Report: Facebook Credit Card Scam Exposed Via Huge Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently uncovered a potentially massive phishing and credit card fraud operation targeting Facebook users.
We discovered the scam via an unsecured database used by the fraudsters to store private data belonging to 100,000s of their victims.
The people running the scam were tricking Facebook users into providing login credentials for their private accounts via a tool pretending to reveal who was visiting their profiles.
The fraudsters used the stolen login credentials to share spam comments on Facebook posts via the victims hacked account, directing people to their network of scam websites. These websites all eventually led to a fake Bitcoin trading platform used to scam people out of ‘deposits’ of at least €250.
It was a vast operation, spanning the entire globe.
However, the fraudsters left the database used to harvest and store their victims' details completely open for anyone to view and access. With this information, we were able to expose their operation.
Incident Summary
| Company targeted | |
|---|---|
| Company headquarters | California, USA |
| Type of scam | Phishing attack; Credit card scam |
| Size of data in gigabytes | 5.5 GB+ |
| No. of records | 13,521,774 |
| No. of people exposed in Facebook scam* | 100,000s |
| No. of people exposed in Bitcoin scam* | 100,000s |
| Date range/timeline | June - September 2020 |
| Geographical scope | Worldwide |
| Types of data exposed | Facebook usernames and passwords; IP Addresses |
| Potential impact | Account takeover; identity theft; fraud; blackmail; disinformation |
| Data storage format | Unsecured Elasticsearch |
* Note: these figures are from the period June - September 2020. All the data stored in the database from before this time was wiped in a cyberattack. We believe many more people were victims of the scam before this.
Discovery and Investigation Timeline
- Database discovered: 21st September, 2020
- Date Facebook contacted: 21st September, 2020
- Database server closed*: 22nd September, 2020
*Note: The owners of the database most likely secured the server after it was completely wiped following a Meow cyberattack. Meow has been successfully targeting many unsecured Elasticsearch databases in recent months and wiping their data.
Sometimes, the extent of a data breach and the database's owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, it takes days of investigating before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the incident didn’t originate from Facebook. The exposed database belonged to a 3rd party using it to process Facebook account login credentials obtained illegally via a group of scam websites targeting the social network’s users.
Early in our investigation, we contacted Facebook to notify the company of our discovery and present our initial findings.
In the meantime, we continued to investigate the database to learn more. To confirm that the database was live and real, we entered fake login credentials on one of the scam web pages and verified they had been recorded.
However, the day after we discovered the database, it was attacked by the ongoing widespread Meow cyberattack, which completely wiped all its data.
The database went offline the same day and was no longer accessible. We believe the fraudsters did this following the Meow attack, but can’t confirm.

A snippet of code taken from the database shows our test entry was recorded
How the Scam Worked
There were many complex layers to this scam operation.
The Facebook Scam
In the first step, the fraudsters were harvesting login credentials for Facebook accounts from a network of websites owned by the group.
The websites tricked Facebook users into providing their login credentials by promising to show them a list of people who had recently visited their profiles.
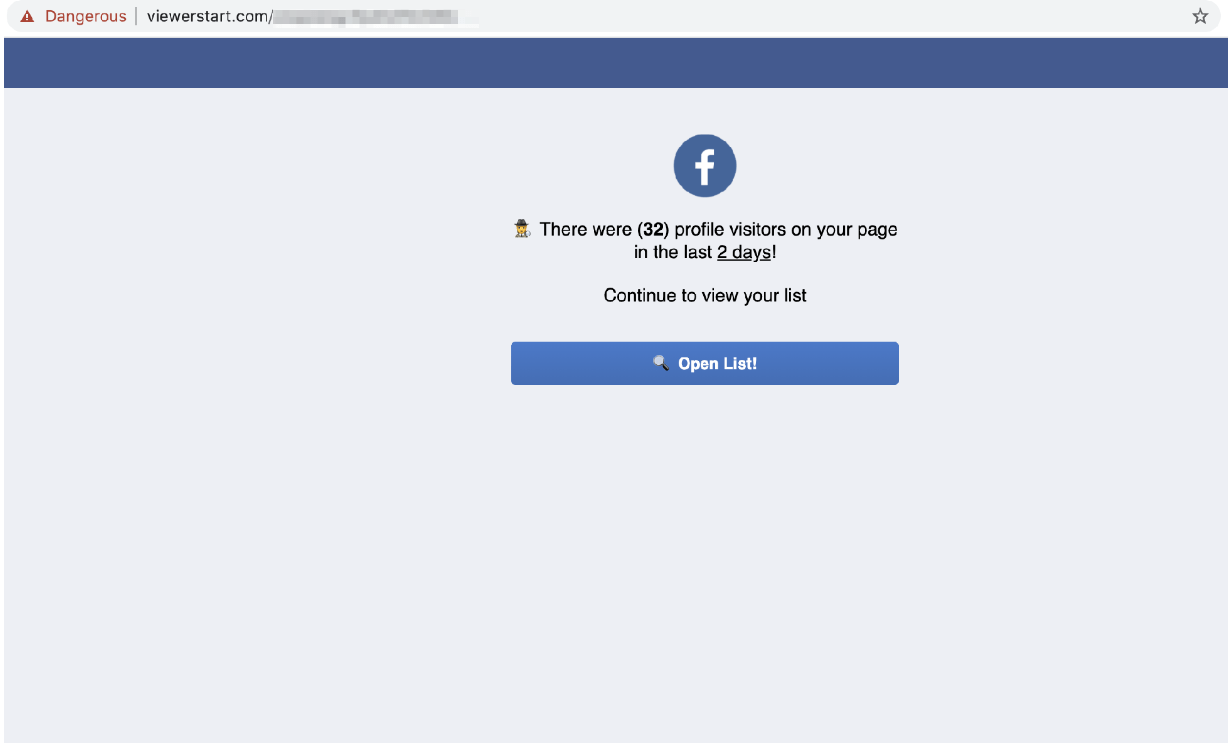
When a victim clicked the link to see the full list, they were sent to a fake Facebook login page and directed to input their login credentials.

After entering login credentials into the window - or any text for that matter - a fake loading page appeared promising to share the full list.

Finally, the victim was redirected to the Google Play page for an unrelated Facebook analytics app.
In the process, the fraudsters saved the victim’s Facebook username and password on the exposed database for future use in their other criminal activities. These were stored in Cleartext format, making it easy for anyone who found the database to view, download, and steal them.

Negative feedback on the analytics app from victims of the fraud, expressing their dissatisfaction with a seemingly broken app, show numerous people have gone through the entire scam and unknowingly had their data stolen.

The Bitcoin Scam
The next phase of the scam started once the fraudsters had their victims’ login credentials. They would take over accounts and comment on Facebook posts published in the victim’s network.
The comments all contained links to a separate network of scam websites owned and operated by the fraudsters.
In this phase, the fraudsters hoped to direct people to a huge Bitcoin fraud scheme.
They were posting links directly to websites in the Bitcoin scheme, alongside many fake news websites and similar spam content.
By including links to fake news websites, the fraudsters hoped to bypass and confuse Facebook’s fraud and bot detection tools. If the hacked accounts only posted the same links to a Bitcoin scam over and over, they’d quickly be blocked by the social network.
Occasionally, the fraudsters would also share links to legitimate news websites like The Washington Post for the same purpose.
However, the fake news websites created by the fraudsters all eventually directed people to their Bitcoin websites.
Once somebody landed on one of the bitcoin scam sites, they were directed to sign up for a free Bitcoin trading account and to deposit €250 into to start trading.
At this point, their money would be gone forever, stolen by the fraudsters.
What We Discovered
When we found it, the unsecured database contained 13.5 million records, totaling over 5.5GB of data.
This included:
- Facebook login credentials (usernames and passwords) for between 150,000 to 200,000 accounts on Facebook
- Text outlines for comments the fraudsters would make on Facebook hosts, via a hacked account, directing people to suspicious and fraudulent websites.
- Personally Identifiable Information (PII) data such as emails, names, and phone numbers from 100,000s of people who’d registered at a fraudulent Bitcoin site also run by the fraudsters.
- Domains for the websites used in the scam.
- Technical information about how the fraudsters had automated their processes.
This massive amount of data came from a short timeframe: June to September 2020.
However, the scam was probably much more extensive and had been operating for far longer.
Based on results from the internet search tool Shodan, we believe that we discovered the database after most of its contents had been deleted. At the time Shodan registered it, the database contained 11GB of additional data potentially related to the scam.
 Screenshot from Shodan search engine shows historical size of the database
Screenshot from Shodan search engine shows historical size of the database
Furthermore, due to the successful Meow cyber attack on the database the day after we discovered it, all data collected up to that point was wiped out. However, new data started appearing immediately after the attack until the database was secured later that day.
It's possible the exposed database was part of a much bigger operation.
Fake Websites and Scam Domains
Fortunately, the database also revealed details about the websites and domains used at every level of the scam.
Below is a list of the domain names used in the first part of the scam to steal peoples’ Facebook credentials:
- askingviewer.com
- capture-stalkers.com
- followviewer.com
- hugeviewing.com
- incredibleviewer.com
- letsviewing.com
- personviewer.com
- quickyviewer.com
- rightviewing.com
- stalkerfight.com
- stalkers-ever.com
- stalkers-unlimited.com
- taskviewing.com
- thinkviewers.com
- vectorviewers.com
- viewersrate.com
- viewerstart.com
- viewinall.com
- viewingage.com
- viewingaround.com
- viewingaway.com
- viewingpeople.com
- viewingsmart.com
- viewingstar.com
- viewingvisit.com
- viewstanding.com
- viewstarter.com
- viewvisitors.com
- Visitorsviewer.com
Aside from these domains, the database contained 100s more for the websites used to mask the fraudsters’ activity (the fake news sites, for example).
We also found 100s of domains related to the Bitcoin scam. A small sample of these:
- tthrsw.com
- Basure-behorus.com
- Castalks-caryback.com
- Cz.superiffy.com
- Clks.yourtopoffers.com
- Go.gamesadar.com
- Host.healthysystems4u.com
- M.tracktechs.net
- Milical-bressorts.com
- Ninvite-implace.com
- Play.realfreegames.net
- Web.2secondsurvey.com
- www.sexylaid.co
Many of these scam websites were hosted on popular hosting provider Namecheap.
The domains were all registered between June and September, corresponding with the data uploaded to the database. However, it's also possible the fraudsters were using additional domains, but records of these were deleted before September.
They were also in various languages for targeting people across the world, including Germany, Italy, the UK, Austria, Australia, New Zealand, Czech Republic, Slovakia, Belgium, and many more.
Data Breach Impact
Throughout the database, we found evidence that the fraudsters were already successfully trapping people in their Bitcoin scams before the database went offline.
However, this isn’t the only way someone could use the PII data harvested from Facebook in this scam for criminal purposes.
Facebook Account Takeover
The most obvious action is the fraudsters taking over a person's Facebook account, posting a link to one of their websites on the victim's timeline, and tricking their friends into falling prey to the scam, growing its potential impact exponentially.
There’s evidence they were already engaging in a similar activity to this by using a victim’s profile to publish comments on Facebook posts directing people to a network of additional fraudulent websites unrelated to Facebook profile views. It’s also possible the fraudsters were posting links on victims’ timelines, as described above, but we didn’t see evidence of this.
External Account Takeover
Many affected victims of this scam are probably reusing usernames, passwords, and email addresses across numerous platforms, apps, and private online accounts.
With one set of login credentials, the fraudsters could target other popular platforms for hacking by logging in to accounts with the same details. This is a pervasive form of fraud known as ‘credential stuffing’ and is often very successful.
They could also use the information found in a person’s Facebook account to create phishing campaigns beyond Facebook, targeting victims over email and imitating legitimate businesses, tricking them into providing additional info like credit card details, etc.
Fraud, Identity Theft, and Blackmail
By taking over a person’s Facebook profile, the fraudsters would also have access to their private data, personal details, contacts, messages with friends, and much more.
With this information, someone could build a comprehensive profile of each user and use the details to target them in other scams, such as identity theft and financial fraud.
If the fraudsters found sensitive, embarrassing, or criminalizing content in a person's Facebook messages, they could use this to blackmail and extort them.
Disinformation and Fake News
The fraudsters used hacked accounts to spread fake news stories about political events in different countries, such as the upcoming US election.
If another party had found this database, they could have taken the login credentials and used them to spread their own fake news and disinformation campaigns.
Posting such stories from a hacked account would make it easier to spread through that person's network, as friends and family would be more trusting.
Advice from the Experts
If you’re a Facebook user and think you’ve been a victim of this fraud, change your login credentials immediately.
Furthermore, if you reused your Facebook password on any other accounts, change it immediately to protect them from hacking. We recommend using a password generator to create unique, strong passwords for every private account you have, and changing them periodically.
You can also use our password meter to ensure your current passwords are strong enough.
Never provide usernames and passwords for Facebook, email, or financial accounts to external websites.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Database
The research team at vpnMentor uncovered the database breach in the course of an expansive web mapping endeavor. Our investigators employ port scanning to scrutinize designated IP blocks and assess various systems for possible weaknesses or vulnerabilities. Each identified weakness is thoroughly probed for any signs of data leakage.
Our team was able to access this database because it was completely unsecured and unencrypted.
The fraudsters were using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when our research uncovers issues that may impact its users. We reached out to Facebook to let them know about the scam and how many people had been affected.
These ethics also mean we carry a responsibility to the public. Facebook users must be aware of scams targeting them.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included a state in India exposing data for millions of Covid-19 patients in the country. We also revealed that a group of free VPNs was recording their users’ activity and exposing it in a massive data leak. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: November, 13th 2020 ]




Please, comment on how to improve this article. Your feedback matters!