Report: AccorHotels Subsidiary Exposes Hotels and Travelers in Massive Data Leak
- Gekko Group Company Profile
- Timeline of Discovery and Owner Reaction
- Examples of Exposed Data
- Impact of the Data Breach
- For Gekko Group and AccorHotels
- For Gekko Group Clients & Travel Agents
- For Travel Agents’ Customers
- Advice from the Experts
- How and Why We Discovered the Breach
- About Us and Previous Reports
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a data breach belonging to Gekko Group, a subsidiary of Accor Hotels.
Based in France, Gekko Group is a leading European B2B hotel booking platform that also owns several smaller hospitality brands.
These include Teldar Travel & Infinite Hotel, the two brands most exposed in the database discovered by our team. However, some data from other Gekko Group-owned brands were also exposed.
The database in question was huge, containing over 1 terabyte of data. This included data from Gekko Group brands and their clients, as well as external websites and platforms which their systems communicate with, such as Booking.com.
This breach represents a serious lapse in data security by Gekko Group and its subsidiaries, compromising the privacy of their customers, clients, AccorHotels, and the businesses themselves.
Gekko Group Company Profile
Founded in 2010 and based in France, Gekko Group primarily works in the European hospitality market but has offices worldwide. A B2B hotel booking platform, it also owns many smaller brands. Within all these brands, Gekko Group has a combined customer base of 600,000 hotels worldwide, with interests in corporate travel, leisure travel, hotel inventory, and data distribution.
In 2017, AccorHotels - the largest hospitality company in Europe, and the sixth-largest worldwide - purchased Gekko Group. At the time, Gekko Group was valued at $117 million.
Teldar Travel
Owned by Gekko Group, Teldar Travel is a European B2B hotel booking system built for travel agents. The platform claims to connect over 14,000 travel agents with 1,000,000 accommodation providers around the world, as well as transport options.
This helps travel agents book and manage accommodation, transport, and various other activities for their customers in a streamlined process.
Infinite Hotels
Also owned by Gekko Group, Infinite Hotels manages wholesale inventory and booking data distribution relating to accommodation providers across various travel-related online platforms.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and what’s at stake takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true.
In this case, the database contained files belonging to numerous Gekko Group brands and external platforms. Initially, it was unclear exactly which brand the database belonged to. With data originating from numerous sources, the team had to cross-reference data with different brands to make sure they all matched.
Once we confirmed Gekko Group as the database’s owner, we attempted to contact AccorHotels and their data privacy officer to notify them of the breach and help resolve the issue.
When this failed, our team reached out to Gekko Group directly, as well as their GDPR officer.
Still receiving no replies from AccorHotels or Gekko Group, we contacted their hosting company and, eventually, the Commission Nationale de l'Informatique et des Libertés (CNIL) - France’s independent regulatory body for data security and privacy.
Finally, on November 13th, after a week of emails being sent, we received a response from AccorHotels asking about the leak. Almost immediately after, it had been closed. We duly received a thank you note from AccorHotels, confirming the closure of the leak. They also informed Gekko Group accordingly.
- Date discovered: 7/11
- Date vendors contacted: 7/11
- Date of 2nd contact attempt (if relevant): 10/11
- Date of Response: 13/11
- Date of Action:13/11
Examples of Exposed Data
Hosted in France on servers belonging to OVH SA, the compromised database was huge, containing approximately 1TB of data.
While the data belonged to AccorHotels - via their ownership of Gekko Group - it originated from many different businesses within Gekko Group. The bulk of the data came from two sources: Teldar Travel & Infinite Hotels.
As Gekko Group’s brands serve very different functions, there was a huge variety in types of data our team accessed, including:
- Hotel and transport reservations
- Credit card details
- Personally Identifiable Information (PII) of various parties
- Login credentials for client accounts on Gekko Group-owned platforms
- etc.
As these businesses interact with many external platforms in the travel and hospitality industries, the database also contained data originating from platforms outside of the Gekko Group umbrella.
This exposed hotels, travel agencies and their customers around the world, many of whom had no direct relationship with Gekko Group or its brands.
Our team viewed database entries in numerous languages, originating from many different countries, mostly in Europe. These included citizens of the following countries:
- Spain
- The United Kingdom
- The Netherlands
- Portugal
- France
- Belgium
- Italy
- Israel
Travel Reservations & PII
Most of the data we viewed originated from two Gekko Group-owned platforms: Teldar Travel and Infinite Hotel. Both platforms serve separate functions relating to accommodation reservations and data.
Given its function as a booking platform for travel agents, the entries in the database relating to accommodation and transport reservations mostly came from Teldar Travel.
Whenever a travel agent used the platform to make a reservation for a customer, an entry was logged on Gekko Group’s database.
The data exposed in these reservations included:
- Full names
- Email addresses
- Home addresses
- PII of children
- Travel dates
- Destination hotels
- Reservation details (no. of guests, room types, etc.)
- Price of stays
- Data from external reservations platforms (ie. Booking.com)
Because Teldar Travel interacts with many other accommodation and travel platforms, the database also contained significant amounts of data from external sources.
External platforms whose data was exposed due to interaction with Gekko Group-owned platforms included:
- Occius - Spanish travel platform
- Infra - French creative agency
- Smile - French digital experience and web development agency
- Mondial Assistance - Polish travel platform
- Selectour.com - French online travel agency
- Booking.com - International hotel booking platform
- Hotelbeds.com - International hotel booking platform
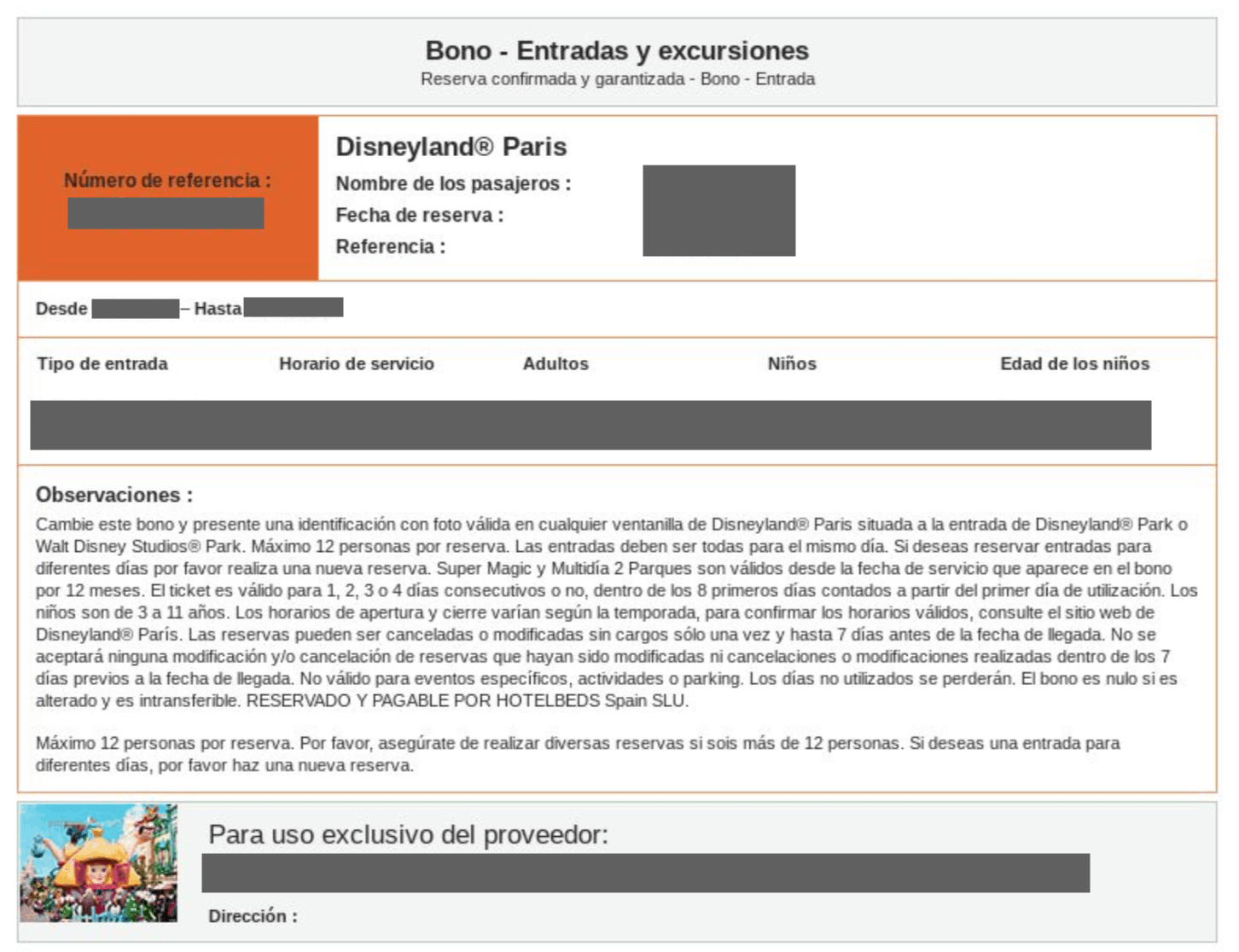
Below is an example of a reservation made via Booking.com, exposing the PII of guests.

Aside from hotel reservations, the exposed data also included other forms of travel and hospitality-based reservations. These included tickets to Eurodisney, guest transfers between the hotels and airports, excursions and tours, and tickets for the Eurostar train.
Financial Details Exposed
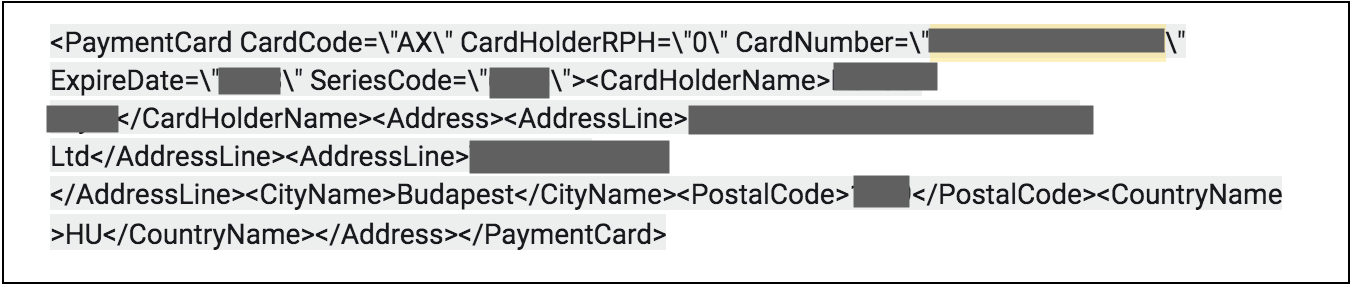
Along with the exposed PII data, many entries contained invoices exposing financial details of travel agents and their customers.
The database contained invoices attached to certain reservations, made using credit cards belonging to agents and/or their clients. These included regular, virtual, and prepaid credit cards.
Below is an example of a reservation made via Teldar Travel, with redacted credit card details clearly displayed.
Account Login Credentials
During their investigation, our team viewed thousands of plain text passwords linked to accounts on Gekko Group-owned platforms.
In theory, this could have allowed us to log in to private accounts and take certain actions, including:
- Booking on the account credit
- Canceling existing bookings
- Accessing invoices
- Many more possibilities
Amongst the parties affected in the data breach were the World Health Organisation. Our researchers viewed usernames and passwords for the WHOs account on Teldar Travel, potentially giving them access to the WHOs large credit account and travel budget on the platform.
Impact of the Data Breach
To reiterate, this is a huge amount of data to be exposed. It represents a serious lapse in the data security protocols of Gekko Group and its subsidiaries, with serious implications for the many people affected.
For Gekko Group and AccorHotels
For two companies of their respective sizes and market shares, Gekko Group and AccorHotels would be expected to have more robust data security.
By exposing such a huge amount of sensitive data, they will likely face serious questions over how this happened, and their wider data security policies for all brands they own.
Data security and privacy are two of the biggest concerns for all online consumers. Any company that exposes customers to risk will face serious questions over trust and reliability, damaging their reputation and potentially harming their future revenue and growth.
Account takeover
From a practical perspective, the breached database also exposed Gekko Group to various forms of fraud and attack.
The login credentials our team viewed could give hackers access to private user accounts on reservation platforms owned by the company.
With these, hackers could enter accounts and charge purchases to virtual credit cards stored within, maxing them out before AccorHotels or Gekko Group can charge clients for reservations, and similar bookings made.
This could lead to serious losses for the company.
Legal Action
Based in France, with many European customers, AccorHotels and Gekko Group are within the jurisdiction of the European Union and their GDPR rules. A leak of this magnitude opens both companies to potential legal action, including fines and lawsuits.
For Gekko Group Clients & Travel Agents
For companies using Gekko Group’s proprietary software, account takeover is also a concern. By accessing their user accounts and abusing their credit accounts, hackers would also be causing significant harm to these much smaller businesses.
Even if it were possible, recovering any stolen funds would be a long and expensive process.
The contents of the database could also help hackers and cybercriminals target the same companies in other ways. Using the information and accesses exposed, they could create effective phishing campaigns, or target companies with various forms of malicious software attacks: malware, spyware, ransomware, and more.
There are many ways a company using Gekko Group’s platforms could be attacked, but they all have one thing in common: they would be devastating to the companies targeted.
For Travel Agents’ Customers
With so much of the PII and financial data exposed, the customers of travel agents using Gekko Group’s platform are also vulnerable to attack.
The information our team viewed could be used in many ways. One potential tactic for hackers would be building effective phishing campaigns. Posing as hotels, booking agents, or Teldar Travel, hackers could trick targets into revealing additional information and using this to steal from them, send malicious software like malware and spyware, and steal their identities.
These campaigns of fraud would not need to be sophisticated. Given the size of the data being exposed, even if only a small number of targets were successfully attacked, the hackers would consider it a success.
Advice from the Experts
Gekko Group could have easily avoided this leak if they had taken some basic security measures to protect the database. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online Gekko Group from hackers.
For Gekko Group Clients
Contact Gekko Group and ensure they are taking the necessary steps to resolve any potential vulnerabilities.
In the meantime, we suggest changing any passwords and usernames for a platform owned by Gekko Group. This will ensure no future access by malicious actors, if your data was exposed in any way.
For an added layer of protection, use a password generator to create the most secure password possible.
We also suggest thoroughly vetting any 3rd party software and contractors you use to guarantee they’re following strict data security protocols.
If you’re concerned about how data vulnerabilities in general might affect your privacy and security, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
As part of an extensive web mapping initiative, the vpnMentor research team detected the breach in the Gekko Group's database. Our investigators employ port scanning to scrutinize distinct IP blocks and probe open vulnerabilities within systems. Each detected gap is thoroughly assessed for potential data leakage.
When they find a data breach, they use expert techniques to verify the Gekko Group’s identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
Our team was able to access this server because it was completely unsecured and unencrypted.
The company uses an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata.
The purpose of this web mapping project is to help make the internet safer for all users. As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security.
However, these ethics also mean we also carry a responsibility to the public. This is especially true when the companies data breach contains such a huge amount of private and financial information.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data. In the past, we’ve discovered a huge data breach exposing the data of millions of Ecuadorean citizens. We also revealed that a breach in Biostar 2 compromised the biometric data of over 1 million people. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 20.11.2019]




Please, comment on how to improve this article. Your feedback matters!