Report: Security Platform Leaking Hotel Security Logs, Including Marriott Properties
vpnMentor’s research team has recently discovered that Marriott and other hotel brands managed by The Pyramid Hotel Group have experienced a cybersecurity data leak, revealing vulnerabilities that could be an important tool with significant impact in a massive future attack.
Led by hacktivists Noam Rotem and Ran Locar, vpnMentor’s researchers discovered a breach that exposes 85.4GB of security audit logs, which also include personally identifying information (PII) of employees of the affected companies, and go back as far as April 19, 2019. This date may indicate system setup, reconfiguration, or maintenance that impacted the server and made it open and available to the world.
The Pyramid Hotel Group utilizes Wazuh - an open source intrusion detection system - on an unsecured server that is leaking information regarding their operating systems, security policies, internal networks, and application logs.
Editor's Note: Wazuh is a security monitoring tool, and as such, alerts generated by Wazuh can be stored just about anywhere. Securing those systems is left to the responsibility of the user, including securing data and preventing its exposure to unauthorized users. This leak was not caused by an error on the part of the Wazuh tool, nor its team.
Timeline of Discovery and Reaction
| DATE | EVENT |
|---|---|
| 5/27/19 | Breach discovered by vpnMentor Research team |
| 5/28/19 | Informed PHG of breach |
| 5/28/19 | Received acknowledgement from PHG |
| 5/29/19 | Data leak closed. Problem resolved. |
Information Included in the Database
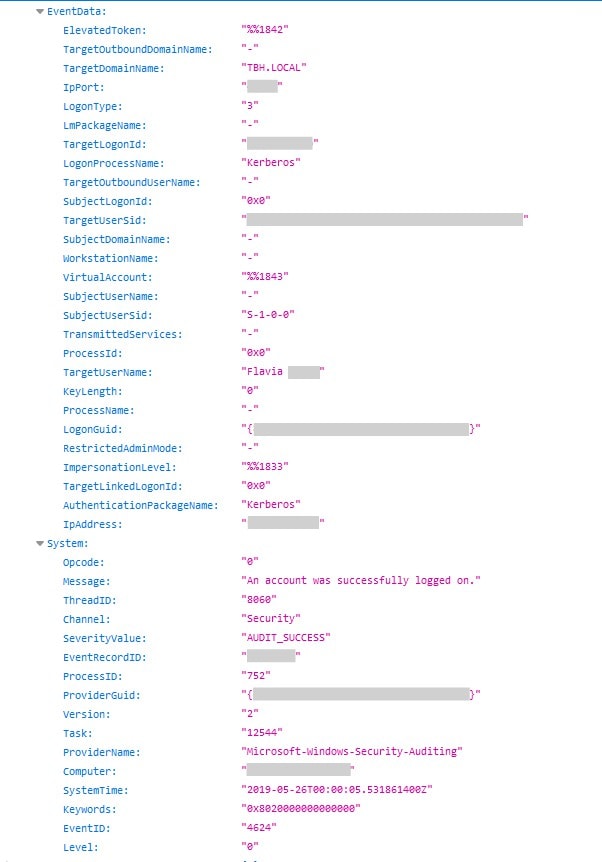
The unsecured data that is publicly visible include both monitoring and alerts, reported system errors, misconfiguration, policy violations, potential attempted malicious breaches, and other cybersecurity events.
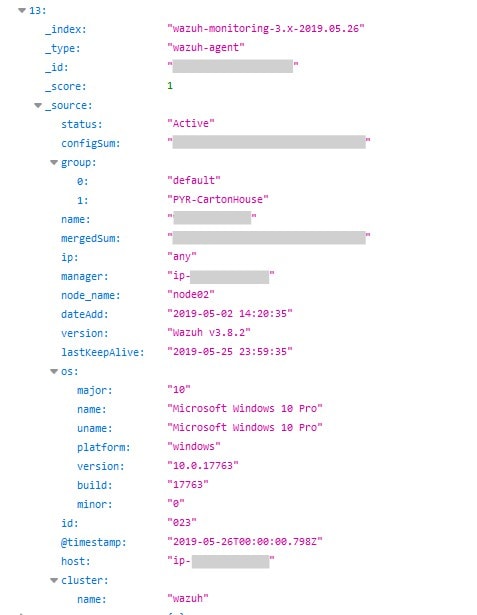
Affected parties seem to include Tarrytown House Estate (New York), Carton House Luxury Hotel (Ireland), Aloft Hotels (Florida), Temple Bar Hotel (Ireland) and other brands in the Pyramid Hotel Group.
What we can see through the data leak includes - but is not limited to - the following sensitive details:
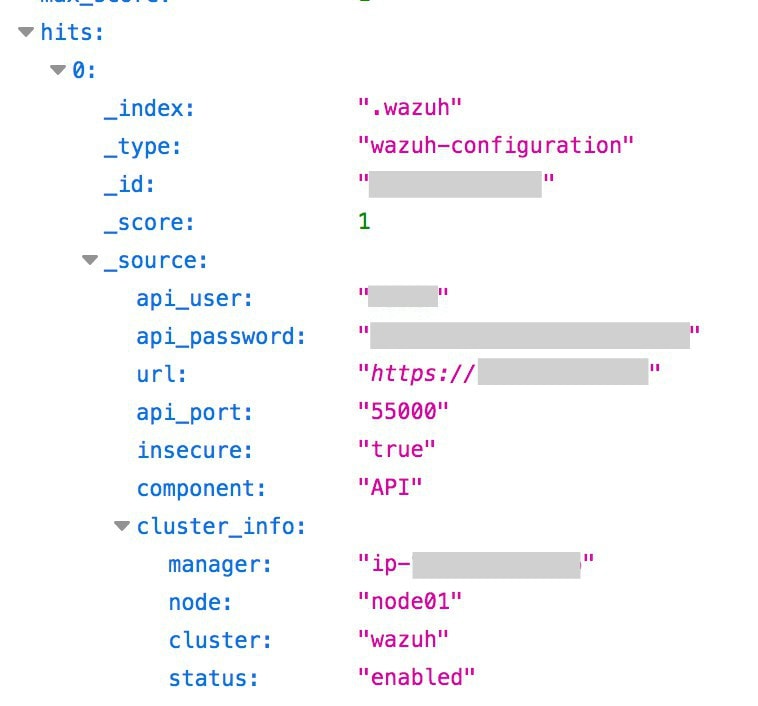
- Server API key and password
- Device names
- IP addresses of incoming connections to the system and geolocation
- Firewall and open ports information
- Malware alerts
- Restricted applications
- Login attempts
- Brute force attack detection
- Local computer name and addresses, including alerts of which of them has no antivirus installed
- Virus and Malware detected on various machines
- Application errors
- Server names and OS details
- Information identifying cybersecurity Policies
- Employees’ full names and usernames
- Other telling security data
The Danger of Exposing this Information
This database gives any would-be attacker the ability to monitor the hotels’ network, gather valuable information about administrators and other users, and build an attack vector targeting the weakest links in the security chain. It also enables the attacker to see what the security team sees, learn from their attempts based on the alerts raised by the systems, and adjust their attacks accordingly. It’s as if the nefarious individuals have their own camera looking in on the company’s security office.
In the worst case scenario, this leak has the potential to put not only systems at risk, but the physical security hotel guests and other patrons as well. Our team found multiple devices that control hotel locking mechanisms, electronic in-room safes, and other physical security management systems. Especially in the wrong hands, this drives home the very real danger here of when cybersecurity flaws threaten real-world security.
With this window into the cybersecurity events and policies, it is possible to fine-tune tactics to gain entry into the systems of the affected companies. From what we can see, it's possible to understand the naming convention used by the organization, their various domains and domain control, the database(s) used, and other important information leading to potential penetration.
This data leak is disclosing information that is private, secret, and would typically be for the eyes of an internal-team or MSSP only. The irony is that what’s being exposed is from a system that is meant to protect the company from such vulnerabilities.
How We Discovered the Leak
vpnMentor’s research team is currently undertaking a huge web mapping project. Using port scanning to examine known IP blocks reveals gaps in web systems, which are then examined for vulnerabilities, including potential data exposure and breaches.
Tapping into years of experience and know-how, the research team examines the database to confirm its identity.
After identification, we reach out to the database’s owner to report the leak. Whenever possible, we also alert those directly affected. This is our version of putting good karma out on the web - to build a safer and more protected internet.
Advice From The Experts
Could this data leak have been prevented? Without a doubt! Companies can steer clear of such a situation by promptly implementing essential security measures, which include:
- First and foremost, secure your servers.
- Implement proper access rules.
- Never leave a system that doesn't require authentication open to the internet.
For more in-depth information on how to protect your business, check out how to secure your website and online database from hackers.
You May Be Interested in Our Past Reports:
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
We recently revealed that a data breach exposed more than 80 million US households, and that more than 25% of Fortune 500 companies have been hacked. You may also want to read our report of fake apps used in Iran to monitor users, VPN Leak Report and Data Privacy Stats Report.
Please share this report on Facebook or tweet it.





Please, comment on how to improve this article. Your feedback matters!