Tor vs VPN: Which Is Better for Anonymity & Safety in 2025?
When it comes to online security, VPNs and Tor are the most powerful tools you can use — but they provide very different functionality. Tor is an open-source tool designed to anonymize your browsing by routing your traffic through a series of nodes. VPNs, meanwhile, ensure your online privacy by routing your traffic through an encrypted tunnel.
While this distinction may seem small, it’s vital to your security and privacy that you understand the core differences between Tor and VPNs. This will help you to keep your personal data and online activity private and out of the hands of cybercriminals, corporations, and governments.
Below, I’ll dive deeper into the differences between Tor and VPNs, what they do, and how they work. I’ve also covered the different ways you can use them to help you decide whether Tor or a VPN would be the best solution for you.
My recommendation is to use a VPN, either alone or in combination with Tor. ExpressVPN has been my go-to service which proved to be very reliable, and I’ve been using it for a couple of years now. If you want to try it out risk-free, you can do so for 30 days since it offers a money-back guarantee. Editor's Note: Transparency is one of our core values at vpnMentor, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process.
Boost Your Security With ExpressVPN >>
What's the Difference Between Tor and VPN?
One of the key differences between Tor and a Virtual Private Network (VPN) is who controls the tool. VPNs are operated by private companies, which means that they are centralized. If you use a VPN, you have to trust that the VPN provider will honor its commitment to keep your data secure and private.
In contrast, Tor is an open-source network that is maintained by a community of volunteers worldwide. It is not controlled by any company or government, which means that it is more decentralized and less vulnerable to outside interference. However, you also have to trust that there are no rogue volunteers using their privileged access to steal your data.
The routing methods used by Tor and VPNs are also different. VPNs use a single proxy server and work by creating a secure tunnel between your device and the VPN. Your internet traffic is routed through this tunnel and encrypted, making it difficult for anyone to monitor or intercept your online activity.
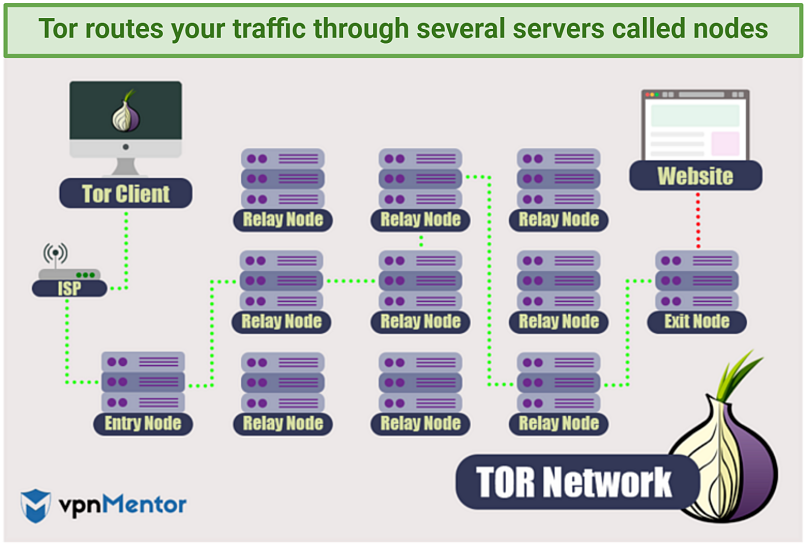
Tor, on the other hand, uses a distributed network of volunteer-operated nodes to route user traffic through multiple relays before it reaches its destination. Each relay encrypts the data traveling through it, including your IP address. This makes it much harder for anyone to trace your online activity back to your IP address. However, when your traffic is received by the last node, i.e., the exit node, it is decrypted and forwarded to the website you’re visiting.
 Note that your data is decrypted when it comes out of the exit node
Note that your data is decrypted when it comes out of the exit node
To summarize, premium VPNs are generally faster, safer, and more convenient to use. Tor, on the other hand, is slower and less user-friendly.
Tor vs VPN: When Should I Use Tor and When a VPN?
One of the main reasons to use Tor is for more online privacy. But it’s also a well-known fact that Tor has been used for not-so-ethical activities. A lot of users access the dark web with Tor, which contains content that can be dangerous. While Tor provides a level of anonymity, it’s important to note that it’s not the safest tool to use.
Tor is also slower and less user-friendly than a VPN, so it may not be the best choice for data-heavy activities like streaming or torrenting. On top of this, it was only designed to encrypt data that uses the TCP protocol. So, anything that uses the UDP protocol won’t be protected.
A VPN, on the other hand, is a good choice for activities that require extra security and privacy, such as online banking. That’s because the encrypted tunnel it creates thoroughly protects your data from prying eyes. VPNs aren’t limited to only the TCP protocol like Tor is, either. So, you can protect all your data while you’re gaming, streaming, or video chatting with friends.
However, not all VPNs are created equal. You’ll need a premium VPN that offers quality security features. I recommend looking for VPNs with a kill switch and IP/DNS leak protection to keep your data secure in case your connection drops.
On top of this, top-rated VPN services, such as ExpressVPN, offer strong encryption protocols and independently verified no-logs policies that ensure they retain no information about your online activity.
Comparison Table: Tor vs VPN
Here’s how the two stack up against each other:
| Tor | VPN | |
| Cost | Free | Affordable subscription fee, typically without a contract |
| Encryption | Yes, but only to the exit node. | Yes, end-to-end encryption. |
| Anonymity | Yes, but surveillance programs can detect when Tor is in use. | Yes, but if you opt for a secure, premium VPN. |
| Other security features | Can be used in conjunction with Obfsproxy to disguise that you’re using Tor. | Depending on the provider:
|
| Device compatibility | Windows, macOS, Linux, Android, iOS. | All these platforms, including routers and streaming devices. |
| Streaming | Tor is not recommended for streaming as the connection is too slow. | Yes, most VPNs are fast enough for streaming. |
| Torrenting | Most exit nodes block traffic to and from torrents. | Yes, but sometimes it depends on the provider. |
| Ease of use | The browser is easy to set up but often needs further configuration that requires more technical knowledge. | Depends on the provider. Most VPNs are easy to use and intuitive. |
| Speed | Slow | Fast speeds, but this will depend on the VPN provider, the server you choose and your distance to it, and other factors. |
How Do VPNs Work?
A VPN connects your device through a secure tunnel to a remote server in a country of your choice. When you send data through this tunnel, your IP address is replaced with the server’s IP. This makes it appear as though you are accessing the internet from the location of the remote server instead of your actual location.
All data that passes through this tunnel is encrypted. This effectively means it locks your data away in an impenetrable safe. Only those that have the key to open this safe (which is you and the data’s destination, like a website) can see your data. Thanks to modern encryption algorithms (or locks), it’s near impossible to break into your data.
VPNs typically offer a variety of different VPN protocols that use different encryption algorithms. For example, ExpressVPN uses an encryption algorithm called AES 256-bit, which is the same algorithm used by the government and military. Attackers can theoretically crack this with a brute force attack, but it would take an estimated 1 billion years to do so!
If a hacker or government surveillance agent got ahold of your data as it traveled across the network, they would have no way to read it. It would just look like gibberish.
To test this, I used an AES encryption generator to encrypt the phrase 'vpnMentor.' Without encryption, you can clearly see the phrase 'vpnMentor,' but when it’s encrypted, all you can see is: ‘NRRJsYVI/6HXtdnnh2BLZg==’
 You can see how AES encryption works in this example
You can see how AES encryption works in this example
These are the kind of security features that keep journalists and activists safe when they use digital communication in tumultuous political climates. But VPNs aren’t just for people in dangerous positions — they’re the key to anonymity, and security for every online citizen.
In today’s digital landscape, where third parties are constantly buying, selling, and tracking user data, a VPN helps you to maintain your privacy online. It means that companies like Google and Facebook can’t serve you tailored ads based on the websites you’ve visited, and it protects you against cybercriminals stealing your personal information.
To use a VPN, you’ll need:
- An account with a VPN provider
- The VPN provider’s client software or app installed on your device
Once you’ve set up an account with your chosen provider, you’ll need to open the client software on your computer, log in, and select a server to connect to. If you prioritize fast speeds, select a server close to your physical location.
Pros and Cons of Using a VPN
VPN Pros:
- More security: VPNs offer features such as end-to-end encryption, IP/DNS leak protection, and kill switches to make sure that all your data is protected from snoops.
- IP masking: By replacing your IP address with one from a different location, VPNs can bypass online restrictions and geoblocks.
- Avoid throttling: VPNs encrypt your data and prevent ISPs from snooping on your activity, which means they’re less likely to throttle your speeds as punishment for perceived suspicious activity.
- Full encryption: A VPN encrypts all of the data traveling to and from your device, not just data from a specific browser.
- Device compatibility: VPNs are available on a wide array of devices — you can even configure it on your router to ensure all of your internet-connected devices are protected.
VPN Cons:
- Cost: Quality VPN services require a paid subscription. However, most offer significant discounts for signing up for longer, plus a money-back guarantee if it doesn’t work for you. For example, ExpressVPN offers a 30-day money-back guarantee, which lets you test it out risk-free.
- Can be detected: Sometimes, some websites, banks, or other payment gateways can detect that you are using a VPN and flag your account for suspicious activity. Some VPNs, like ExpressVPN, allow you to obfuscate your traffic to help you avoid this.
- Speed loss: You will experience speed loss because your data needs to travel farther to get to its destination and because the encryption process takes time. That said, this difference is barely noticeable with a high-quality VPN, and it won’t affect your speed as much as Tor does, as Tor isn’t optimized for speed as some VPNs are.
- Errors and bugs: VPN software can run into errors and even crash, leaving your data unprotected. This is why you should look for a VPN which offers an automatic kill switch, as it will disconnect you from the internet in case your VPN software fails.
How Does Tor Work?
The Onion Router, or Tor, is a free network that disguises your identity by routing your data through a series of volunteer-operated servers known as nodes. Each node encrypts your data before it is forwarded to the next server. When your traffic is received by the last server (called the exit node), it’s decrypted and sent to the website you’re visiting.
Because of this multi-layer encryption, each node on the network can only see the IP address of the nodes before and after it. The exceptions to this are the entry node, which can see your real IP, and the exit node, which unlocks your encrypted data. Spies can see your traffic once it leaves the network, but not where that data came from.
However, because Tor’s nodes are operated by volunteers, anyone can set up an exit node and see the plaintext traffic that leaves it, including hackers and spies. Bad nodes typically harvest information such as login details to websites, personal information, online chat messages, and emails.
The Tor community actively hunts for and removes bad nodes using both automated tools and manual reporting. To protect yourself from bad relays on Tor, I recommend the following:
- Avoid sending private messages and sensitive information over your connection. Never log into websites unless they use HTTPS.
- Use a VPN in conjunction with Tor to encrypt your sensitive information and login details — we’ll talk about this in more detail below.
For more information on this browser and tips on how to stay safe while using it, have a look at our Tor beginner's guide.
Tor is also a doorway to the dark web, which is the part of the internet that isn’t visible to search engines like Google. The dark web is, unsurprisingly, home to criminal operations, but it’s also a haven for people who need to share information privately. Many legitimate websites have “mirror sites” with a .onion subdomain for these purposes.
For example, the New York Times operates a secure lockbox on the dark web so that whistleblowers can submit files and information without compromising their identity. Facebook has a .onion mirror site so that people in heavily-censored regions can use it to communicate.
To use Tor, you’ll need:
- The Tor browser or Android app, or
- Tails, the Tor operating system, or
- Onion Browser, the Tor iOS app.
All you need to do is download one of these options and start browsing the internet. Everything is automatically configured so you can start using the Tor network right away.
Pros and Cons of Using Tor
Tor Pros:
- It’s free: Tor is free to download and use, unlike most VPNs. While some reliable free VPNs exist, they have a large number of disadvantages making them an unfavorable option.
- Privacy: Your browsing activity can’t be linked back to you since your data is protected by several layers of encryption. Plus, because your data is relayed through several servers, it’s even harder for snoops to discover your original IP address.
- Accesses restricted content: Since the browser hides your identity, Tor is often used to access global content in countries with strict online censorship.
Tor Cons:
- Slow speed: The Tor network is very slow, which makes it less than ideal for streaming, torrenting, gaming, or any other bandwidth-heavy activities.
- Compromised nodes: The exit nodes of Tor can be manipulated by skilled individuals to spy on other users, so it’s not as safe as a premium VPN would be.
- Data leaks: Just because you’re using the Tor network doesn’t mean your data is completely obscured. If the website you are communicating with isn’t on the dark web and doesn’t support HTTPS, then your IP address and other identifying information may be visible.
- Can be detected: Your ISP and other snoops can tell if you are using Tor. Even though you’re using the network for legitimate purposes, any Tor use is viewed with suspicion and can result in speed throttling and other issues.
- Limited protection: Unless you’re using Tor’s OS, only the traffic from your browser is protected. Plus, your data is being decrypted when it reaches the exit node, so there’s no end-to-end encryption that most VPNs offer nowadays.
- Not P2P-friendly: Tor doesn’t support torrenting, in fact, most nodes block it altogether. Even in the rare cases when it is allowed, Tor’s speeds aren’t fast enough to torrent, unlike with VPNs.
Using Tor and a VPN at the Same Time
If you want to protect your connection with the strongest online privacy solution, I recommend using Tor alongside a VPN.
The VPN’s encryption protocol will prevent malevolent nodes from seeing your IP address and activity, as well as prevent your ISP and surveillance bodies from detecting the use of Tor. This will also allow you to access websites that block Tor users.
There are two ways to combine a VPN and Tor:
VPN Over Tor
For this configuration, you’ll need to first connect to the internet and then log into your VPN through the Tor network. This method requires more technical know-how because you’ll need to configure your VPN client to work with Tor.
Instead of connecting directly to the internet, Tor’s exit node reroutes your traffic to your VPN server, which eliminates the risk of malicious exit nodes (because your traffic is decrypted after it leaves the Tor network).
Although Tor’s entry node can still see your real IP, your VPN will only see the exit node’s address. Your ISP won’t be able to see that you’re connected to a VPN, but it can see that you’re using Tor. Because you can select which remote server your VPN uses, it’s easier to access specific websites that you need with this method, too.
Use VPN over Tor if:
- You want to safeguard your connection against malicious exit nodes.
- You want to hide your VPN use from your ISP.
- You are going to transmit sensitive information over your connection, like login details and private messages.
- You want to access sites that block Tor traffic.
Tor Over VPN
In this setup, you first connect to your VPN and then access Tor. Your traffic is encrypted by the VPN before it traverses the Tor network, concealing your Tor usage from your Internet Service Provider (ISP).
If anyone investigates your data before it reaches the Tor network, all they’ll see is that you’re using a VPN (unless you’re VPN uses obfuscation, like ExpressVPN). The Tor entry node will only see the IP address of your chosen VPN server, which increases your privacy.
However, your traffic is not encrypted when it leaves the Tor network, so Tor over VPN doesn’t protect you from malicious exit nodes. So, you’ll still need to be careful about sending sensitive information over your connection.
Use Tor over VPN if:
- You need to hide your use of Tor from your ISP and surveillance bodies.
- You need to hide your traffic from your VPN provider.
- You aren’t sending personal information, such as login details, over your connection.
- You want to access .onion sites.
FAQs on Tor vs VPN
Which is better for my online anonymity and security, Tor or VPNs?
That depends on your priorities, but I recommend using a VPN because it’s more convenient and secure than Tor overall, especially for less tech-savvy people. Another solution is to combine both and use Tor over VPN.
Tor safeguards your privacy by directing traffic through various layers of encryption and relays, however, your data is at risk at the exit node. VPNs, on the other hand, encrypt your web traffic from end to end and reroute it through remote servers of your choosing, simultaneously altering your IP address, making it more difficult for anyone to monitor your activities. While Tor is free and ensures a degree of anonymity, VPNs provide quicker speeds and an extensive range of security features, albeit at a price.
Are VPNs faster than Tor for torrenting?
VPNs are generally much faster than Tor for torrenting. This is because VPNs only route your torrent traffic through a remote server, while Tor routes your traffic through multiple relay nodes. This additional encryption considerably slows your connection.
Additionally, VPNs offer faster speeds because they allow you to choose from a range of servers located in different countries. Choosing a server that's closer to your physical location can greatly reduce latency and improve your torrenting speeds.
Should I use a VPN with Tor?
Using a VPN with Tor can provide additional layers of privacy and security. When you use Tor, your traffic is already encrypted and routed through multiple relays, making it very difficult for anyone to trace it back to you. However, using a VPN with Tor can add an extra layer of encryption and help hide the fact that you're using this browser.
Can Tor prevent ISP throttling as VPNs can?
Tor can help prevent ISP throttling to some extent, but it may not be as effective as VPNs. When you use Tor, your internet traffic is encrypted and routed through multiple nodes, making it more difficult for your ISP to see what you're doing online. This can help prevent ISP throttling based on your online activities, such as streaming videos or downloading large files.
However, Tor traffic is often easy to identify, which means that some ISPs may still be able to detect and throttle Tor traffic. In contrast, VPN traffic is often more difficult to identify, especially if the specific VPN comes with obfuscation, like ExpressVPN.
On what devices can I use Tor vs VPNs?
You can use Tor on Windows, macOS, Linux, Android, and iOS. There’s also a Tor operating system called Tails.
VPNs, in contrast, can be used on a wider range of devices and platforms. Aside from the above-mentioned OSs, VPNs can be also used on streaming devices like Fire Stick, smart TVs, tablets, and more. In addition, most VPN providers offer manual setup guides for other devices like routers or gaming consoles. Some VPNs also offer browser extensions that can be used with popular browsers like Chrome or Firefox.
Tor vs VPN: Final Verdict
Both VPN and Tor are recognized as potent tools that enhance online security and privacy by safeguarding the personal data of their users. For comprehensive protection of your personal information, I recommend utilizing either a VPN or employing Tor over a VPN.
My top pick is ExpressVPN, as it comes with obfuscation, robust security, and fast speeds. Plus, it's very easy to use. You can try ExpressVPN risk-free, as its service is backed by a 30-day money-back guarantee. If you end up not liking it, you can request a refund from its customer support via the 24/7 live chat within the first 30 days of subscribing.
To summarize, here are the best VPNs to use with Tor
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: Intego, Cyberghost, ExpressVPN, and Private Internet Access. However, this does not affect our review process, as we adhere to a strict testing methodology.
Your data is exposed to the websites you visit!
Your IP Address:
18.118.37.224
Your Location:
US, Ohio, Columbus
Your Internet Provider:
The information above can be used to track you, target you for ads, and monitor what you do online.
VPNs can help you hide this information from websites so that you are protected at all times. We recommend ExpressVPN — the #1 VPN out of over 350 providers we've tested. It has military-grade encryption and privacy features that will ensure your digital security, plus — it's currently offering 61% off. Editor's Note: ExpressVPN and this site are in the same ownership group.




Please, comment on how to improve this article. Your feedback matters!