Report: Ecuadorian Breach Reveals Sensitive Personal Data
vpnMentor's research team has found a large data breach that may impact millions of individuals in Ecuador. The leaked database includes over 20 million individuals.
Led by Noam Rotem and Ran Locar, our team discovered the data breach on an unsecured server located in Miami, Florida. The server appears to be owned by Ecuadorian company Novaestrat.
Novaestrat is a consulting company that provides services in data analytics, strategic marketing, and software development.
The data breach involves a large amount of sensitive personally identifiable information at the individual level. The majority of the affected individuals seem to be located in Ecuador.
Although the exact details remain unclear, the leaked database appears to contain information obtained from outside sources.
These sources may include Ecuadorian government registries, an automotive association called Aeade, and Biess, an Ecuadorian national bank.
The breach was closed on September 11, 2019.
Example of Entries in the Database
The data breach involves around 18 GB of data. As many as 20 million individuals may be impacted by this breach, although some of the data seems to involve individuals who are already deceased.
To give some context about the scale of this leak, Ecuador has a population of around 16 million people.
Individuals in the database are identified by a ten-digit ID code. In some places in the database, that same ten-digit code is referred to as “cedula” and “cedula_ruc”.
In Ecuador, the term “cédula” or “cédula de identidad” refers to a person’s ten-digit national identification number, similar to a social security number in the US.
The term “RUC” refers to Ecuador’s unique taxpayer registry. The value here may refer to a person’s taxpayer identification number.
In order to check the validity of the database, we ran a search with a random ID number. By doing this, we were also able to find a variety of sensitive personal information.
Here are some examples of the personal information that we could find:
- full name (first, middle, last)
- gender
- date of birth
- place of birth
- home address
- email address
- home, work, and cell phone numbers
- marital status
- date of marriage (if applicable)
- date of death (if applicable)
- level of education
Here is an example of a typical entry:

Our search to validate the database also brought up specific financial information related to accounts held with the Ecuadorian national bank Biess (El Banco del Instituto Ecuatoriano de Seguridad Social), including:
- account status
- current balance in the account
- amount financed
- credit type
- location and contact information for the person's local Biess branch
Here is an example of this type of data:

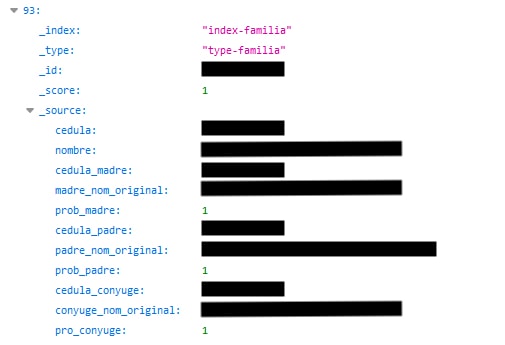
One of the most concerning parts about this data breach is that it includes detailed information about people’s family members.
For each entry, we were able to view the full name of their mother, father, and spouse. We were also able to view each family member’s “cedula” value, which may be a national identification number.
In another part of the database, we found detailed employment information. We were able to view each person’s:
- employer name
- employer location
- employer tax identification number
- job title
- salary information
- job start date
- job end date
The data breach also exposed various automotive records that may be linked to individual car owners through their taxpayer identification number.
The leaked information includes the car’s license plate number, make, model, date of purchase, most recent date of registration, and other technical details about the model.
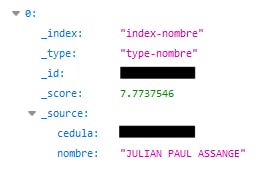
Entry for Julian Assange
Within the leaked records, we found an entry for WikiLeaks founder Julian Assange.
We were able to view his name, as well as the “cedula” value that may be a national identification number in Ecuador.
In 2012, Assange was granted political asylum by Ecuador. Assange resided in the Ecuadorian embassy in London up until April of 2019.
Assange was arrested at the embassy by British law enforcement officials after Ecuador withdrew his asylum, claiming that Assange repeatedly violated his asylum terms.
Company Records
In addition to personal information, the data breach also revealed details related to various companies in Ecuador.
Some of the exposed information may be sensitive. We were able to view many companies’ Ecuadorian taxpayer identification number (RUC), along with each company’s address and contact information.
The database also listed each company’s legal representative and provided their detailed contact information.
Data Breach Impact
Although the data breach is closed, the leaked data could create long-lasting privacy issues for affected individuals.
Scams and Phishing Attacks
The exposed personally identifiable information (PII) includes full names, addresses, phone numbers, emails, information about family members, and more.
This information leaves individuals at risk of email and phone scams. Hackers and other malicious parties could use the leaked email addresses and phone numbers to target individuals with scams and spam.
Phishing attacks could be tailored to the individuals using exposed details to increase the chances that people will click on the links.
This data breach is particularly serious simply because of how much information was revealed about each individual. Scammers could use this information to establish trust and trick individuals into exposing more information.
For example, a scammer could pretend to be a friend of a family member in need of financial help. They could back up the story with exposed personal information to build trust.
Identity Theft and Financial Fraud
Another issue is the highly private and sensitive nature of some of the leaked information.
Most concerningly, the leaked data seems to include national identification numbers and unique taxpayer numbers. This puts people at risk of identity theft and financial fraud.
A malicious party with access to the leaked data could possibly gather enough information to gain access to bank accounts and more.
Additionally, access to automotive details can assist criminals in identifying specific vehicles and their owner’s address.
Impact on Companies in Ecuador
The data breach could also have an impact on Ecuadorian companies. The leaked data included information about many companies’ employees, as well as details about some companies themselves.
These companies may be at risk of business espionage and fraud. Knowledge of a company’s employees could help competitors or other malicious parties gather additional sensitive company data.
Advice from the Experts
Once data has been exposed to the world, it can’t be undone. The database is now closed, but the information may already be in the hands of malicious parties.
This kind of data breach could have been prevented with some basic security measures. No matter what the size of your company is, you should always use the following security practices:
- Secure your servers
- Implement appropriate access rules
- Require authentication to access all systems
For a more in-depth guide on how to protect your business, check out how to secure your website and online database from hackers.
How and Why We Discovered the Breach
The vpnMentor research team discovered this breach as part of our large-scale web mapping project.
Our research team, guided by security specialists Ran and Noam, conducts port scans to identify recognized IP blocks. Following this, the team seeks out system vulnerabilities that could signify the presence of an unsecured database.
Once a data breach is found, our team links the database back to the owner. We then contact the owner, inform them of the vulnerability, and suggest ways that the owner can make their system more secure.
As ethical hackers and researchers, we never sell, store, or expose the information we encounter.
Our goal is to improve the overall safety and security of the internet for everyone.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
We recently discovered a massive fraud network targeting Groupon and online ticket vendors. We also found a data breach in the email platform used by a South Korean company, DKLOK.




Please, comment on how to improve this article. Your feedback matters!