Connected Cars Need Proper Security to Be Safe - Argus CEO
Argus is a global leader in automotive cyber security offering comprehensive and proven solutions and services to protect connected cars and commercial vehicles against cyber-attacks. With decades of experience in both cyber security and the automotive industry, Argus integrates innovative security methods and proven computer networking know-how with a deep understanding of automotive best practices. In this article, Argus co-founder and CEO Ofer Ben Noon describes the complexity of the industry and stresses that without proper security measures, no connected vehicle should be allowed on the road. Share
What's brought you to focus on Connected cars security initially?
Although Internet connectivity can make vehicles safer and more efficient, embedded connectivity exposes the vehicle to potential cyber attacks. Essentially, the more sophisticated vehicles become, the more prone they are to attack. Argus’ mission is to secure private and commercial vehicles from cyber-attacks. This is all the more important in the automotive industry as attacks could have physical consequences.
Founded in 2013, Argus has decades of experience in both cyber security and the automotive industry. Today, the Argus team consists of over fifty people, the vast majority of whom are ex-8200 military intelligence officers who collectively bring tens of decades of experience in cyber technology to the company. Argus also has hired automotive industry veterans. With the knowledge base of the team, Argus solutions and services are built for the automotive industry by automotive and cyber experts.
With headquarters and R&D located in Tel Aviv, Israel and offices next to major automotive centers in Detroit, Silicon Valley, Stuttgart and Tokyo, Argus is well positioned to play a central role in the industry for years to come.

How common are Connected Cars and how often do you encounter hacking attempts on these cars?
According to a recent Gartner report, there will be over 250 million connected vehicles on the road by 2020. While connectivity makes us more productive and vastly increases the pleasure of our ride, it opens up the possibility of data theft, espionage and the hijacking of mission critical systems such as steering, acceleration and braking through cyber attacks.
With this kind of growth in connected vehicles, some analysts go even further than the Gartner report and claim there may be close to a half a billion connected cars on the road by 2020.
Luckily, all known exploits to date have been whitehat in nature – exposed in order to raise awareness and virtually all major auto manufacturers have been affected. However, there are a slew of reasons why a hacker would potentially want to target a vehicle - hacktivism, theft, pranks, ransom, assassination and mass consequence events are all possible motivations for targeting a vehicle or a fleet of vehicles.
In a public appearance, assistant Attorney General John Carlin stated that "...the same innovations that revolutionize the auto industry create vulnerabilities if not carefully deployed. Connectivity creates access. Potential access to vehicle control systems could be used against us to undermine the very safety the technology was designed to provide".
What are the most vulnerable components in Connected Cars and what kind of risks do they impose?
Components within the vehicle that are meant to communicate with the outside world (e.g., the infotainment or telematics units) are potentially the most vulnerable to experiencing an attack. These components are part of the vehicle’s “attack surface”.
Although these units may be the most vulnerable to an attack coming from outside the vehicle, these components are connected to the rest of the vehicle’s electronic systems through the CAN bus or other in-vehicle communication network (e.g., Ethernet). Therefore, some components may be more exposed, but all components can potentially be reached if an attack breaches the first line of defense and especially if a security system is not layered.
Argus preaches end-to-end solutions and services that integrate cyber security from the concept to production phases and throughout the lifecycle of the vehicle.
To protect connected vehicles today and into the future, solutions need to be technologically innovative and combine cyber security know-how with automotive best practices.
There is no silver bullet that can effectively protect against all dynamic, sophisticated cyber attacks. What is needed is multi-layered protection to prepare the vehicle or vehicle fleet for virtually any scenario.
Securing a moving vehicle from a cyber attack is vastly different from securing a computer, as solutions need to be low-latency, high performance and need to be ready to embed into a vehicle’s existing architecture. Automotive cyber security companies should also be able to act as trusted cyber security advisers that can escort customers from the design stage right through to incident response if needed.
Argus offers the industry’s most comprehensive, multi-layered solutions and services. We are a one-stop-shop for automotive cyber security solutions and services.
It seems that the more sophisticated modern cars become, the more vulnerable they are to cyber-attacks. If that is the case, why would anyone want to use those cars?
Vehicles with advanced connectivity modules are more prone to attack than those without such components. Whereas one could potentially resort to only driving cars or trucks built before 1996 (i.e., the year that OBD-II became mandatory for all cars sold in the USA), motorists and passengers today expect services and experiences that are only available via advanced technology and connectivity. As such, this strategy is not entirely feasible.
The more a vehicle becomes connected to the internet (and reliant on it to perform safety critical functions, think Advanced Driver Assistance Systems (ADAS) and autonomous driving), the more likely and susceptible that vehicle is to being the target of a cyber attack.
It may be a surprise to some, but many private and commercial vehicles already use autonomous and ADAS features on the road today. Lane keep technologies, assisted parking and vehicle summoning are only a few of the advanced technologies in use today.
Looking forward, its no secret that vehicle connectivity will be an inseparable part of our lives. Given this fact and our desires to benefit, cyber security must be integrated into the entire vehicle lifecycle - from concept phase through production, servicing and decommission. Without computer security taken into account at each stage, vehicles will be susceptible to attack.
Once an attacker has managed to hack the vehicle’s internal communications, how easy is it to take control of additional modules, such as the steering wheel, the speed, the brakes, the ABS, ECU and the engine?
Without multiple layers of cyber defense, malware that has breached an attack surface can potentially influence any of the vehicle’s electronic control units (ECUs). This would require the hacker operating the malware to have an understanding of the messages sent between the various ECUs over the vehicle’s in-vehicle network and the CAN (control area network) bus.
Does your system also protect the privacy of the driver? for example, can it prevent an attacker from tracking and eavesdropping the vehicle?
Yes, one of Argus solution suites, specifically Argus Connectivity Protection, is designed to defend against such scenarios. Among other things, this suite prevents suspicious, modified or otherwise unauthorized applications from communicating with the telematics or infotainment unit. Thus, we are able to prevent eavesdropping and location tracking. Additionally, Argus Connectivity Protection secures the two-way communication channel with the outside world and operates across platforms (e.g., Linux, QNX, Android & others) to protect the vehicle’s most vulnerable attack surfaces.
A recent KPMG study revealed that 82% of consumers would be “wary” or would “never buy again” from an automaker if they had been hacked. This is clearly problematic for the manufacturers, which is why we help our customers take proactive cyber security measures that can significantly strengthen their cyber posture. It can also reduce any eventual costs in case of an incident.
Who are your main customers? Are we talking about car manufacturers only or are there any other markets that benefit from your system?
Argus is a software and services company that works with private and commercial OEMs, Tier 1s, aftermarket connectivity providers, fleet managers, insurance companies and dealerships to secure connected cars, commercial vehicles and connected vehicle fleets from hacking.
Argus also acts as a trusted security advisor by leveraging the unique automotive domain expertise of Argus research team. Through services such as threat analyses, risk assessments, vulnerability analyses, code reviews, penetration testing, incident response and cyber threat intelligence, Argus helps customers integrate cyber security into each stage of the vehicle lifespan and during any emerging cyber security situation facing the organization.
How likely are we to see connected cars technology implemented on military operations and public transport networks?
Rental fleets, public bus fleets, dealerships, the military, insurance companies and others are all responsible for the operation of thousands and at times even millions of vehicles. In each case, the organization is responsible for the safety and privacy of the vehicles used in their name. Therefore, Argus is already working to secure the vehicles and specific use cases that these types of businesses rely on.
When considering the future of the automotive industry, it becomes evident that the presence of cybersecurity measures is imperative for every vehicle on the road. Failing to implement such measures exposes not only motorists and passengers but also pedestrians to the potential danger of physical harm.
We understand that your IDPS system will generate reports and alerts for remote monitoring of a vehicle’s cyber health. What will this report include? Can you offer an example to "healthy" vs. "infected" Car?
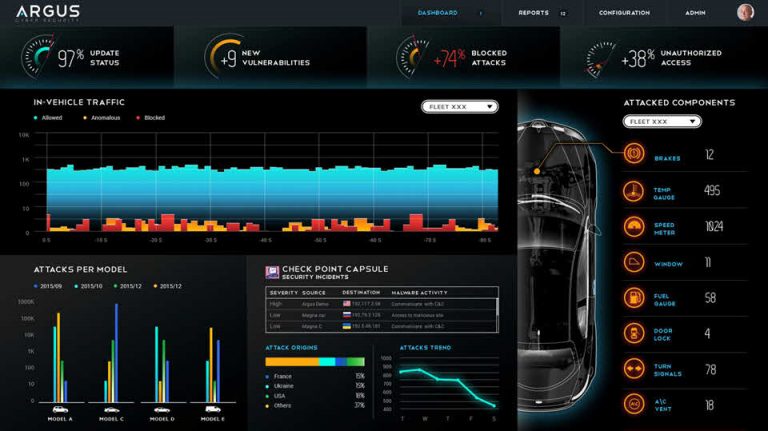
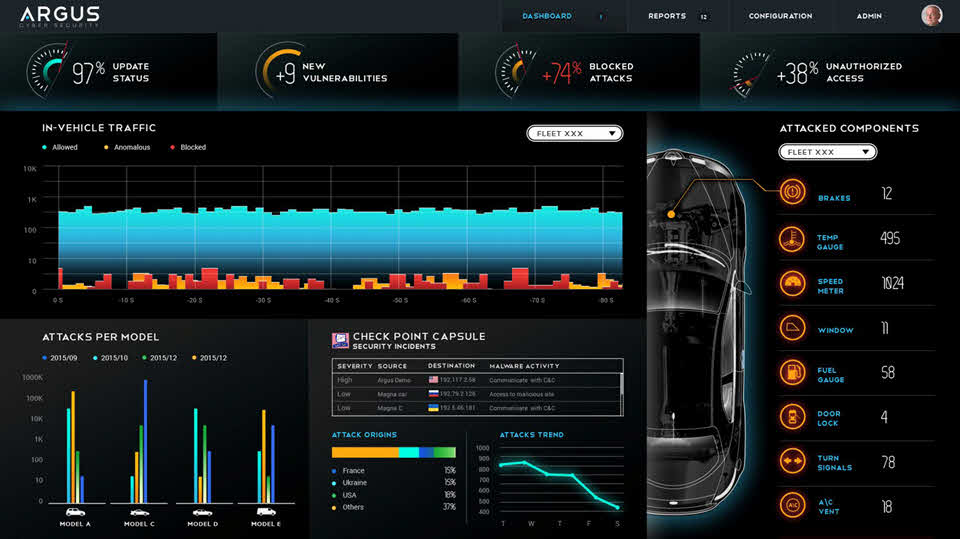
Below is our dashboard that works in the cloud. Argus IDPS, as well as any other Argus in-vehicle solution, can work standalone or in conjunction with ArgusCloud. ArgusCloud enables event drill down, forensics, automated insights as well as the ability to send OTA updates to the vehicle fleet.

Does your solution require any special architectural modifications? Can you describe the integration process?
Argus solution suites are easily adaptable according to a specific vehicle’s architecture, and do not require any architectural modifications to a vehicle. Each car is designed in a unique way and is exposed to attacks in accordance with how it is built. Because of these design inconsistencies in private cars, cyber security solutions must be flexible and tailored to vulnerabilities that are unique to specific vehicles.
On the other hand heavy duty trucks and commercial vehicles share a common communication standard, J1939, that makes it possible to craft "one size fits all" attacks that are instantly scalable. This makes a basic level of security easier to implement across a variety of truck fleets, but these solutions need to be sophisticated to account for the standardized access points across these commercial vehicles.
Why, in your opinion, Telematics Service Providers offering Smart Driving Assistance, Remote Diagnostics systems and Usage-Based Insurance solutions are at high risk of being hacked?
By definition, wireless services can potentially be hacked. The reason they are so dangerous is because they could be the means by which malware is unknowingly introduced into the in-vehicle network and as we've discussed, unauthorized messages sent over the in-vehicle network are potentially harmful to motorists and passengers.
One might assume that the automobile industry had taken precautions and will always evaluate the passenger's safety first. Do you agree?
Passenger safety and satisfaction are the foremost concerns for automakers. At the end of the day, the manufacturers have a lot at stake – if they don’t ensure the safety of their customers, everything else comes crashing down.
Since cyber security is still a relatively new consideration for car makers, Argus is working with them from concept to production and throughout the vehicle lifespan on protecting against any and all potential security lapses. Argus specializes in implementing layers of cyber security solutions in connected vehicles and in helping OEMs establish the policies and processes related to cyber security inside their organizations.
Do you offer any threat assessment services or penetration testing for car models?
Argus offers a suite of consulting services that help integrate cyber security practices and processes into entire product lifecycles. Through services such as threat analyses, risk assessments, vulnerability analyses, code reviews, penetration testing, incident response and cyber threat intelligence, Argus helps customers integrate cyber security into each stage of the vehicle lifespan and during any emerging cyber security situation facing the organization.
Working with customers both on and off-site, from concept phase to production and aftermarket, Argus research team helps identify existing and potential risks, threats and vulnerabilities in vehicle network elements and other key components, all the while preparing customers for emerging regulations.
Argus has performed these services for major OEMs and Tier 1s. In each instance of evaluating current and future vehicle architectures, Argus found vulnerabilities that have the potential to severely endanger the safety and privacy of motorists and passengers.
One could only imagine what a cyber terrorist could do to a car if not protected… can you tell us more from your personal experience how your technology can prevent or in fact already prevents these acts of terror?
There are many potential motivations and methods of vehicle hacking - from theft to ransomware, from hacktivism to pranks and possibly even terrorism.
Argus solution suites were built from the ground up by experts in both cyber security and the automotive industry. Argus detects, prevents and isolates suspicious activity and cyber attacks through an end-to-end offering that defends both the attack surfaces and components buried deep inside the network.
Argus products are highly modular and can be applied selectively in accordance with the specific wants and needs of the customer. Argus products and personnel can also be found at every stage of the vehicle lifecycle from the design and concept phases through to vehicle servicing, event response and more.
What changes can we expect to see in the connected cars industry over the next 5 years?
As cars become more advanced they become more vulnerable to cyber attacks. The automotive industry, regulatory bodies and organizations such as insurance companies that are directly affected by the heightened attack landscape will need to work towards a stronger automotive cyber security posture. The resulting ecosystem will need to proactively implement advanced security measures, such as the best practices offered by Auto-ISAC this month and regulations such as the Spy Car Act proposed by Senators Markey and Blumenthal.
Argus sees the industry changing in profound ways. Connectivity is at the heart of that change and will be an enabler for a whole array of products and services. It will also facilitate the implementation of autonomous driving. However, just as the services offered get more sophisticated, so too will the attacks on vehicle networks.
Technologies such as vehicle to vehicle (V2V) and vehicle to infrastructure (V2X) communication will further enrich and complicate the auto-transport environment. The sophisticated data streams enabling these technologies will surely make our roads safer but the more data we send to and from vehicles (and to and from the infrastructure that governs their movements) increases the potential for attack. Car makers and the industry at large need to stay ahead of these threats.
More sophisticated media content, navigation data, telecommunications and even personal banking information into and out of vehicles make our livelihoods and safety dependent on the proper implementation of automotive cyber security. Moreover, without cyber security, autonomous driving simply cannot be implemented safely.



Please, comment on how to improve this article. Your feedback matters!