What Is I2P vs Tor? How to Install & Use With a Browser (2026)
With regular browsers, user privacy and security are constantly under threat on the internet. The high demand for safe and encrypted connections has resulted in traffic anonymization services like Tor and the Invisible Internet Project (I2P) network.
I2P is a decentralized network that encrypts your data and routes it through a series of volunteer-operated nodes, ensuring that your identity and activities remain hidden. This not only shields you from prying eyes but also makes it nearly impossible for anyone to trace your online movements. It also offers additional benefits, such as safe emailing and torrenting tools.
Whether you’ve never used it before or you just want to expand your knowledge, I'll cover the nitty-gritty of how I2P works, the browser installation process, and how using the network can open up a world of online possibilities.
What Is the I2P Network and How Does It Work?
The Invisible Internet Project (I2P) is an anonymous network layer designed to provide secure communications over the internet. Through a system of encryption and routing techniques, it conceals your identity, location, and browsing activities, making it difficult for third parties to track or intercept your data. You can browse I2P websites (eepsites), chat, blog, and share files securely without exposing your IP addresses or other identifying information.
The I2P network operates through a series of tunnels, which are pathways that data packets travel through to reach their destinations. When a user sends data, it’s first encrypted and then split into multiple parts. These parts are sent through various tunnels, with each part taking a different route. This process prevents a single entity from intercepting the complete data, thus preserving your privacy and security.
To further enhance security, I2P employs garlic routing, a technique where multiple messages are bundled together into a single encrypted packet, similar to how layers of an onion work in Tor. This makes it hard for snoops to analyze the traffic and link messages to specific users.
I2P also functions as a decentralized peer-to-peer (P2P) network (using a distributed network called NetDB), where users volunteer their resources to help route data for others. Each participant in the I2P network acts as both a client and a server, routing traffic for others while simultaneously sending and receiving their data. This decentralization means that there is no single point of failure, making the network resistant to censorship and surveillance.
The Pros and Cons of Using the I2P Network
The I2P network offers many advantages but also comes with challenges. It’s good to understand both sides to make an informed decision on whether it's the right tool for you.
Pros
Secure Data Routing
The I2P garlic routing and tunneling system minimizes the risk of cyber threats (like Man-in-the-Middle and Timing attacks) by splitting and encrypting data. The network also provides a secure way to communicate or share information with minimal fear of being hacked.
Enhanced User Privacy and Anonymity
I2P hides users' IP addresses and encrypts all data transmitted over the network. This keeps your online activities private and protected from prying eyes, safeguarding against surveillance and data tracking.
Decentralization and Resilience
The network’s decentralized nature means there is no central authority, making it difficult for any single entity to control I2P or shut down the network. This also means consistent connection availability and reliability, even in restrictive environments.
Versatile Use Cases
I2P supports a wide range of applications, from anonymous browsing and blogging to secure file sharing and encrypted email communications. It also provides a platform for developers to create privacy-focused apps.
Fast P2P File Sharing
Unlike Tor's circuits, I2P's unilateral proxy tunnels allow for more efficient P2P file sharing. In fact, Tracker2.postman.i2p is one of I2P’s most popular services. It features thousands of torrents that can be loaded onto your torrent client for secure, anonymous file sharing.
Community-Driven Development
I2P is an open-source project that is continually improved and maintained by a dedicated community of developers and users. This collaborative effort helps keep the network up to date with the latest security enhancements and features.
Cons
Impact on Speed and Bandwidth
The multiple layers of encryption and the complex routing system used to anonymize traffic can result in slower data transfer rates compared to traditional internet connections. This can be particularly noticeable when downloading large files or streaming media, where the reduced speed can be a significant drawback.
Complexity and Usability
The I2P network isn't as straightforward as mainstream internet services. The initial setup and configuration can be complicated, especially for the less tech-savvy. Configuring proxies, managing keys, and understanding how to navigate the I2P ecosystem requires a certain level of technical knowledge.
Limited Content Access
Unlike Tor, which allows access to both the regular internet (clearnet) and its own .onion sites, I2P only facilitates access to services and websites within its own network (eepsites). To access the “normal” internet with I2P, you need to use outproxies (like exit nodes for Tor), which can compromise I2P’s levels of privacy.
This means that the variety and volume of content available is limited compared to the open internet, making it challenging to locate specific information or resources.
Resource Intensive Client
Running the I2P client can consume significant amounts of CPU and memory, affecting the performance of other applications. If you’re on a device with limited resources or older and less powerful hardware, you may experience performance issues and a lack of system responsiveness.
Legal and Ethical Considerations
The I2P network can be misused for illegal activities, such as distributing illicit content or conducting illegal transactions. This potential for misuse may also attract unwanted attention from law enforcement agencies.
Network Stability Issues
Because I2P is decentralized and relies on the participation and cooperation of its users to maintain stability and performance, network quality can vary significantly. You may experience higher latency sometimes when the network is less stable.
How I2P Differs from Other Private Networks
There are some distinguishing differences between I2P and other privacy-focused networks and tools like Tor, Freenet, and VPNs. Each achieves enhanced security in different ways suited to various use cases.
I2P vs Tor
I2P and Tor both aim to provide anonymous internet browsing but differ in their architectures and methods. Tor (short for The Onion Router) uses a system of layered encryption to route internet traffic through a network of volunteer-operated servers. This creates a series of encrypted layers (hence the onion analogy) that mask the user's IP address and data content from any would-be observers.
In contrast, I2P uses a garlic routing technique, where multiple messages are bundled together into a single encrypted packet. This method enhances privacy by making it more difficult for anyone to analyze the traffic and link the data back to specific users.
Also, Tor supports access to the open internet (clearnet), while I2P only allows access to websites and services (known as eepsites) within its own networks. Outproxies, which are similar to Tor exit nodes, can be used to access the clearnet with I2P. However, this reduces privacy as your data leaves the network and is a less common use case.
I2P vs Freenet
Freenet is a closed peer-to-peer and distributed data store for publishing and retrieving information, with a focus on resisting censorship. The content on freesites (Freenet sites) can be accessed even if the original publisher isn’t online. Also, users can securely and privately share files, publish websites, and interact through forums. Freenet doesn’t have exit nodes, so it can’t be used to browse the regular internet.
I2P, on the other hand, is more versatile in its use cases, supporting browsing, blogging, chat, file sharing, and other online activities. It focuses on providing secure P2P communication data privacy using encrypted tunnels and a sophisticated routing system.
I2P vs VPNs
While I2P is its own network, VPNs are designed more for accessing the regular internet with boosted privacy. VPNs create a secure, encrypted tunnel between a user's device and a remote server, masking the user's IP address and encrypting data in transit. This is useful for securing web and WiFi connections, bypassing geo-restrictions, and avoiding issues like ISP connection throttling.
VPNs are also centralized services run by commercial entities, so it’s essential to use a trustworthy service that does not log activities or share data. I2P is decentralized and does not rely on a central authority. This means no single entity has control over the network or access to users' data, making I2P more resilient against activity logging and centralized points of failure.
How to Download & Install the I2P Client
The I2P client works on most major operating systems, including Windows and macOS. It's natively supported on Android mobile devices but not iOS. Linux users can use I2P on Debian Ubuntu or Mint, but it doesn't work on Tails anymore.
Setting it up on Windows’ Microsoft Edge or the Chrome browser isn’t recommended if you highly prioritize security and privacy. That said, you can easily set up I2P with privacy-friendly browsers like Firefox or Brave.
I2P needs a Java application installed before it can run (you may be prompted to download Java if it’s not already on your computer). Without Java, the I2P client installation can fail.
Here is a step-by-step guide to installing I2P on a desktop platform. My guide uses Windows, but the procedure is similar for macOS.
Installing I2P on Windows & macOS
- Download the I2P installer for your device from the official I2P website.
 Make sure you've also installed Java before you begin
Make sure you've also installed Java before you begin - Locate the downloaded installer and double-click to run it.
- If asked to allow User Account Control (UAC), click Yes. If you encounter a message from Windows Defender blocking the installation, right click on the file and select Run as Administrator.
- After the I2P installation wizard opens, accept and click Next to all the installation prompts.
 You can run the installer as an administrator if it's blocked by Windows Defender
You can run the installer as an administrator if it's blocked by Windows Defender - Once the installation is complete, click Done to exit the wizard.
 Restart your browser before configuring it with the I2P proxy settings for effective integration
Restart your browser before configuring it with the I2P proxy settings for effective integration
When you start I2P for the first time, it’ll open your default web browser and take you to the I2P Router Console, which is the control panel for your client. It may take a few minutes for your router to integrate into the network, but you’ll see a status message once it's ready.
Installing I2P on Linux
The procedure for installing I2P on Linux is quite similar to Windows, with minor variations.
- Download the appropriate Linux installer package (get .deb for Debian-based systems or .tar.bz2 for others).
- Open the terminal and navigate to the download location.
- Run the installer with commands such as sudo dpkg -i i2pinstall_XXX.deb or extract and run the script for the tarball.
How to Use I2P
The I2P network offers privacy-focused features to help keep your online activities secure. Here’s how you can get the most out of the application.
Browsing
Browsing on I2P involves accessing websites that are hosted within the I2P network, known as eepsites. To start browsing privately online, you first need to configure your browser to work with I2P. Firefox offers dedicated features for I2P (including extensions) and integrates well with the client. However, you can also use it with other browsers like Chrome and Brave (though Chrome isn’t the most privacy-friendly choice).
Here’s how to configure I2P with the Firefox browser:
1. Launch the I2P client and leave it running in the background.
2. Open your web browser and access the I2P Router Console by typing 127.0.0.1:7657 in the address bar.
 I2P only encrypts communications from your browser and doesn't secure other applications on your computer
I2P only encrypts communications from your browser and doesn't secure other applications on your computer
3. Access the Firefox browser preferences settings by clicking the 3 lines at the top right and then go to Settings.
 You need to configure your browser correctly to work with I2P's client
You need to configure your browser correctly to work with I2P's client
4. Scroll down to Network Settings and click Settings.
 If you don't adjust these proxy settings, your browser may show a DNS resolution error
If you don't adjust these proxy settings, your browser may show a DNS resolution error
5. On the pop up window, select Manual configuration and enter these proxy settings:
- Set the HTTP proxy to 127.0.0.1 and port to 4444.
- Set the HTTPS proxy to 127.0.0.1 and port to 4445.
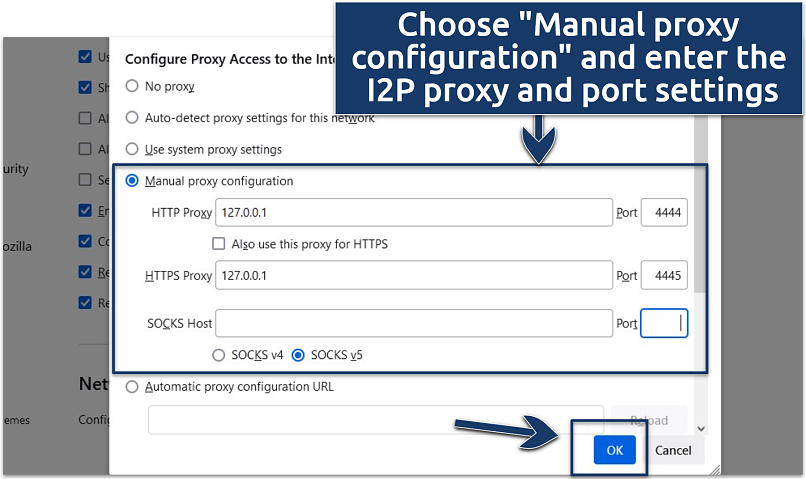 Browser extensions like FoxyProxy can make this configuration process easier
Browser extensions like FoxyProxy can make this configuration process easier
6. Click OK and check if there is now a shared clients status on the Router Console.
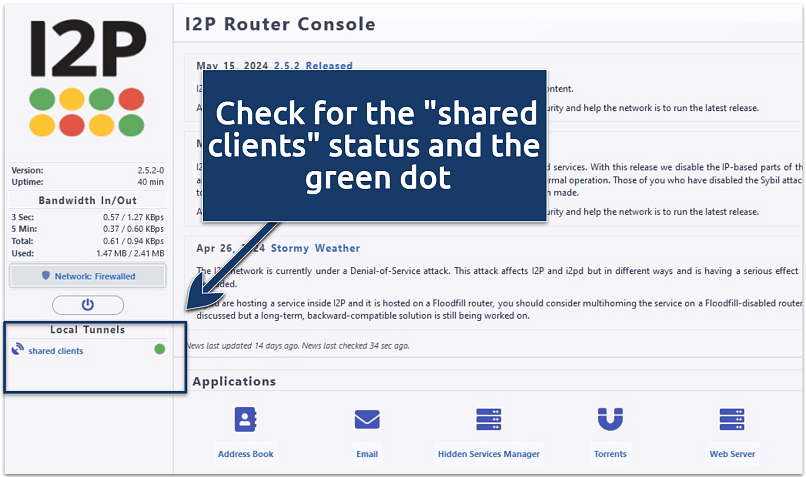 You can install additional plugins directly from the Router Console to get more browsing features
You can install additional plugins directly from the Router Console to get more browsing features
You’re all set to get started with I2P. Find useful private browsing features and links to resources in the Router Console, or enter a specific eepsite address in your browser. Any resources you subscribe to will be automatically stored in the Address Book.
Torrenting
I2P supports secure torrenting through its built-in BitTorrent client, I2PSnark. It’s also compatible with other clients like Vuze using the I2P plugin.
Here's how to go about safe torrenting on I2P:
- Open the I2P Router Console and go to the Torrents section.
- Access I2PSnark, where you can add torrent files or magnet links to privately download and upload content. I2PSnark routes your torrent traffic through the I2P network, masking your IP address in the process.
- Alternatively, you can use a BitTorrent client like Vuze with the I2P plugin for flexibility. This gives you access to torrents from the clearnet as well as the I2P network.
Email & Chats
I2P’s SusiMail feature allows you to securely send and receive emails to and from addresses inside and outside the network. You can also use I2P-Bote, a decentralized, serverless, and encrypted email system, for safe communications — but only within the I2P network.
Integrated chat apps, such as I2P Messenger (or IRC clients configured to work with I2P like HexChat or jIRCii ), also allow you to interact in real time with other I2P users.
Cryptocurrencies
I2P enhances privacy for cryptocurrency transactions by routing them through secure and encrypted tunnels. Using crypto wallets that support I2P, such as Bitcoin Core, you can hide traces of account activities by tunneling traffic via the I2P network.
How to Find Content on the I2P Network
You can discover content and useful eepsites on the I2P network through features such as:
- I2P directories. The Router Console hosts directories (like Jump Services) with lists of popular eepsites and resources.
- Search engines. The client provides its own I2P-specific search engines and tools for looking up content.
- Forums and communities. There are eepsite platforms like The I2P Planet and I2P FAQ Page, where you can post and also get link recommendations to content and resources within the network. The I2P Bug Tracker page is another useful place where network users report common issues (like I2P getting firewalled) and share possible fixes.
How to Set Up an Eepsite
Setting up an eepsite allows you to host your anonymous website within the I2P network.
Here’s how:
- Install web server software (like Apache or Nginx) on your machine.
- Configure the server to show content from a designated directory.
- Go to the I2P Router Console and navigate to the I2P Services section.
- Generate a new site key for your eepsite, which will provide a unique .i2p address.
- Bind your web server to the I2P network using the site key.
- Start your web server and share the eepsite address with others (through I2P directories, forums, or other channels).
FAQs about the I2P Network
Is the I2P network legal?
Privacy-focused networks like I2P are legal in most countries. However, dark web sites accessible through I2P are sometimes used for illegal activities, such as distributing illicit content or conducting illegal transactions. It's crucial to understand and adhere to your country's laws and regulations regarding I2P and the dark web to avoid legal trouble.
Is I2P safer than Tor or a VPN?
I2P provides a different kind of safety compared to Tor and VPNs. It's primarily designed for browsing within its private and controlled network and not for accessing the open internet. Even the underlying working mechanisms between I2P and other dark web networks differ slightly.
I2P uses garlic routing, which is robust for communications within the network. Tor uses onion routing that supports safe browsing in and outside of the network. A VPN, on the other hand, secures all your internet traffic — including browsers and applications.
Which browser should I use with I2P?
Firefox offers features that integrate well with I2P, allowing you to configure the necessary proxy settings easily. Extensions like I2P In Private Browsing (on Firefox) also offer more convenient features. You can create a separate I2P profile from your clearnet browsing activities and use it to access eepsites at any time. That said, setting up I2P for secure web access is straightforward with any supported browser, including Firefox and Chrome.
How can I fix the I2P firewalled error?
The firewalled error sometimes shows when everything is working fine, so check if you can still access eepsites first. If not, it could be that your network doesn’t allow I2P traffic to pass through. Try opening the specific ports used by I2P on your router. Enable port forwarding for ports 8887 and 8888 (or other ports if you've configured I2P differently). Also, check that any firewall software on your computer, like an antivirus, is not blocking I2P.
Wrapping Up
I2P leverages cutting-edge technologies like garlic routing and a decentralized P2P network to provide a robust platform for secure communications, anonymous browsing, and private file sharing. It has some drawbacks, like limited content (compared to the clearnet) and, sometimes unstable speeds. That said, it's a great solution for anyone enthusiastic about protecting their privacy in the increasingly monitored digital space.




Please, comment on how to improve this article. Your feedback matters!