Report: Cannabis Users' Sensitive Data Exposed in Data Breach
Led by internet privacy researchers Noam Rotem and Ran Locar, vpnMentor's research team discovered a data breach in THSuite, a point-of-sale system in the cannabis industry.
Our team identified an unsecured Amazon S3 bucket owned by THSuite that exposed sensitive data from multiple marijuana dispensaries around the US and their customers.
The leaked data included scanned government and employee IDs, exposing personally identifiable information (PII) for over 30,000 individuals.
THSuite Company Profile
THSuite offers business process management software services to cannabis dispensary owners and operators in the US.
Cannabis dispensaries have to collect large quantities of sensitive information in order to comply with state laws. The THSuite platform is designed to simplify this process for dispensary operators by automatically integrating with each state's API traceability system.
As a consequence of this, the platform has access to a lot of private data related to dispensaries and their customers.
Timeline of Discovery and Owner Reaction
Sometimes the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what's at stake or who's leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true.
In this case, we easily identified THSuite as the owner of the database and contacted the company with our findings.
- Date discovered: December 24, 2019
- Date owners contacted: December 26, 2019
- Date Amazon AWS contacted: January 7, 2020
- Date database closed: January 14, 2020
Example of Entries in the Database
Over 85,000 files were leaked in this data breach, including over 30,000 records with sensitive PII. The leak also included scanned government and company IDs stored in an Amazon S3 bucket through the Amazon Simple Storage Service.
The leaked bucket contained so much data that it wasn't possible for us to examine all the records individually. Instead, we looked through a handful of random entries to understand what types of data were exposed in the breach overall.
In the sample of entries we checked, we found information related to three marijuana dispensaries in different locations around the US: Amedicanna Dispensary, Bloom Medicinals, and Colorado Grow Company. Examples of these entries can be found below.
However, this breach affected many more dispensaries. It's possible that all THSuite clients and their customers were involved.
We also found photographs of government-issued photo IDs and corresponding signatures of dispensary visitors and patients alike. Additionally, there are attestations for what appears to be each patient acknowledging state laws regarding purchase and use of cannabis-based medicine.
Amedicanna Dispensary Files
The THSuite breach involved data from AmediCanna Dispensary, a medical marijuana dispensary located in the state of Maryland.
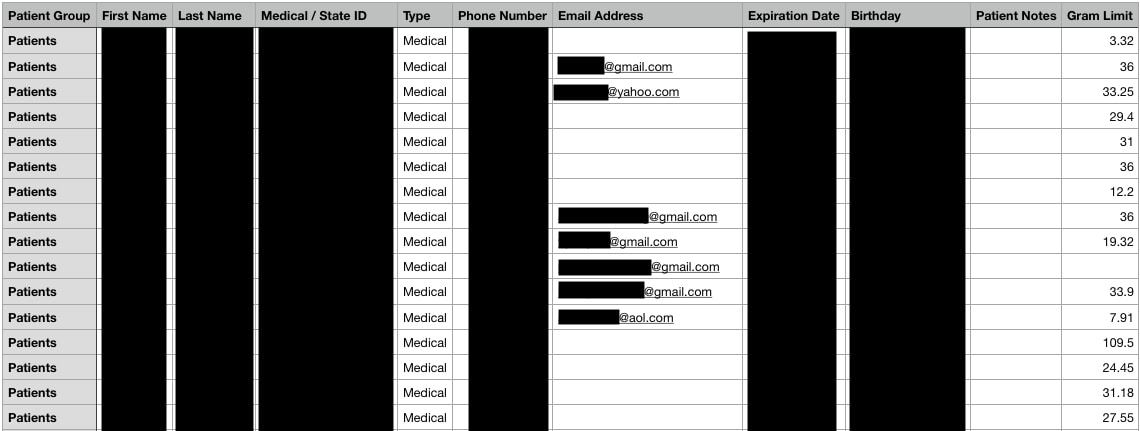
The leak exposed the following personal details about Amedicanna's customers:
- Full name
- Phone number
- Email address
- Date of birth
- Street address
- Medical/State ID number and expiration date
- Cannabis gram limit
- Signature
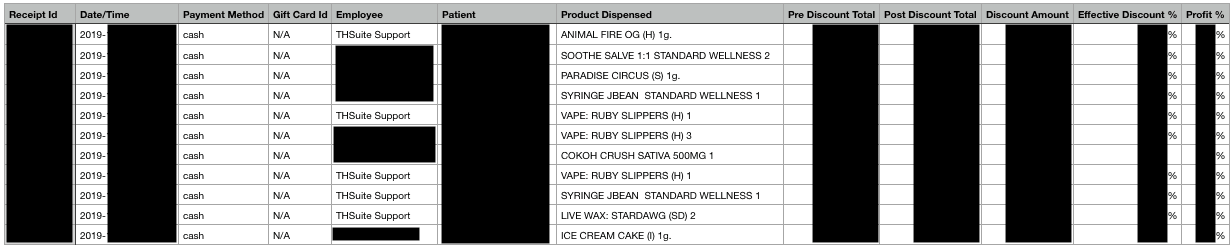
The database also included details about Amedicanna's inventory and sales. We were able to view a list of transactions with the following information:
- Patient name and medical ID number
- Employee name
- Cannabis variety purchased
- Quantity of cannabis purchased
- Total transaction cost
- Date received, along with an internal receipt ID
Bloom Medicinals
Bloom Medicinals is an Ohio-based medical marijuana dispensary with locations in Akron, Columbus, Maumee, Painesville, and Seven Mile.
The data breach exposed information about the dispensary's inventory, monthly sales reports, and compliance reports, as well as the following patient details:
- Full name
- Date of birth
- Medical/State ID and expiration date
- Phone number
- Email address
- Street address
- Date of first purchase
- Whether or not the patient received financial assistance for cannabis purchases
- Whether or not the patient opted in for SMS text notifications
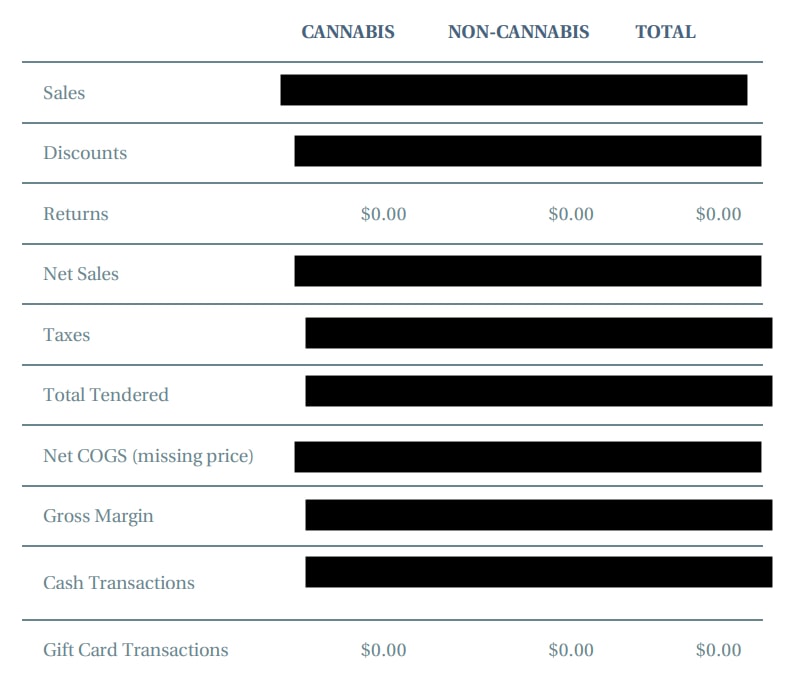
We were able to view the dispensary's monthly sales, discounts, returns, and taxes paid. The sales were further broken down by payment method and product type.
The database included a list of each cannabis product, along with a brief description, the product's supplier, and its price.
Colorado Grow Company
Colorado Grow Company is a recreational marijuana dispensary located in the city of Durango, Colorado.
The THSuite data breach exposed the dispensary's monthly sales reports for both cannabis and non-cannabis products, including gross sales, discounts, taxes, net sales, and totals for each payment type.
The leak exposed full names of dispensary employees and the number of hours they worked during each two-week pay period.

The database also included a detailed inventory list with product names, descriptions, cost breakdowns, and quantity on hand at the dispensary.
We didn't find any records with specific information about Colorado Grow Company's customers, or any other recreational marijuana users. However, since we weren't able to explore all the leaked data in detail, we can't be sure these records don't exist.
Data Breach Impact
This data breach has serious consequences for the dispensaries and their customers.
Privacy Concerns for Cannabis Users
As a result of this data breach, sensitive personal information was exposed for medical marijuana patients, and possibly for recreational marijuana users as well. This raises some serious privacy concerns.
Medical patients have a legal right to keep their medical information private for good reason. Patients whose personal information was leaked may face negative consequences both personally and professionally.
Under HIPAA regulations, it's a federal crime in the US for any health services provider to expose protected health information (PHI) that could be used to identify an individual. HIPAA violations can result in fines of up to $50,000 for every exposed record, or even in jail time.
Cannabis dispensaries exist in a legal gray area, since in the US there are major conflicts between federal and state laws regarding both medical and recreational marijuana. Even in states where cannabis use is permitted under state law, it's still prohibited under federal law.
However, most legal experts agree that dispensaries must follow HIPAA regulations just like any other health care provider.
Many workplaces have specific policies prohibiting cannabis use. Customers and patients may face consequences at work due to their cannabis use being exposed. Some could even lose their jobs, especially if they work for a federal agency.
Even without the legal risks, there's still a stigma surrounding marijuana use. Individuals may suffer backlash if their families, friends, and colleagues find out that they use cannabis.
Scams and Phishing Attacks
Hackers and scammers can take advantage of personal details exposed in the data breach about dispensary customers and employees to create highly effective personalized phishing attacks.
Exposed telephone numbers and text notification opt-in status provide the perfect opportunity for phishing attacks. Malicious actors can also use leaked emails and home addresses to target individuals.
Hackers can easily use exposed personal details to gather more personal data through social media accounts and other online sources. Detailed information about recent purchases exposed in the data breach could be used to gain access to private financial accounts.
With enough information, a malicious party could even commit identity theft, which can have very serious long-term consequences.
Impact on Dispensaries
The data breach also affects dispensaries that trusted THSuite with their private information. These dispensaries may find themselves facing major consequences because of the possible HIPAA violation created by this breach.
Another issue is that competing dispensaries may now have access to detailed information about these dispensaries' customers and inventory.
These businesses can take advantage of this to improve their pricing strategy and product offerings. They can also use leaked customer information to create targeted ad campaigns.
Affected dispensaries could lose customers as a result of the data breach. Even if the dispensaries were not directly responsible, customers might hesitate to trust these dispensaries with their personal information after it was leaked.
Advice from the Experts
THSuite could have easily avoided this leak if they had taken some basic security measures to protect the Amazon S3 bucket. These include, but are not limited to:
- Secure your servers
- Implement appropriate access rules
- Never leave a system that doesn't require authentication open to the internet
Any company can replicate the same steps, no matter its size. To learn more about how to protect your business, check out our in-depth guide on securing your website and online database from hackers.
For Affected Dispensaries
We recommend contacting THSuite directly to find out more about the company's security practices and how it plans to ensure the safety of your data in the future.
At the very least, THSuite should investigate to find out how this data breach occurred and implement new security procedures to make sure something like this never happens again.
In the future, we also recommend that you thoroughly vet any third party services you hire to make sure they follow best practices and have multiple security measures in place to protect your sensitive data.
For Affected Customers
If you are a customer or patient of a marijuana dispensary, we recommend that you speak directly with your provider to find out if they are using THSuite or have used it in the past.
If you believe your private information may have been exposed in this data breach, there are steps you can take to minimize its impact.
Read our complete guide to online privacy to learn about the techniques hackers use to invade your privacy and what you can do to protect yourself. We also recommend you use a VPN to protect your private data from cybercriminals who may try to target you after your information was leaked.
You may also want to speak your dispensary to find out how it's going to guarantee your safety and privacy in the future.
How and Why We Discovered the Breach
The vpnMentor research team discovered this breach in THSuite's database as part of our large-scale web mapping project.
Our research team scans ports to find known IP blocks. The team then searches for vulnerabilities in the system that would indicate an open database.
Our team managed to gain entry into THSuite's S3 bucket as it was devoid of any security measures or encryption. Utilizing a web browser, the team was capable of accessing all the files stored in the database.
After finding a data breach, we do our best to link the database back to the owner. We then contact the owner to inform them of the vulnerability and suggest ways that the owner can improve the security of their systems.
As ethical hackers and researchers, we never sell, store, or expose the information we encounter. Our goal is to improve the overall safety and security of the internet for everyone.
About Us and Previous Reports
vpnMentor is the world's largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users' data.
We recently found a large data breach that exposed the browsing history of mobile internet users in South Africa. We also discovered over 1TB of data leaked by Chinese online retailer LightInTheBox.




Please, comment on how to improve this article. Your feedback matters!