The written agreement is proof that the ethical hacker is legally authorized to try to exploit the company’s security vulnerabilities and gain access to the system.
Before hiring an ethical hacker, companies must also do their research and make sure that they are not asking the hacker to do anything illegal.
Organizations may be breaking the law by asking hackers to access confidential customer data without getting customers’ permission.
For a company hiring an ethical hacker, a written agreement can be an opportunity for the company to make sure their hacking request is legal and create proof of what exactly they gave the hacker permission to do.
Meeting the following four conditions is the best way for both parties to protect themselves and avoid legal consequences for ethical hacking:
- The ethical hacker and client both agree on and sign a statement of work (SOW) that describes the goal of the ethical hacking, what the hacker is being asked to do, what actions the hacker is allowed to take, what the hacker will deliver to the client when the project is complete, and any boundaries and limitations given to the hacker.
- If the ethical hacker may be exposed to confidential information, the hacker should be asked to sign a non-disclosure agreement so that private or sensitive information is properly handled.
- Both parties should sign a liability release document that frees the ethical hacker from any responsibility in case of service interruptions or problems due to authorized actions taken during the ethical hacking engagement.
- The ethical hacker should make every effort to be as transparent as possible with the client. Full disclosure is one of the most important principles of ethical hacking.
Unauthorized Ethical Hacking — Is It Legal?
Okay, so a written agreement is great and all. But what about situations that aren’t so black and white?
Imagine a white hat hacker who unexpectedly runs into a security flaw on a company’s website. She tries to assess the security flaw to find out whether she should try to report it to the company.
While doing so, she unintentionally gains access to the website’s confidential database. She quickly and privately informs the company of her discovery and even gives them some ideas for how to fix the problem.
To her surprise, instead of being thanked and rewarded by the company, she is hit with legal charges for her unauthorized access to the system’s database.
Unfortunately, there have been multiple real-world examples of this very scenario. Even though the hacker’s intentions were good, the law doesn’t always take intentions into consideration.
Things get complicated when you consider the fact that not all ethical hackers are directly hired by a company. Instead, some white hats act as vigilantes. They spend their time trying to find and report security flaws that companies have failed to fix themselves.
They often have noble intentions, with their main goal being to make the world a more secure place. In legal terms, this is sometimes called good faith hacking.
Security researchers may also use hacking techniques to evaluate security flaws in networks, devices, or software as part of their research.
Bug bounty programs and vulnerability disclosure programs (VDPs) can offer some legal protection to ethical hackers.
A bug bounty program is a reward system offered by a software developer or website to any white hat hacker who discovers and reports a vulnerability to the company.
Typically, bug bounty programs are explicitly defined and outlined by the company to the public in writing. This can act as a written agreement and provide an area of safe harbor to ethical hackers and protect them from civil or criminal charges.
Vulnerability disclosure programs (VDPs) are similar to bug bounties, but don’t offer financial incentives. They create a secure channel for white hat hackers and security researchers to report vulnerabilities discovered in good faith.
As cybercrime becomes a growing threat to businesses in the digital age, more and more organizations are announcing their own VDPs.
Many companies recognize that VDPs and bug bounty programs can be the best way to improve their security and encourage hackers to report their discovery rather than publicly announcing the vulnerability or exploiting it.
If you are interested in getting involved in bug bounties, the most important thing is to read the terms and conditions of the program very carefully.
Ethical hackers must make sure that their actions are completely covered by the written terms of the program to protect themselves from legal consequences.
Real-World Examples of Ethical Hacking
Let’s go over some real-world examples of ethical hackers and the good and bad consequences that they faced for their hacking activity.
These examples help explain how ethical hacking can be legal or not depending on the circumstances and context.
Dave Dittrich
University of Washington software engineer and cybersecurity researcher Dave Dittrich is best known for his research on Distributed Denial of Service (DDoS) attack tools.
After a series of large-scale DDoS attacks around the world caused panic in the late ‘90s and early 2000s, Dittrich began investigating compromised hosts using ethical hacking techniques.
His research sometimes forced him to access personal information from account holders with compromised systems.
Dittrich frequently speaks about how his hacking activities could have landed him in serious legal trouble. Even though his intentions were good, some of his actions could have been viewed as unauthorized intrusions.
Luckily, Dittrich has never faced any legal consequences for his hacking. Part of the reason that Dittrich’s actions were considered ethical hacking was because he worked hard to follow strict ethical guidelines.
The researcher tried to be transparent and communicative with all of the DDoS attack victims involved in his research. He also informed government authorities of his activities and all of his research findings.
Dittrich is now a big advocate of ethical hacking to combat malicious hacking tools. He believes that ethical hackers need to work together to create and follow a strict hacking code of ethics to protect themselves and others.
Glenn Mangham
The story of British software development student Glenn Mangham is a great example of the risks involved in unauthorized hacking even if your intentions are good.
In 2011, Mangham noticed some security vulnerabilities in the Yahoo! search engine. Using hacking techniques, the software development student explored the vulnerabilities in more detail.
He put together a report on his activities and findings, which he then sent to Yahoo! along with recommendations for how to improve the security.
Yahoo! considered Mangham’s actions to be ethical hacking. The company thanked him for his report and even gave him a reward of several thousand pounds for his efforts.
However, Mangham’s luck changed later that year when he tried the same routine with Facebook. Encouraged by his previous success, this time he took more extreme actions on his hunt to find vulnerabilities.
Mangham successfully hacked into the account of a Facebook employee, which he used to gain access to several Facebook servers.
While exploring security vulnerabilities that he encountered, Mangham downloaded confidential source code from the Facebook servers onto his home hard drive. He claims that he was trying to put together a report similar to the one he created for Yahoo! in order to help Facebook improve their security.
Unfortunately, Facebook saw things differently. The company found evidence of an unauthorized breach and went straight to the FBI, who tracked the intrusion back to Mangham.
When British authorities confronted the software development student, he immediately admitted what he had done and tried to explain his intentions, but it was too late.
Facebook did not view Mangham’s actions as ethical hacking. The company’s lawyers argued that unauthorized access was never harmless and should be punished regardless of the hacker’s intentions. Mangham was sentenced to eight months in prison for his actions.
Charlie Miller
Charlie Miller is an American cybersecurity researcher and well-known ethical hacker who has previously worked for the NSA, Twitter, and Uber.
Miller has been publicly rewarded multiple times for discovering critical security flaws in popular devices and software. He has never faced legal consequences for his hacking because he follows a strict code of hacking ethics.
Here are some examples of what Miller has accomplished with ethical hacking:
- 2007: Miller discovered a critical vulnerability in the Safari iPhone application that could be used to hack and hijack iPhones. Apple was able to successfully fix the problem after Miller reported his findings to the company.
- 2008: A hacker conference in Canada awarded a $10,000 prize to Miller for demonstrating how a security vulnerability could be used to hack a MacBook Air in less than 2 minutes.
- 2009: Miller exposed a security flaw in iPhone’s text message processing system that left iPhones vulnerable to DDoS attacks.
- 2011: Miller found a critical vulnerability in the battery chips of Apple laptops that could easily be exploited to infect the laptop with malware or damage the device.
- 2012: Miller exposed a method that hackers could use to bypass Google’s mobile app store protections, making it possible for hackers to create malicious Android apps to steal data, send spam, or take money. Google was able to repair the problem with Miller’s help.
- 2015: Charlie Miller and fellow ethical hacker Chris Valasek discovered a vulnerability in the Jeep Cherokee’s internet-connected entertainment system. With only the car’s IP address, the two hackers were able to remotely control the car’s engine, breaks, steering wheel, and more by sending commands to the car's internal Controller Area Network (CAN). Fiat Chrysler, which owns the Jeep Cherokee, was able to quickly create a security patch after Miller and Valasek disclosed the issue.
How to Become an Ethical Hacker
The real-world examples in the previous section show how a hacking code of ethics can make the difference between a hacker’s actions earning a $10,000 reward or a prison sentence.
Following ethical hacking guidelines is the only way to safely and legally get started as a hacker. It is also much easier to make money as an ethical hacker than as a black hat or gray hat.
A growing number of companies around the world are realizing the importance of investing heavily in cybersecurity. This rising awareness means that the field of information security is growing faster than ever.
With the current booming demand for skilled ethical hackers creating jobs and driving up salaries, the outlook for aspiring white hat hackers has never been brighter.
There are even examples of black hat hackers switching sides because there are so many more opportunities for ethical hackers than in the past.
One of the most famous cases is Kevin Mitnick, an incredibly talented American black hat hacker who is believed to have gained unauthorized access to hundreds of devices and networks over several decades.
Mitnick evaded authorities for many years, but he was finally caught, arrested, and sentenced to five years in prison after a high-profile FBI pursuit in 1995.
Today, Mitnick is an extremely successful security consultant who has provided ethical hacking services to some of the largest companies in the world. The former black hat hacker’s story is both fascinating and inspirational to anyone who is considering a career in hacking.
Thanks to a growing awareness about the benefits of ethical hacking, there are a ton of resources and opportunities to help teach people how to ethically hack.
Making Money as an Ethical Hacker
Ethical hacking is a fun and interesting field to get into, and it can also be a great way to make money. There are two main paths that ethical hackers can take to earn a living.
Many ethical hackers are hired by businesses or consulting firms. Here are some common job titles that attract ethical hackers:
- Information Security Analyst
- Cyber Security Analyst
- Security Engineer
- Penetration Tester
- Information Security Manager
- Cyber Security Researcher
Payscale reports that Certified Ethical Hackers (CEH) have an average salary that varies from $63,000 to $152,000 for men and from $64,000 to $159,000 for women.
Here are some average salary ranges in 2024 for an ethical hacker in the US based on location:
- Washington, DC: $108,072 - $135,646
- New York, New York: $114,072 - $143,176
- Atlanta, Georgia: $95,353 - $119,682
- San Antonio, Texas: $93,626 - $117,514
Some ethical hackers prefer to work solo rather than join a company. These hackers usually make their money through bug bounties.
Bug Bounty Programs
Many website owners and software developers recognize the value of offering people motivation to disclose any bugs or vulnerabilities that they encounter rather than exploiting them or announcing them publicly.
A bug bounty is a reward offered by a website or software developer to users and ethical hackers who find and report a bug to the company. The biggest rewards are usually offered for the discovery of a bug that could potentially be exploited by a malicious hacker.
The legal protections for bug bounty programs are discussed in more detail earlier in this article. In general, the most important thing is to read the terms and conditions of the bug bounty program carefully and follow the guidelines given by the company.
Bug bounties can be a great way for talented ethical hackers to earn money. Here is a list of a few bug bounty programs offered by well-known companies, along with possible earnings:
- Facebook: $500 - $300,000
- Apple: Up to $1,000,000
- GitHub: $600 - $30,000+
- Google: $100 - $30,000+
- Microsoft: Up to $250,000
- Netflix: $200 - $20,000
- Uber: $250 - $15,000
- PayPal: $100- $20,000
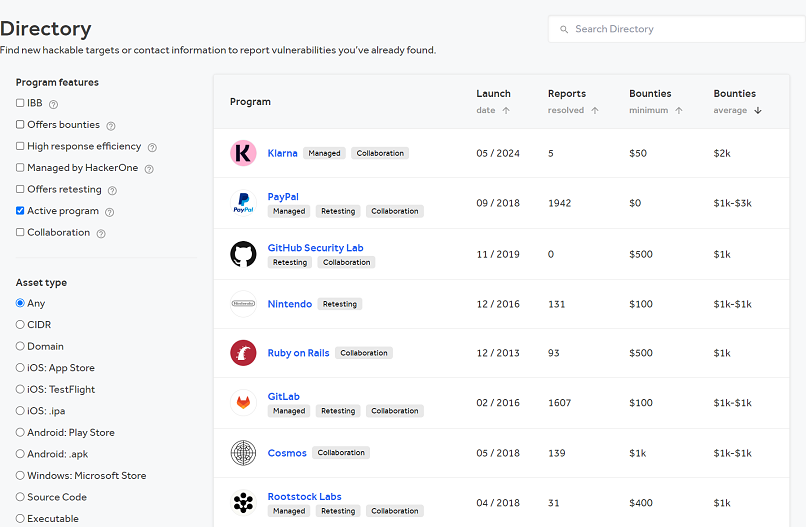
Many websites host information about their bug bounty programs on the hackerone database.
How to Get Started as an Ethical Hacker
One of the best things about ethical hacking is that it is accessible to everyone. There is no single correct way to become a great hacker.
Ethical hacking is different from many other careers where you must follow a strict, traditional path to become successful. In fact, some of the most famous ethical hackers have been completely self-taught.
Keep in mind that no one becomes a talented hacker overnight. Learning hacking skills takes time, effort, and dedication. Even experienced hackers need to constantly learn new skills because technology changes so rapidly.
If you are invested in learning and constantly improving your skills, then you are already off to a great start.
Since there are so many possible paths to take as an aspiring ethical hacker, we are going to break things down into formal and informal steps that you can take.
Formal Learning — Degrees and Certifications
There is no specific degree or major that is required for a career in ethical hacking, but taking courses in information technology, computer science, computer engineering, or even mathematics can help prepare you to enter the field.
Any degree that involves learning programming languages and software development will be the most relevant for ethical hackers.
If you lack real-world experience, one of the best ways to make yourself stand out as a talented ethical hacker is to obtain a certification. There are a few different credentials that ethical hackers can get.
Certified Ethical Hacker (CEH)
To become a Certified Ethical Hacker, you need to receive credentials from the International Council of Electronic Commerce Consultants (EC-Council).
The CEH is an entry-level certification. Obtaining it proves that you understand on a theoretical level what ethical hacking is, how it is different from non-ethical hacking, what kinds of attacks exist, and how to protect against them.
The exam is made up of 125 multiple-choice questions covering topics such as: footprinting and reconnaissance, network scanning, sniffing data, hijacking servers, SQL injection, system hacking, web application hacking, and social engineering. The exam lasts about four hours.
Certified Ethical Hacker (Practical)
After you have obtained your CEH credential, you are also eligible to take the CEH practical exam. This is an intermediate-level certification.
While the foundational CEH credential primarily focuses on showcasing your comprehension of ethical hacking methodologies and tools, the practical examination serves as a means to demonstrate your practical proficiency in effectively utilizing them.
As its name implies, you'll be putting into practice all the theories that you've encountered while obtaining CEH. The exam is more difficult than the CEH and will require about six hours of challenge solving — 20 challenges in total — on a virtual network with machines to be hacked.
Offensive Security Certified Professional (OSCP)
The OSCP certification is for ethical hackers who want to prove that they not only know how to hack but actually know how to do so according to a strict standard of ethics and business etiquette.
It's one thing to be a good hacker, but it’s another thing to be a professional and ethical hacker. To pass the OSCP you will perform a penetration test against a live simulated network with vulnerable devices.
You'll be hacking in conditions that mimic reality. At the end of your penetration test, you'll have to write and deliver a report of several hundred pages on your findings.
This is an advanced certification, but obtaining it proves that you're an outstanding ethical hacker.
Informal Learning — Skills and Resources
One of the best ways to get started is to start learning one or more programming languages. You can sign up for a formal programming class, but you certainly don’t have to.
There are many excellent free online resources for both beginner and advanced hackers to improve their programming skills. Here are a few examples:
Programming Resources
Codecademy is an interactive site that is great for beginners. You get to learn the basics of different programming languages in a practical way.
Codewars is a fun, interactive way to learn basic and intermediate coding in several popular programming languages.
Free Code Camp advertises itself as a coding bootcamp. After you work your way through the curriculum, you will have the opportunity to work on real projects for nonprofits.
You can also find some excellent free programming courses on online learning platforms like Coursera, edX, Udacity, Udemy, and even on Youtube.
If you’re new to programming and aren’t sure where to start, some of the most popular programming languages used by hackers are Python, HTML, Javascript, SQL, Ruby, and Perl.
Online Hacking Resources and Platforms
There are lots of resources out there that can help you learn how to be an ethical hacker or practice your existing skills. Here are some resources to learn basic hacking techniques and even apply hacking skills in realistic simulations:
Cybrary offers free online training courses on a wide range of hacking and cybersecurity-related skills.
Bug Hunters, made by Google, is an excellent tool for those who want to know how to ethically hack. It teaches how to write professional reports on vulnerabilities for bug bounty programs.
Hacksplaining is a fun, interactive site that teaches lessons on different hacking techniques. This is a great place to learn the basics of hacking techniques, as well as how to defend against them.
yeahhub offers security ebooks available for free on GitHub. They cover everything from “Hacking for Dummies” to “Advanced Penetration Testing.”
EnigmaGroup is a resource for potential ethical hackers to develop their penetration testing skills.
Hack This Site promotes itself as a free and legal training ground and community for hackers to test and expand their hacking skills.
Additional Hacking Resources
If you are really looking to learn how to ethically hack, these additional resource lists may be helpful to you:
- Free Security eBooks: Free hacking and cybersecurity eBooks hosted on Github.
- Online Hacking Resources Database: List of forums, blogs, YouTube channels, articles, and references on a variety of hacking skills and topics.
- Courses and Trainings: List of reputable courses and training sessions on cybersecurity topics.
- Social Engineering: Resources and materials to help you learn real social engineering techniques.
Sources:
- Estimated cost of cybercrime worldwide 2018-2029 – Statista
- What are the chances of being hacked? Eye Security: 1 in 5 – Eye Security
- Cost of a Data Breach Report 2024 – IBM
- Ethical Hacking: White Hats Making the Digital World Secure – Delhi School of Business
- Ethical hacking vs. the law – will you get arrested for a good deed? – invicti
- Salary for Certification: Certified Ethical Hacker (CEH) – payscale
- Ethical Hacker Salary in the United States – salary.com
- Directory – HackerOne




Please, comment on how to improve this article. Your feedback matters!