Report: Groupe Phosphore Exposes Data of French Small Businesses and Job Seekers
Data security experts Noam Rotem and Ran Locar, along with vpnMentor’s research team, discovered a breach in two databases belonging to the French technology and business group Groupe Phosphore.
The databases in question had indices named after two Groupe Phosphore brands: Henrri, a free billing and invoicing platform for small and midsize businesses (SMBs); and Rivalis, a professional support network and consultancy firm for business leaders.
The leak exposed sensitive data belonging to Groupe Phosphore, their brands, employees, and job applicants. It also exposed data of businesses within the Groupe Phosphore support network and clients using their software in France and Belgium.
This compromised the privacy of not just of the businesses involved, but also private individuals.
The implications for such a data breach are far-reaching and of major concern to all involved.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the database are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. Our team needs to be thorough and make sure everything we find is correct and true. Occasionally, the affected parties deny the facts, disregarding our research or playing down its impact.
In this instance, Noam, Ran, and the team initially suspected the data breach was confined to one Groupe Phosphore brand, Rivalis. But after some investigation, it became clear the scope of the breach was much wider and involved two separate databases containing different forms of information.
- Date discovered: 7/10/19
- Date company contacted: 10/10/19
- Date of 2nd contact attempt: 13/10/19
- Date of Response: 19/11/19
- Date of Action: 20/11/19
Example of Entries in the Database
Groupe Phosphore is a huge organization working within many industries, primarily in France. They claim a customer base of 160,000 users and a network of 4,200 professionals across their brands, with capital exceeding €8 million.
One of the exposed Groupe Phosphore databases affected people and organizations across France, as well as some in Belgium, containing almost 14 million records and totaling 17.2GB of data. Most of this data belonged to indices named after two Groupe Phosphore brands: Henrri & Rivalis.
This is a huge amount of sensitive information to be leaked. In one database, we estimate the details of 27,286 SMBs were exposed in indices belonging to Henrri, along with 339,787 private individuals from an index named after Rivalis.
The data our team viewed from each Groupe Phosphore brand differed somewhat, depending on the function of the affected database and the brand it belonged to.
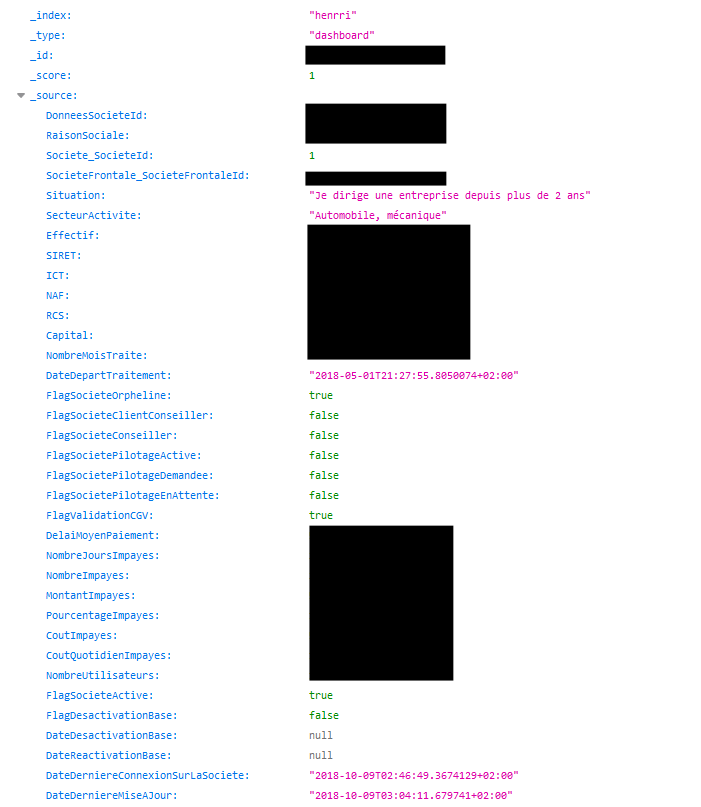
For example, as a billing and invoicing platform, Henrri’s indices contained sensitive financial data from French and Belgian SMBs using the platform.
This included:
- Company ID numbers
- Business names
- Overview of a business's position and health (details provided by the customer)
- Details about the company owners: their status/position, phone number, name, email
- Business sector & industry
- Number of employees
- SIRET, ICT, NAF, RCS numbers for French business and governmental services
- Corporate capital value
- The average length of payments outstanding/received
- Details of debt owed by the client (amount, cost, length, etc.)
- Client email address(es)
- Postal codes
- Monthly fiscal details such as goods & workforce revenues
- Total revenue numbers & revenue of invoices and quotes
The following screenshot shows an example of exposed data, belonging to a company in the automobile industry.
Most of the data from the index named Rivalis was apparently linked to a job position within the company. This included the personally identifying information (PII) data of people applying to the position and candidates that Rivalis seemed to have approached for the role.
In some cases, the data originated from job-seeker profiles on external websites. This means the breached Groupe Phosphore database also exposed individuals with no direct link to the company or its brands.
PII Data of candidates viewed included:
- Resume details
- Gender
- Full name
- Email address
- Origin of resume (external recruitment websites)
- Marital status & children
- City of Residence
- Phone number
- Interview details
- Their professional qualifications
Below is an example of the data viewable from a job applicant in the "Rivalis" index, displaying the PII exposed. The resume text revealed additional personal information about the candidate that malicious hackers and criminals could exploit.

An additional dataset originated from customers making complaints appearing to be directed towards Rivalis regarding their service offer via email.
One of the databases also contained data from Sirene.fr, a public database of businesses registered in France.
Data Breach Impact
The data exposed in this breach would have had far-reaching implications for all parties affected: Groupe Phosphore, their brands, clients, and members of the public in France.
The varied nature of the data exposed presented many opportunities for hackers and criminals to exploit it for illicit financial gain.
For Groupe Phosphore, Henrri, and Rivalis
The biggest impact of this data breach for Groupe Phosphore is reputational. Such a large exposure of private client data can justifiably cause a lack of trust amongst clients, partners, and customers.
It also casts doubt on their overall data security policies across every brand under the Groupe Phosphore umbrella: 15 businesses in total, with a network spread across France.
The Henrri data compromised the privacy of their clients, who would have provided sensitive financial details in strictest confidence. Meanwhile, much of the job seeker data found in the "Rivalis" indices weren’t even provided knowingly.
Our team viewed PII belonging to people whose resumes were hosted on external recruitment sites.
The data relating to customer complaints could create another headache for Rivalis and Groupe Phosphore. By revealing the complaints and negative feedback received from customers, it gives their competitors an opportunity to undermine Groupe Phosphore’s business and entice customers away with better value propositions.
Potential new customers may also be less inclined to join the Rivalis network, based on the complaints made and this breach in data privacy.
This all makes Groupe Phosphore vulnerable to legal and financial actions, due to breach of privacy: fines, GDPR investigations, and lawsuits, loss of revenue, industrial espionage, and more.
For Groupe Phosphore clients
The companies affected by this data breach were SMBs, who usually have fewer resources to protect themselves against fraud. As a result, any exposure of their private financial data could be devastating if exploited by criminal hackers and gangs.
Also less financially stable than bigger companies, SMBs can't afford their private financial data being leaked and used to defraud or steal from them in any way. Aside from any loss of revenue or capital, even the cost of investigating a case of fraud can be too much for some SMBs.
If malicious and criminal hackers discovered this database, they would have plenty of opportunities to target the affected SMBs and their owners with various forms of attack.
They could also sell the data on the Dark Web for further exploitation by an infinite number of criminal organizations.
Aside from criminal concerns, the breach presents major privacy and competition issues for the SMBs affected. With so much otherwise private and very sensitive financial details exposed, competitors can use this information to undermine Groupe Phosphore’s clients’ businesses and capture their market share.
For Job Applicants
For the job seekers who had their PII exposed in the Rivalis-named indices, this information could be used against them in fraud and identity theft.
Email addresses, names, and phone numbers are enough PII for criminals to start building a profile of a victim, extract further personal information, and target them for financial fraud.
With the data exposed in this database, cyber-criminals could build convincing phishing campaigns - creating imitation emails of real businesses to trick targets or embed their device with malicious software like malware or ransomware.
In this case, victims might provide private information like social security numbers, financial account details, or passwords and usernames to criminals posing as Rivalis or similar businesses.
The breach also compromised the job security of those affected. Job seekers currently employed often don't want their employer to know they're looking for a job elsewhere. With this information in the public domain, it makes them vulnerable to a negative reaction within their current workplace.
Advice from the Experts
Groupe Phosphore could have easily avoided this leak if they had taken some basic security measures to protect the database. Any company can replicate the following steps, no matter its size:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
We also suggest Groupe Phosphore not host the data of separate brands on a shared database. This minimizes the impact of a breach, confining it to one brand or company.
For Groupe Phosphore Clients
If you’re a client of Groupe Phosphore or Henrri, contact them and find out if your details were exposed. They should be able to provide details of the steps taken to close the data breach and resolve any issues related to it.
In the future, thoroughly vet any 3rd parties to whom you provide sensitive data and ensure they’re following the strictest data security protocols.
For a more in-depth guide on how to protect your business, check out our guide to securing your business's website and online database from hackers.
For Rivalis Job Applicants
If you applied for or been contacted about a job at Rivalis or another Groupe Phosphore brand, contact them and confirm the steps they’re taking to protect your data.
If you’re concerned about how this breach, or data vulnerabilities in general, might impact you or your business, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered this Breach
The vpnMentor research team discovered the breach in Groupe Phosphore’s database as part of a huge web mapping project. Our hackers use port scanning to examine particular IP blocks and test open holes in systems for weaknesses. They examine each hole for data being leaked.
When they find a data breach, they use expert techniques to verify the database’s identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
Our team was able to access this database because it was completely unsecured and unencrypted.
Groupe Phosphore used an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. This is especially true when the company's data breach contains such sensitive and financial information.
These ethics also mean we carry a responsibility to the public. Groupe Phospore clients and users must be aware of a data breach that impacts them also.
Company's reply
A representative of Groupe Phosphore reached out to our team on November 22nd 2019.
The group denies that Henrri and Rivalis have any responsibility or ownership over the data that was leaked, specifically stating that "Henrri and Rivalis are not concerned about data treatment. The company responsible for data treatment is BM EST (groupe Phosphore)."
Pertaining to the two indices mentioned earlier and located in the database, it was alleged that one was inaccurately labeled by the "individual responsible for conducting some statistical analysis on the test server" (the Rivalis index). Conversely, the other one genuinely consisted of data from the company it was named after (the Henrri index).
While in the past, our team has found that companies with major data leaks will often attempt to mislead us and deny any responsibility, in this case, our research does correlate specifically with the above statements, but not necessarily other claims of Groupe Phosphore relating to this breach.
While we tend to accept the comments of the company regarding Henrri and Rivalis brands, we decided to keep their mention in the report as those were the names of the indices, and we want to be accurate with the report.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
In the past, we’ve discovered a huge breach exposing the data of customers to a French hotel group owned by Accorhotels. We also revealed a data leak by French flight booking platform Option Way, compromising the privacy of their customers. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 25.11.2019]




Please, comment on how to improve this article. Your feedback matters!