40+ Ethical Hacking Statistics
The online world can feel like the Wild West. With digital threats lurking at every corner, it's easy to feel vulnerable. Enter ethical hackers — our very own cybersecurity sheriffs. Unlike malicious hackers, these professionals use their skills for good, working diligently to identify and fix weaknesses in computer systems and networks.
Year after year, ethical hackers continue to uncover an increasing number of software vulnerabilities. This consistent rise highlights both a growing problem and also the growing skillset and unique ability of ethical hackers to spot weaknesses that might elude traditional scanning tools.
In this article, we're diving deep into the captivating world of ethical hacking. I’m bringing you 44 intriguing facts and figures that touch upon everything from the history and career prospects of ethical hacking to the demographics of ethical hackers and the interplay between cybercrime laws and their victims.
Jump to the article’s Glossary of Terms for definitions of some of its technical language.
Introduction to Ethical Hacking
Traversing the fine line between defense and exploration, ethical hacking is a discipline in which cybersecurity meets creativity. This introductory section looks at the history, evolution, and key milestones of ethical hacking.
1. Hacking Origins

Hacking, originally meaning "cutting violently," began its association with technology in the mid-20th century. In 1955, the Technical Model Railroad Club used "hacking" to describe skillful modifications to train sets, highlighting creativity and expertise. As computing grew in popularity, "hacking" also referred to computer enthusiasts pushing technological boundaries.
By 1975, "hacking" became synonymous with cybercrime, indicating the process of seeking unauthorized access to data, often illegally. Today, "hacking" describes exploiting computer system vulnerabilities for unauthorized access. Such actions are illegal and have severe repercussions for perpetrators who are caught. The term now covers both innovative technical skills and illicit cyber activities.
2. Why Does Ethical Hacking Exist?

Ethical hacking, often referred to as "white hat" hacking, is the practice of authorized professionals assessing system security by simulating real-world cyberattacks. The primary goal is to identify vulnerabilities and strengthen defenses. Unlike malicious "black hat" hackers, ethical hackers work with the consent of organizations to protect digital assets and confidential information.
Some ethical hackers aren’t formally authorized to assess a company’s vulnerabilities. Instead, they search the web for open vulnerabilities that bad actors might exploit, which can commonly be found in cloud data storage. They aim to report any found weaknesses to the respective companies, contributing to consumer safety. While some companies act upon these findings, others may not, leading to varied outcomes in addressing these security gaps.
The role of ethical hacking has become crucial in recent years, paralleling the rise in cybercrime. As the volume and sophistication of cyberattacks grow, so does the reliance on these skilled and vigilant professionals to safeguard data.
3. Hacking and Cybercrime Legislation

Malicious hacking activities surged in the late 20th century, which gave rise to the need for robust cybersecurity. This led to the enactment of cybersecurity laws like the Computer Fraud and Abuse Act (1986) and the Computer Misuse Act (1990), which made malicious hacking illegal. Following the enactment of these laws, organizations began recognizing the importance of employing ethical hackers to strengthen their security systems.
4. Early Ethical Hackers

Today’s ethical hacking landscape was significantly influenced by several people who initially operated in legal gray areas. These early hackers eventually transitioned to legitimate practice, playing pivotal roles in shaping the industry:
- Kevin Mitnick: While he began his hacking career on the wrong side of the law, Mitnick later transformed himself into a white hat hacker, consultant, and author. He is often cited in discussions about the early days of ethical hacking due to his high-profile exploits and subsequent reformation.
- Robert Tappan Morris: In 1988, Morris created the first worm to spread across the internet. It was intended to measure the internet’s size but caused unintended damage and highlighted vulnerabilities in many systems. Morris later co-founded Viaweb, which was acquired by Yahoo.
- Gary McKinnon: While his actions were not initially "ethical," his high-profile hacks into 97 U.S. military and NASA computers between 2001 and 2002 were driven by curiosity rather than malicious intent. He claimed to be searching for evidence of free energy suppression and UFO cover-ups.
- Adrian Lamo: Known as "The Homeless Hacker," Lamo identified vulnerabilities in several large corporations but then informed them of their weaknesses, often offering advice on how to fix them.
5. Popular Ethical Hacking Techniques

One of the primary techniques ethical hackers use is penetration testing. In this, authorized professionals pinpoint and exploit vulnerabilities by mimicking real-world cyberattacks on computer systems. In this way, they help organizations proactively detect weak spots, helping close off potential entryways for cybercriminals. This practice, rooted in the early days of ethical hacking, remains a cornerstone in the fight against cyber threats.
Other popular techniques include:
- Vulnerability Scanning: Automated software scans a system for known vulnerabilities, providing a snapshot of potential security weak points.
- Social Engineering Attacks: Simulated attacks, such as phishing emails or impersonation, test how employees respond. They aim to raise awareness and train staff against real scams.
- Network Traffic Analysis: Monitoring and analyzing network traffic to identify suspicious patterns or unauthorized data transfers, often using tools like Wireshark.
- Web Application Testing: Testing websites and web applications for vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF) to ensure they're resistant to potential cyber threats.
6. Major Milestones in Ethical Hacking

From the early days of phone phreaks in the 1970s to the rise of formal ethical hacking education through the 2020s, the journey of ethical hacking has been marked by significant milestones. This timeline captures the evolution of hacking from a subculture hobby to a recognized profession essential for global cybersecurity.
By the 2000s, companies like Google began offering "bug bounties" to ethical hackers, and by 2020, hackers had earned over $100 million in bounties through platforms like HackerOne, showcasing the immense value of ethical hacking in today's digital age.
Ethical Hacking Industry and Careers
Ethical hacking brings skill, strategy, and purpose into the realm of cybersecurity. In this section, we look at the industry's expansion, the dynamic roles of ethical hackers, and the emerging trends that are sculpting their professional paths.
7. What Motivates Ethical Hackers?

Ethical hackers have varied reasons for what they do. 80% are driven by the potential earnings, which is up from 71% in 2022. Learning remains a key motivator as well, with 78% hacking to broaden their knowledge and expertise, slightly down from 79% the previous year.
Beyond personal gains, 47% are on a mission to protect businesses and their users, emphasizing their role as digital guardians. And even though nearly 66% are hacking part-time, almost one-third of ethical hackers have a day job in cybersecurity.
8. Which Industries Use Ethical Hackers the Most?

2022 marked a significant shift in the embrace of ethical hacking across industries — it was the newer sectors that truly shone in terms of growth. The pharmaceutical industry, for instance, accelerated its adoption of ethical hacking programs by a remarkable 700%. The automotive industry wasn’t far behind, registering a 400% growth.
Overall, the year witnessed a 45% surge in program adoption, highlighting the widening recognition of ethical hackers' invaluable role in bolstering cybersecurity.
9. What Tools Do Ethical Hackers Use?
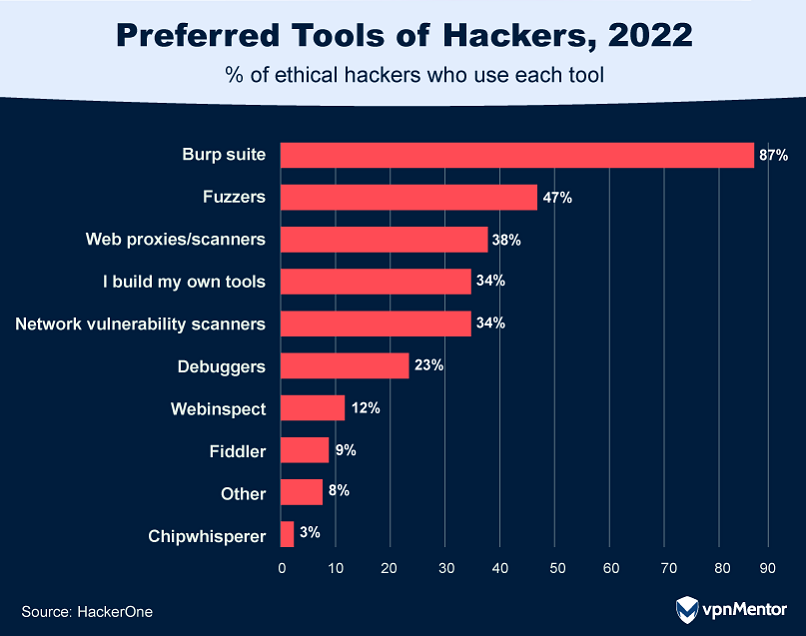
With 88% of hackers noting an increase in attack surfaces — the vulnerable points in a computer system, network, or software where unauthorized access can occur — the importance of advanced tools to secure these areas is critical.
To tackle these vulnerabilities, 87% of hackers rely on tools like Burp Suite, while 34% have taken the initiative to create their own specialized tools.
10. How Many Vulnerabilities Do Ethical Hackers Find?

A whopping 92% of ethical hackers believe they can spot online weaknesses that computer programs miss. In 2022, they found over 65,000 issues that could have affected customers. As more businesses have gone digital, problems like misconfigurations have jumped by 150%, and authorization issues have risen by 45%. This shows just how vital human expertise remains, even in our tech-driven world.
11. Top Vulnerabilities Ethical Hackers Cashed In On
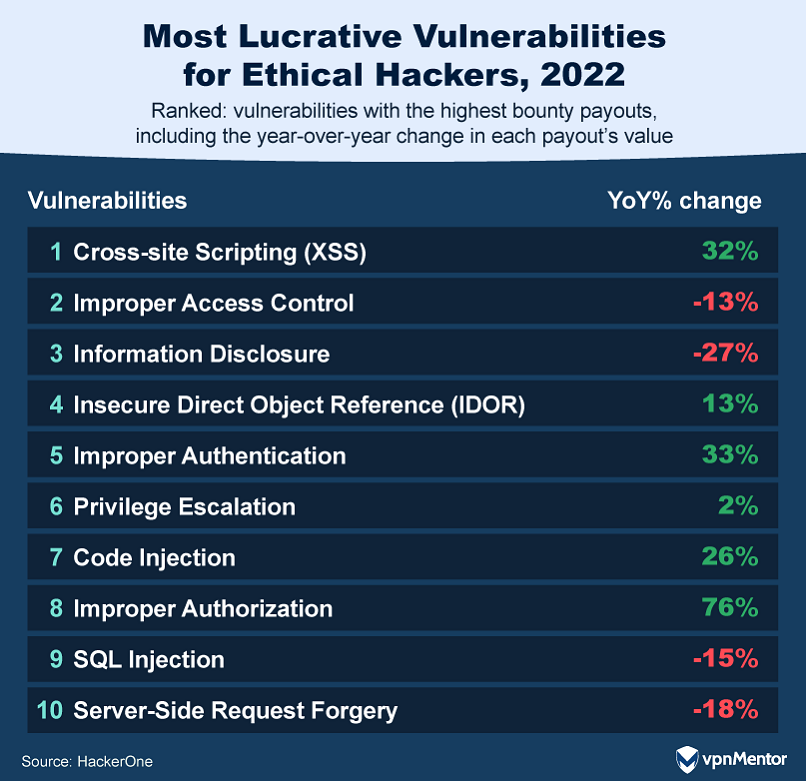
Some vulnerabilities have been more lucrative than others for ethical hackers in the past few years. In 2022, Cross Site Scripting (XSS) saw a notable uptick, with a 7% rise in reports and a whopping 32% increase in payouts. However, as this bug is relatively easy to rectify, incidents of XSS should decrease as companies enhance their security protocols.
The era of digital transformation, marked by cloud transitions and remote work, has also reshaped the vulnerability landscape. As apps introduce more detailed user permissions, vulnerabilities like Improper Authentication and Improper Authorization have seen a surge in payouts. This complexity in user access controls has inadvertently opened new avenues for potential exploitation.
12. Why Half of Hackers Withhold Vulnerability Findings

In 2022, 69% of organizations admitted to having faced a security incident in the past year. Yet, a surprising 50% of hackers opt not to share their findings. Why?
The leading reason, at 42%, is straightforward: Many organizations lack a formal vulnerability disclosure program. Additionally, 12% of hackers are deterred by intimidating legal language on program pages. On a brighter note, recent amendments to the U.S. Department of Justice's Computer Fraud and Abuse Act (CFAA) seem promising, with two-thirds of hackers believing these changes will bolster hacking protections.
13. What Specialized Skills Do Ethical Hackers Have?
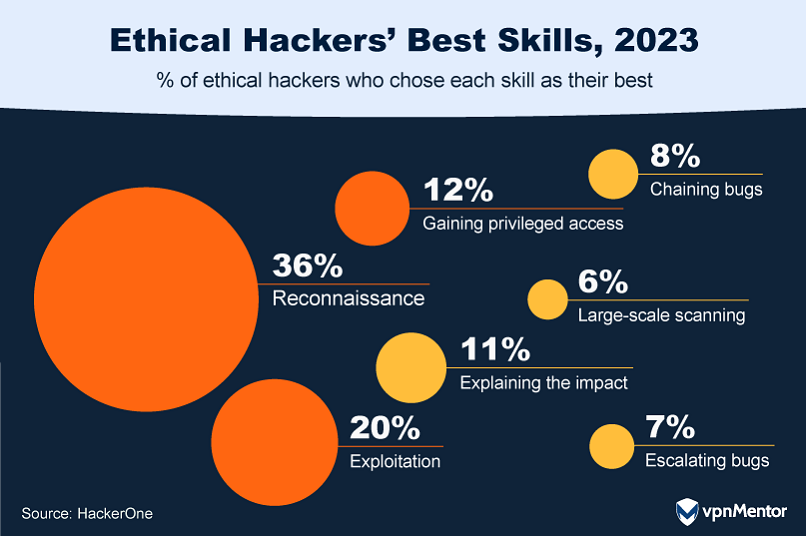
Regarding the specialized skills within the ethical hacking community, 36% of ethical hackers pinpoint reconnaissance as their area of expertise. This critical phase of information gathering aims to identify as many potential attack vectors as possible, laying the groundwork for understanding a system's landscape and planning subsequent security measures.
20% consider themselves proficient in exploitation, a skill that involves taking advantage of identified vulnerabilities to understand how they may be misused by malicious hackers. They simulate attacks to reveal the potential impact of a real-world breach.
14. How Hackers Develop Their Skills and Knowledge

In the ever-evolving landscape of cyber threats, security professionals are constantly seeking effective ways to develop their skills and knowledge. Practice emerges as the top method for development in both ethical hacking and general information security, with the majority of respondents emphasizing its importance.
Following closely, bug bounty hunting is also a popular approach, chosen by 50% of hackers as a key avenue for learning general information security. This method significantly outstrips traditional job-based learning, which was only chosen by 11%. Additional resources include reading blog posts and write-ups and engaging with online tutorials and hacker interviews.
15. The Rise of Generative AI in the Hacker Toolkit
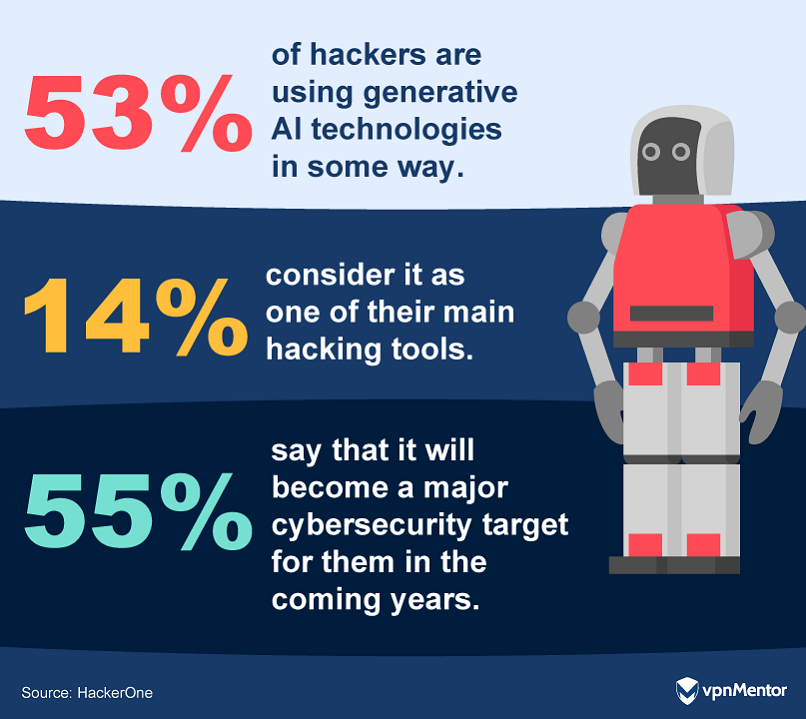
Generative AI (GenAI) is rapidly becoming an integral part of the ethical hacking toolkit, with over half of ethical hackers using it in some capacity. 66% plan to use GenAI for enhancing their reporting, 53% for coding, and 33% for overcoming language barriers.
However, with the adoption of GenAI, new challenges emerge. A substantial 55% foresee GenAI tools themselves becoming major targets. While 38% believe GenAI will reduce vulnerabilities in code, 43% predict an increase in areas such as criminal exploitation and disinformation, as well as in poorly written code that creates vulnerabilities for organizations.
16. What Draws Ethical Hackers to Specific Programs?
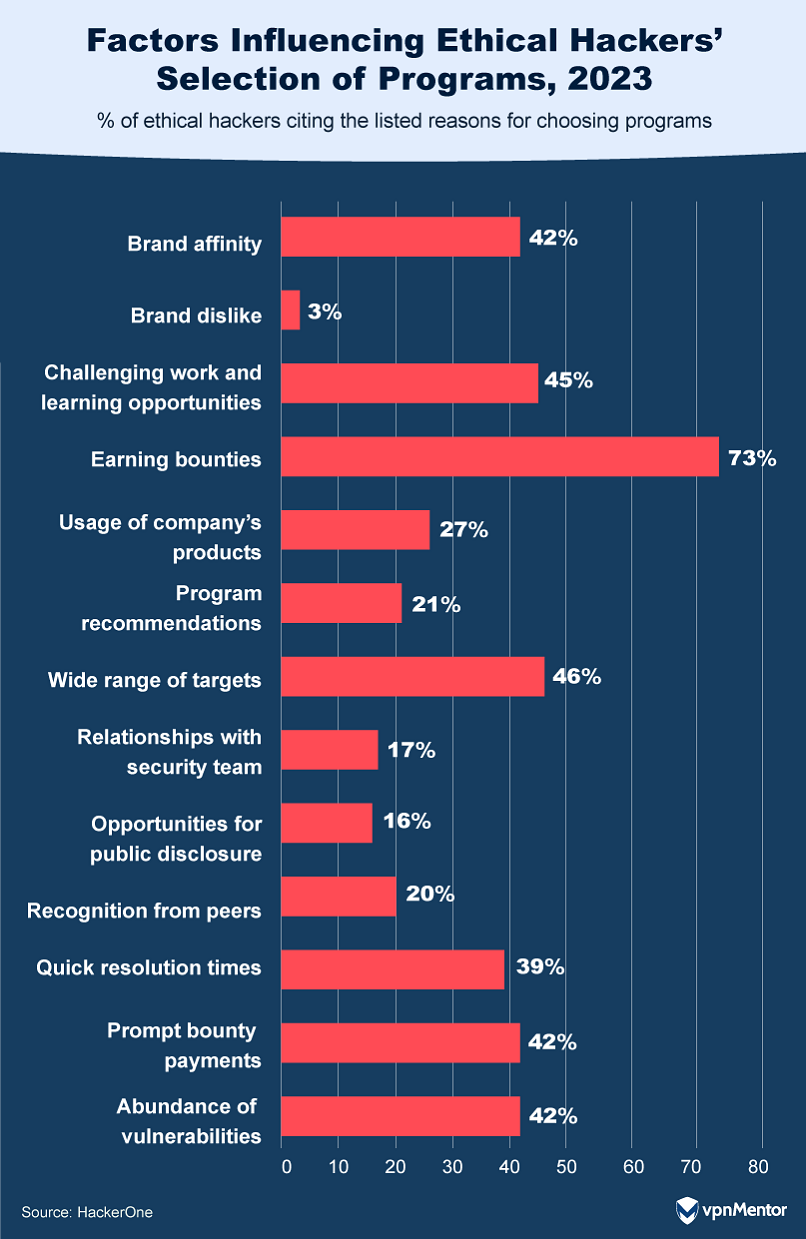
When it comes to selecting their targets, ethical hackers have clear preferences. The allure of bounties stands out, with 73% of hackers gravitating toward programs offering the best rewards. Varied scope is another key factor; 46% value the field of systems, applications, and challenges available for testing within a program.
Brand affinity also plays a role, influencing 42% of hackers in their choice. But lesser-known brands can still attract and benefit from ethical hackers. By adhering to program best practices — like maintaining regular communication, rewarding promptly, and addressing bugs swiftly — they can pique the interest of the hacking community.
17. Industry Response Time for Vulnerabilities Found by Ethical Hackers
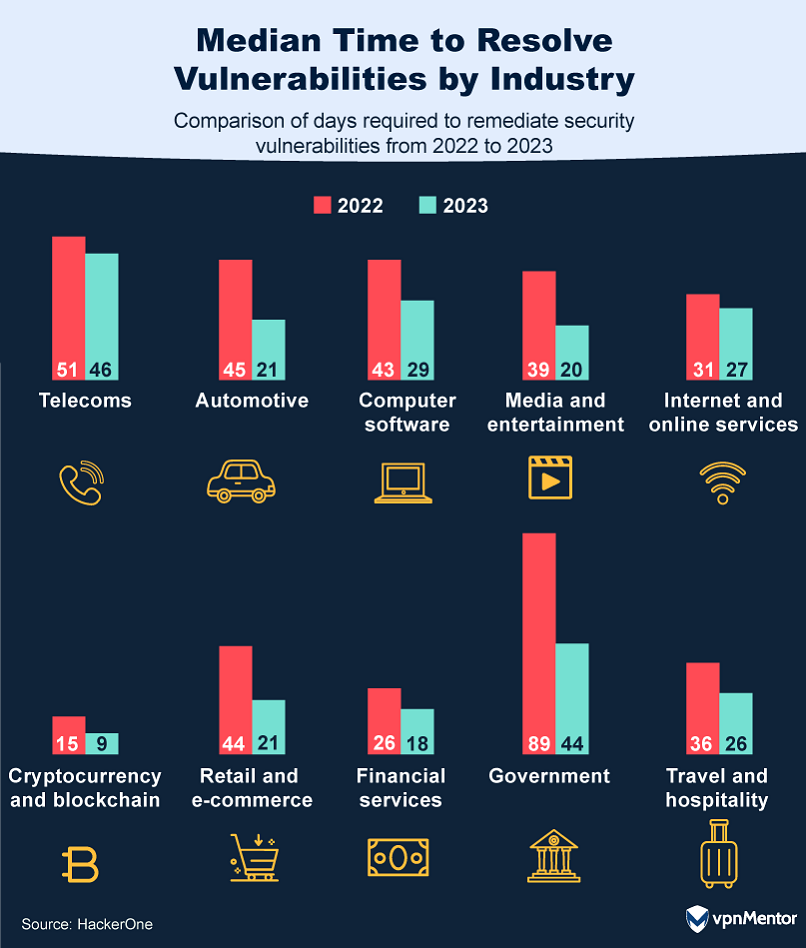
Inefficient communication channels and slow response times create roadblocks that deter ethical hackers and increase the costs for companies. When looking at a year-on-year comparison of the median time to remediation — the time taken to address vulnerabilities — we can see that in 2023, it dropped to just 25.5 days, from 35.5 in 2022.
On average, compared to companies that respond more slowly, a company can save over a million dollars if it can identify and contain a breach in less than 30 days. This makes it crucial for companies to have effective response plans that lay out how communications will be handled and threats responded to.
Significant enhancements were seen in the automotive industry, which cut down its resolution time from 45 to 21 days. Government agencies decreased from 89 to 44 days, underscoring a concerted effort to resolve risks more quickly.
18. How Much Money Do Ethical Hackers Save Companies?
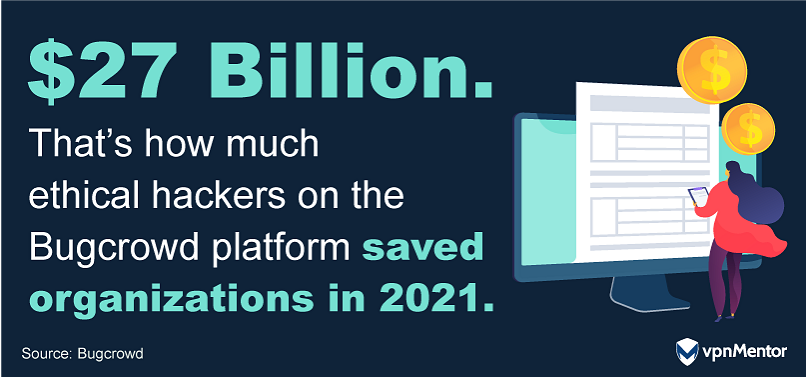
In 2021, the collective efforts of ethical hackers on the Bugcrowd platform — a crowdsourced security platform, and one of the world’s largest bug bounty and vulnerability disclosure companies — were monumental, safeguarding organizations from potential cybercrime amounting to over $27 billion.
This figure represents the efforts of the 59% of ethical hackers who are part of the Bugcrowd community. It also suggests an even larger, though unquantified, impact when considering the full spectrum of the ethical hacking community, which includes other platforms as well as independent researchers.
19. The Effects of Ethical Hacking on Career Development
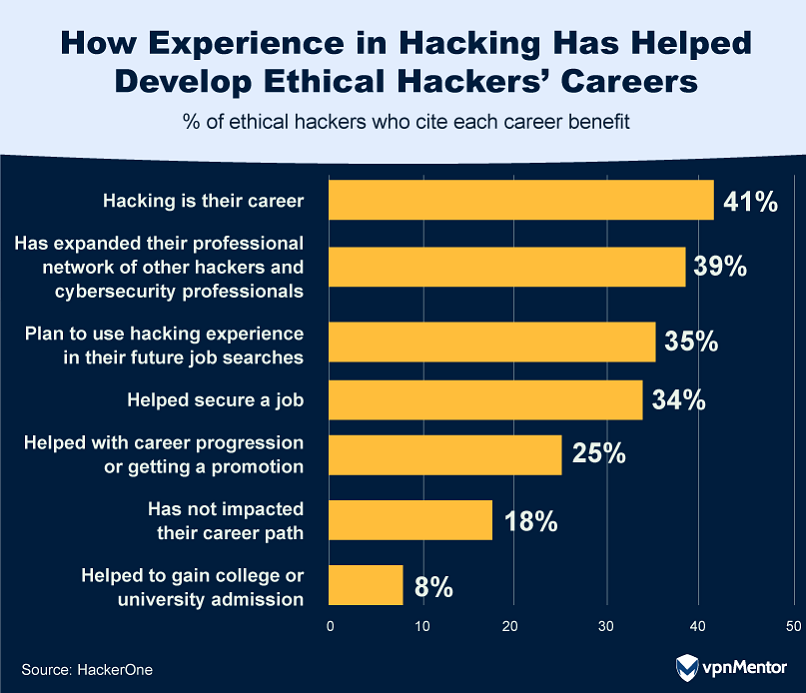
Ethical hacking is proving to be more than just a skill; it's a significant career accelerator in the field of information security. 35% of hackers have landed a job thanks to their hacking experience, and 26% credit it with helping them achieve a promotion or advance in their career. Even more telling, 41% view hacking not just as a skill or hobby but as their chosen career path.
20. How Much Do Ethical Hackers Make?
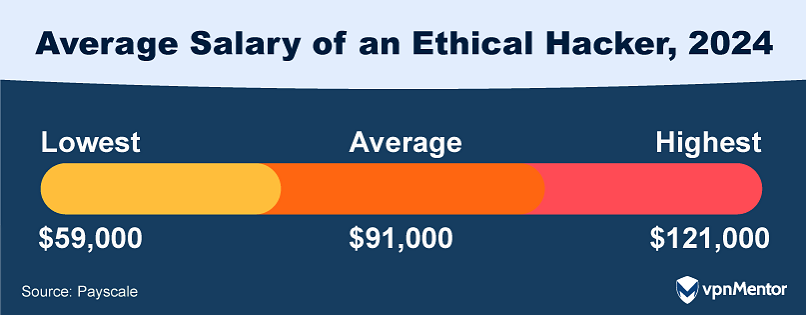
Ethical hacking is both an essential component of cybersecurity and also a lucrative career path. As of 2024, the median annual salary for ethical hackers stands at approximately $91,000 according to Payscale. Meanwhile, top-earning ethical hackers can make well over $100,000.
The job outlook for ethical hackers is robust, with the U.S. Bureau of Labor Statistics projecting a 15.2% growth for all computer and IT occupations from 2022 to 2032, and an even more impressive 31.5% growth for information security analysts. This makes it the fifth fastest-growing occupation in the economy.
This growth, translating to over 377,500 new job openings each year, is driven by increased cyberattacks, the rise in remote work, growing reliance on web-based shopping, and the expanding use of digital health services.
21. Companies Offering the Highest Salaries for Ethical Hackers
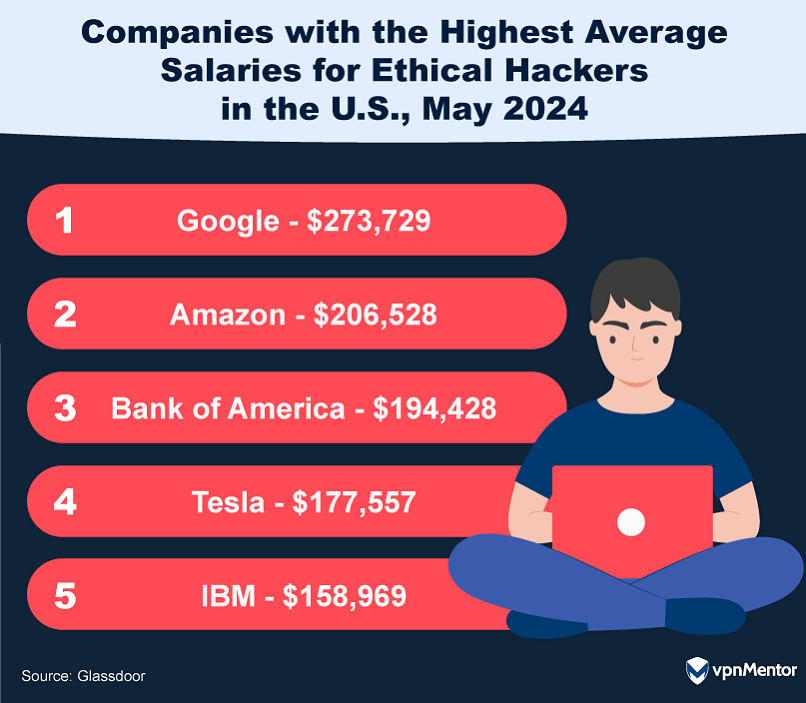
In the competitive world of ethical hacking, tech giants are leading the way in both salary and benefits. As of early 2024, Google tops the list with an average annual salary of $273,729, followed by Amazon at $206,528. Bank of America, Tesla, and IBM are also strong contenders.
These high salaries are often accompanied by comprehensive benefits packages, ranging from health care and paid parental leave to retirement plans and performance-based bonuses, making ethical hacking a lucrative career path in these top-tier companies.
Ethical Hacking Demographics
In the realm of ethical hacking, demographics shape perspectives and influence the landscape. This section explores how an ethical hacker’s background impacts their roles and contributions.
22. How Old Are Ethical Hackers?
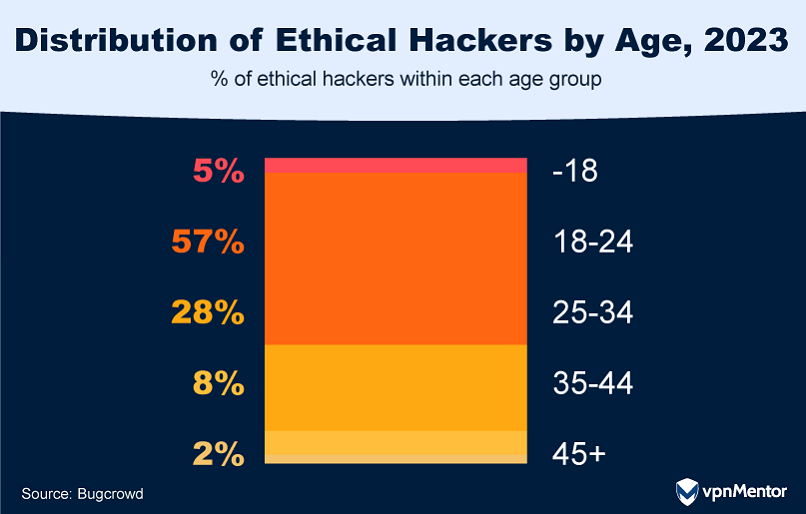
The world of ethical hacking is getting younger. Most ethical hackers are now from Gen Z, the group of people born between 1997 and 2012. They're followed closely by Millennials, who were born between 1981 and 1996. What's interesting is that the number of hackers under 18 has more than doubled in the last year. This is probably because it's easier than ever to learn hacking skills online, which gives young people access to the tools they need to be involved in making the digital world safer.
23. Racial and Ethnic Inclusivity in Ethical Hacking
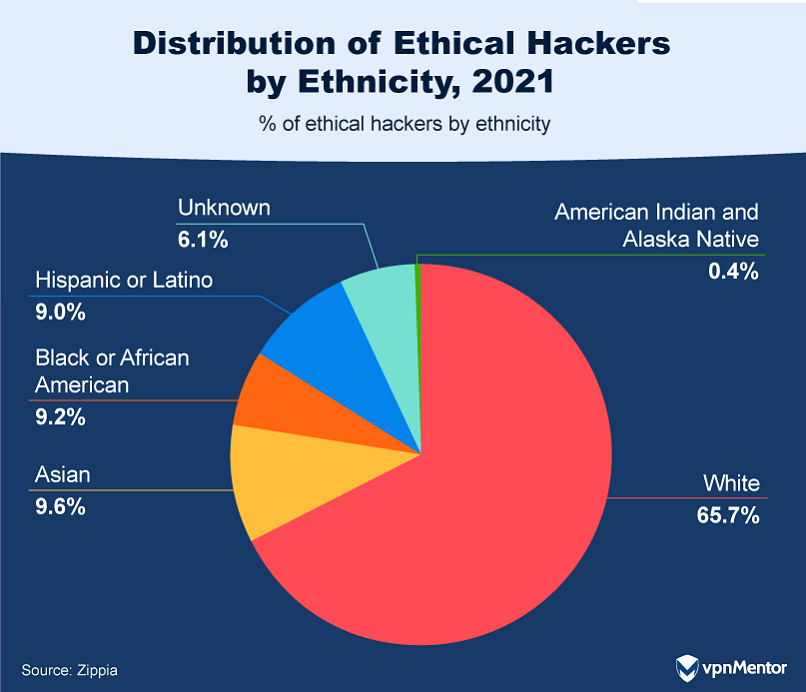
Over the past decade, the field of ethical hacking has experienced a transformation in racial and ethnic diversity. As it stands, the community is predominantly composed of people of European descent, accounting for 65.7%, followed by Asians at 9.6%, Black or African Americans at 9.2%, and Hispanic or Latinos at 9%.
Comparing these figures to those from 2010, there is a clear increase in representation from various racial and ethnic groups. This shift highlights a positive trend toward greater diversity within the ethical hacking field.
24. How Race Affects Earnings in Ethical Hacking
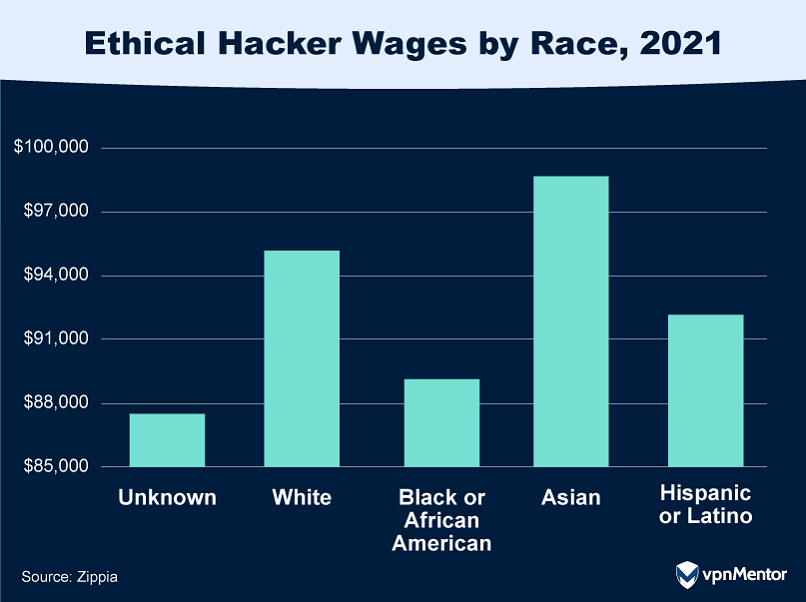
The ethical hacking field in the U.S. reveals intriguing insights into the wage disparities among different racial and ethnic groups. A recent analysis highlights that Asian hackers lead the way in terms of annual salary, earning an average of $98,769 per year. This is closely followed by white hackers earning $95,174, and Hispanic or Latino hackers at $91,847.
These figures underscore the earning potential within the field while also raising questions about the underlying factors contributing to these wage variations.
25. Women in Ethical Hacking on a Decline
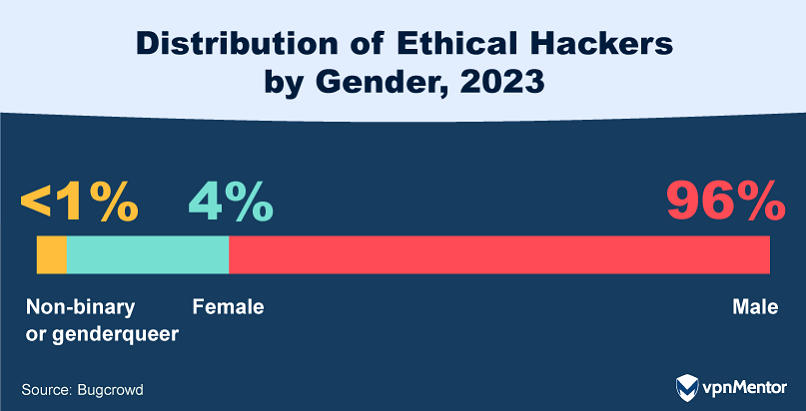
The ethical hacking community shows a significant gender imbalance, with 96% identifying as male. This marks a decline in female representation from 2020 when 6% of hackers were female. The pandemic's added pressures, such as increased childcare responsibilities, may have contributed to this decline. This gender disparity threatens the diversity and range of perspectives that make crowdsourced security so effective.
26. Gender Pay Gap in Ethical Hacking

In the field of ethical hacking, the gender pay gap is a reflection of a broader trend across industries. As of the latest data, women in ethical hacking earn 93 cents for every dollar earned by their male counterparts, with average incomes of $85,903 for women and $92,392 for men.
This discrepancy is consistent with the overall gender wage gap in the United States, where women earned an average of 82% of what men earned in 2022. Interestingly, the gap is smaller among workers ages 25 to 34, where women earned 92 cents for every dollar earned by men.
27. Education-Earnings Connection in Ethical Hacking
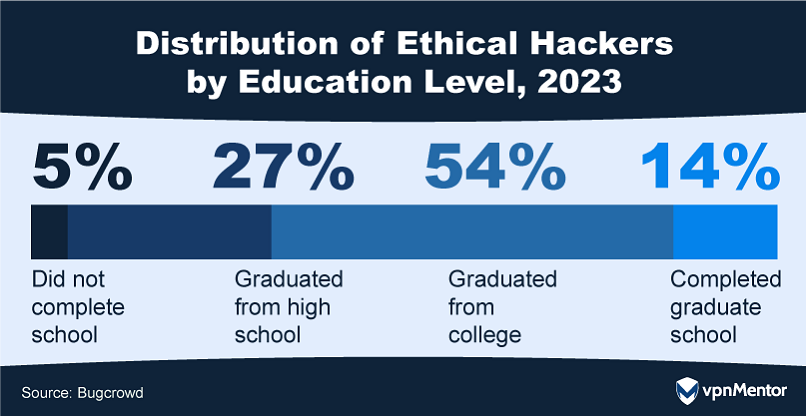
Contrary to stereotypes that paint hackers as hoodie-wearing basement dwellers or government-controlled geniuses, the reality is more nuanced. A majority of 68% of hackers are college graduates, highlighting that this community is well-educated.
Their resourcefulness, critical thinking skills, and subject matter expertise are increasingly in demand, underscoring the value of their educational background in today's complex cybersecurity landscape.
28. The Multilingual Landscape of Ethical Hacking
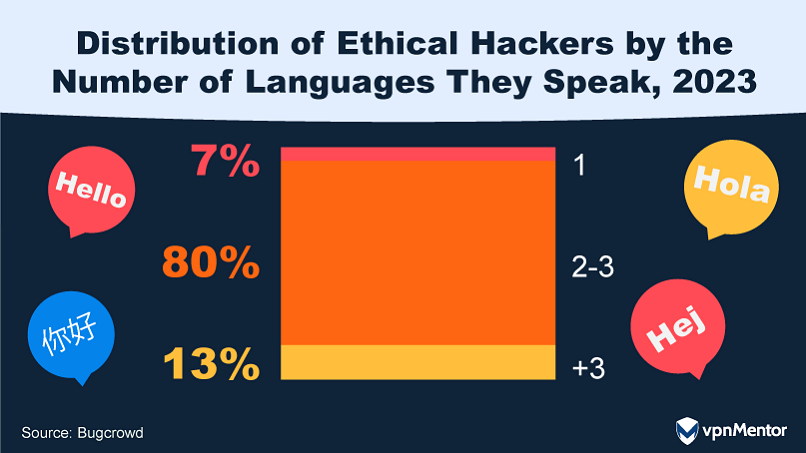
The ethical hacking community is a linguistically diverse group, with 93% of hackers fluent in at least two languages. This multilingualism not only adds to their creativity but also enhances their ability to multitask and adapt to changing scenarios.
Studies show that hackers from non-English speaking countries are increasingly using AI technologies like ChatGPT as translators. This helps them better understand their targets and aids in report writing, showcasing how they're leveraging technology to navigate the predominantly English-speaking digital landscape.
29. Where Do Ethical Hackers Call Home?

Ethical hackers are a global community, and a recent report from Bugcrowd reveals just how diverse this landscape is. The top 10 countries where ethical hackers reside span continents, cultures, and time zones — from India and Bangladesh to the United States and Brazil.
This geographic diversity enriches the ethical hacking community and also brings a wide array of perspectives and skills to the table. So, forget the outdated image of a hacker in a basement; today's ethical hackers are as global and diverse as the challenges they tackle.
Penetration Testing
Penetration testing serves as a fundamental tool in identifying and fortifying against potential cyber threats. This section looks at the market size, costs, budgets, and insights into pen testing, highlighting its essential role in safeguarding digital environments.
30. The Rise of the Penetration Testing Market

Penetration testing, commonly known as pen testing, is a simulated cyber attack against a system to identify vulnerabilities that could be exploited by hackers. It's a critical component in any cybersecurity strategy, targeting everything from web applications and servers to firewalls and APIs.
Based on a comprehensive analysis of a variety of industry forecasts, the global market for penetration testing products and services is projected to surpass a staggering $5 billion annually by 2031. This robust growth underscores the increasing recognition of pen testing's role in bolstering cybersecurity defenses.
31. Average Cost of a Penetration Test

Calculating the costs of penetration testing can be complex. They average $18,300 but can start as low as a few hundred dollars and exceed $100,000. They vary widely depending on the focus and methodology.
Focus:
- Network tests focus on the vulnerabilities in a company's network infrastructure.
- Web application tests aim to find weaknesses in specific software applications.
- Organization-wide tests are comprehensive and cover multiple aspects of a company's information systems.
Methodology:
- Black box testing is done without any prior knowledge of the infrastructure to be tested, simulating an external hacking or cyber attack.
- Gray box testing is a hybrid approach in which the tester has some knowledge or partial access to the environment, offering a more focused evaluation.
- White box testing involves full disclosure in which the tester has complete access to the network or application, allowing for a thorough examination of all possible vulnerabilities.
Each of these types and methodologies comes with its own set of costs, making the "average" cost a somewhat theoretical construct that doesn't capture the full range of options available.
32. Pen Testing Budgets on the Rise

As the cybersecurity landscape evolves, so do organizational budgets to counter potential threats. A 2022 report reveals that 92% of companies are upping their general IT security spending, with 86% specifically boosting their budgets for penetration testing.
European organizations are leading the charge; while 42% of European-based respondents to the report have increased their penetration testing budgets by more than 10%, only 17% based in the United States have done so. The market for penetration testing services is on a growth trajectory too, projected to expand by nearly a quarter by 2026.
33. Penetration Testing Careers

The demand for penetration testers in the U.S. experienced a significant upswing throughout 2023, as evidenced by online job listings. The year saw 15,851 job openings in the field. In early 2024 alone, companies listed 4,800 job openings.
These roles aren't just lucrative — with an average salary of $120,662 — but also diverse in terms of job titles. Positions range from Penetration Testers and Vulnerability Analysts to Information Security Analysts and Cloud Security Engineers.
When it comes to skills, employers are primarily looking for expertise in Computer Science, Vulnerability Assessment, Cyber Security, Python programming, and (of course) Penetration Testing. As for educational qualifications, a Bachelor's Degree is the most commonly requested, making up 69% of the job listings.
34. Why Companies Invest in Penetration Testing
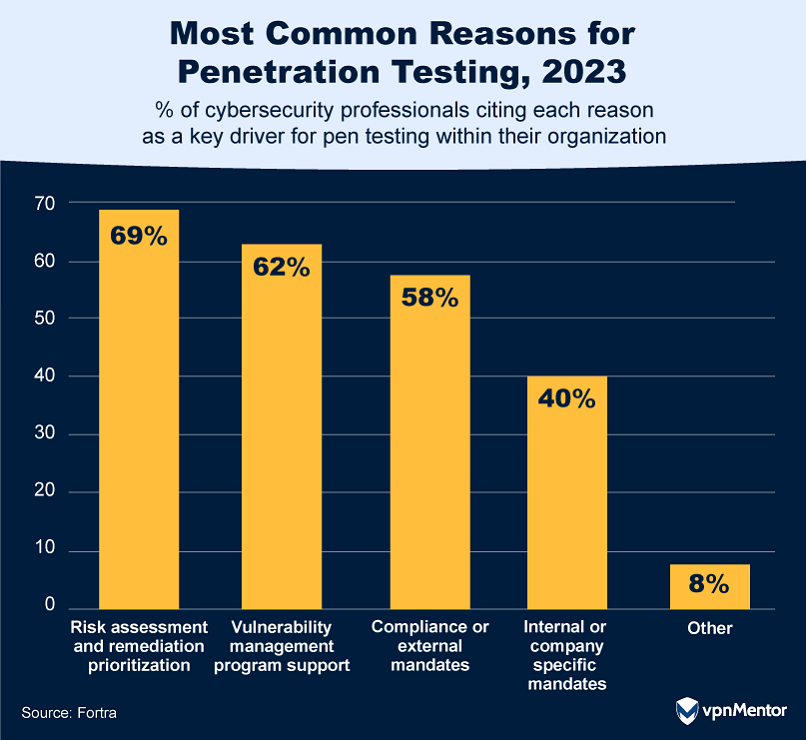
Organizations engage in penetration testing for a variety of critical reasons. The majority, at 69%, conduct these tests primarily for risk assessment and remediation prioritization, helping them identify and focus on the most potentially harmful security weaknesses. Following closely, 62% use pen testing to support their vulnerability management programs, a structured approach to identifying and mitigating IT vulnerabilities.
Compliance is another significant driver, with 58% conducting pen tests to meet external mandates set by regulatory bodies and government agencies, and 40% for internal or company-specific mandates. While external mandates often take precedence due to legal implications, internal mandates are tailored to an organization's unique needs and often exceed the requirements set by external bodies.
35. Navigating the Challenges of Pen Testing
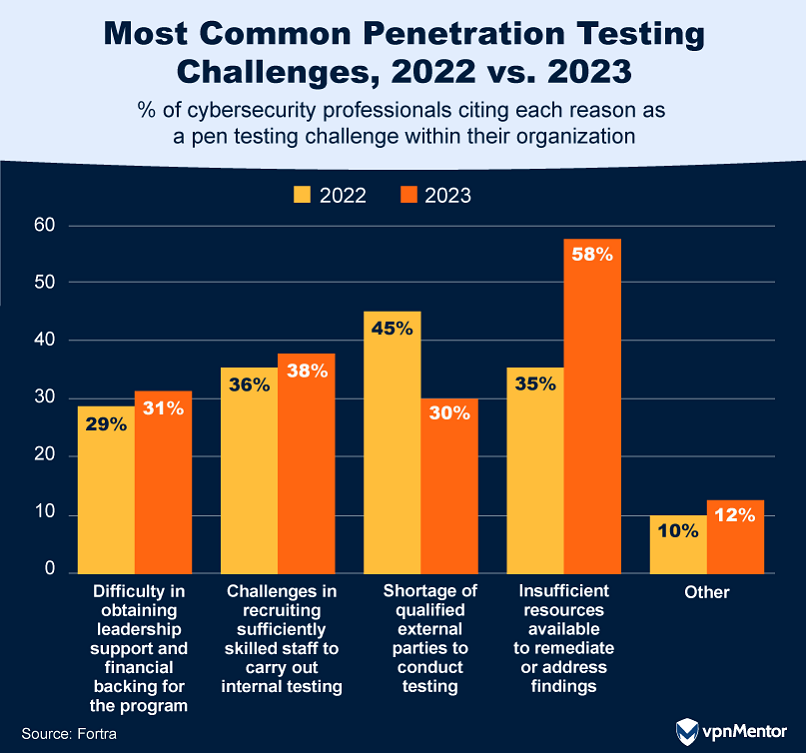
Navigating the ever-evolving landscape of penetration testing comes with its own set of challenges for organizations and, according to a 2023 report by Fortra, there have been some significant shifts over the past two years.
First, finding qualified experts to do the testing is getting easier, with 15% fewer organizations reporting this as a challenge compared to the previous year. On the other hand, more organizations are finding it tough to act on the issues that testing uncovers, with a 23% increase in this challenge from the previous year.
Finally, confidence in security measures has dropped by 15%. While that might sound bad, it could actually be a good thing — overconfidence can lead to complacency, and in cybersecurity, staying alert and ready to adapt is crucial.
36. How Often Companies Really Pen Test
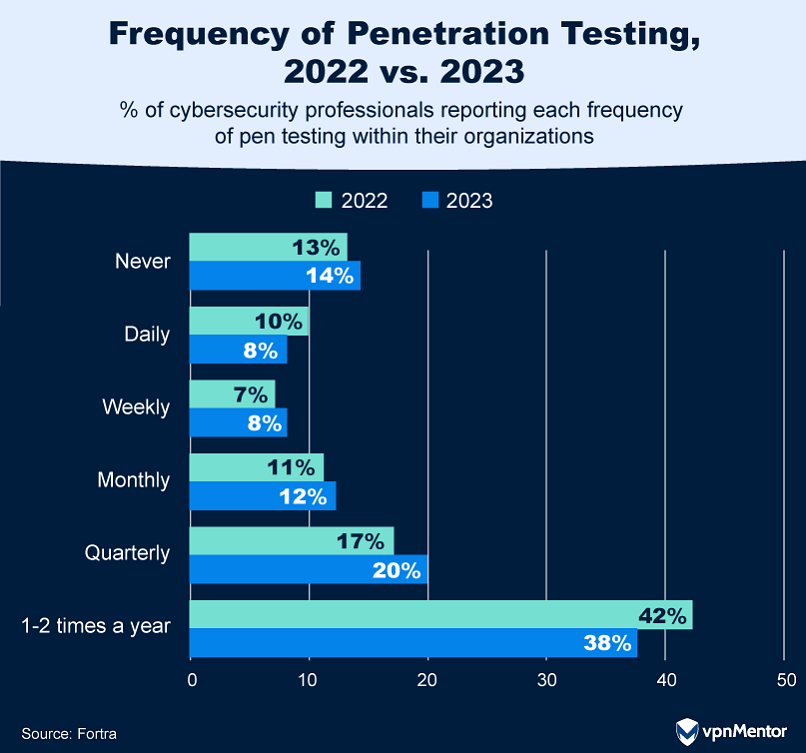
The frequency of penetration testing among organizations reveals some interesting trends. Most organizations conduct pen tests only once or twice per year. While that's better than not doing any tests at all, it may not be enough to ensure that past security issues have been fixed properly. Some companies say they run these tests every day, but they're likely doing simpler, automated checks instead of the more thorough tests that are really needed.
Companies that test monthly or every three months seem to have found a good middle ground. They're doing enough tests to stay safe but not so many that it becomes a burden. The key takeaway? How often a company should run these security tests depends on many factors, including time, money, and personnel, as well as the kind of data the company needs to protect.
37. Trends in In-House Penetration Testing
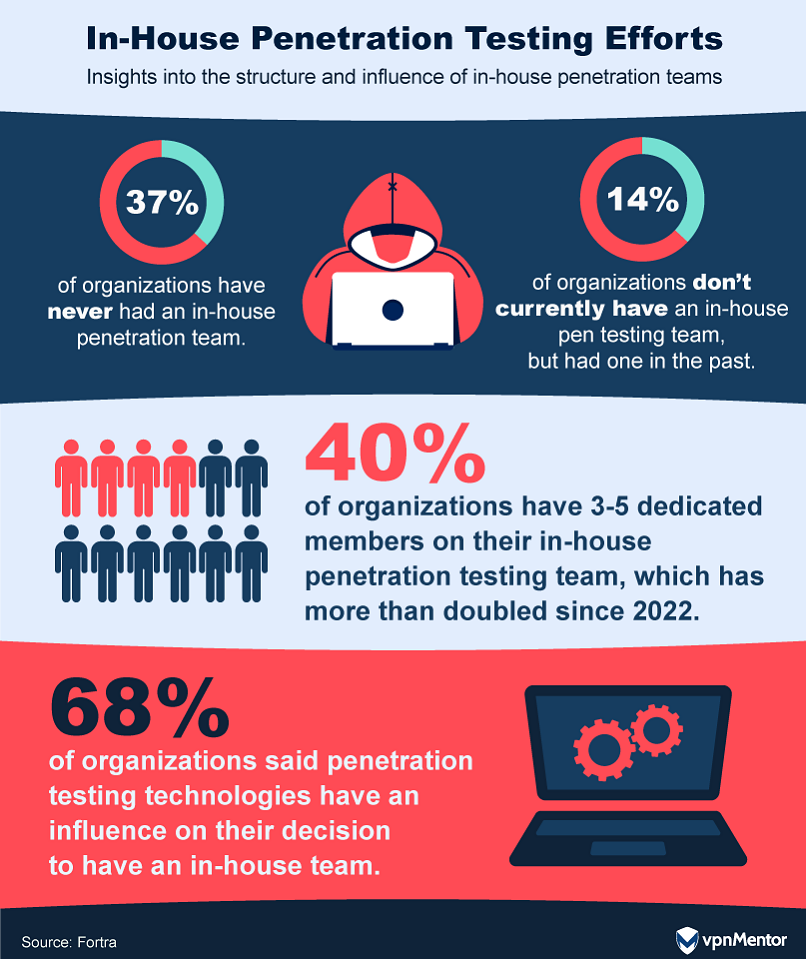
In-house penetration testing teams offer the advantage of more frequent and comprehensive assessments of an organization's IT infrastructure. According to a 2023 report, the number of organizations with internal pen testing teams has increased by 7%.
Despite these gains, many organizations still lack an internal pen testing team, citing reasons like insufficient need (48%), talent scarcity (36%), and budget constraints (28%). Interestingly, there's a 12% drop in organizations claiming they don't need a full-time pen testing team, possibly indicating growing awareness of the value of in-house expertise.
38. Why Organizations Opt for Third-Party Pen Testers
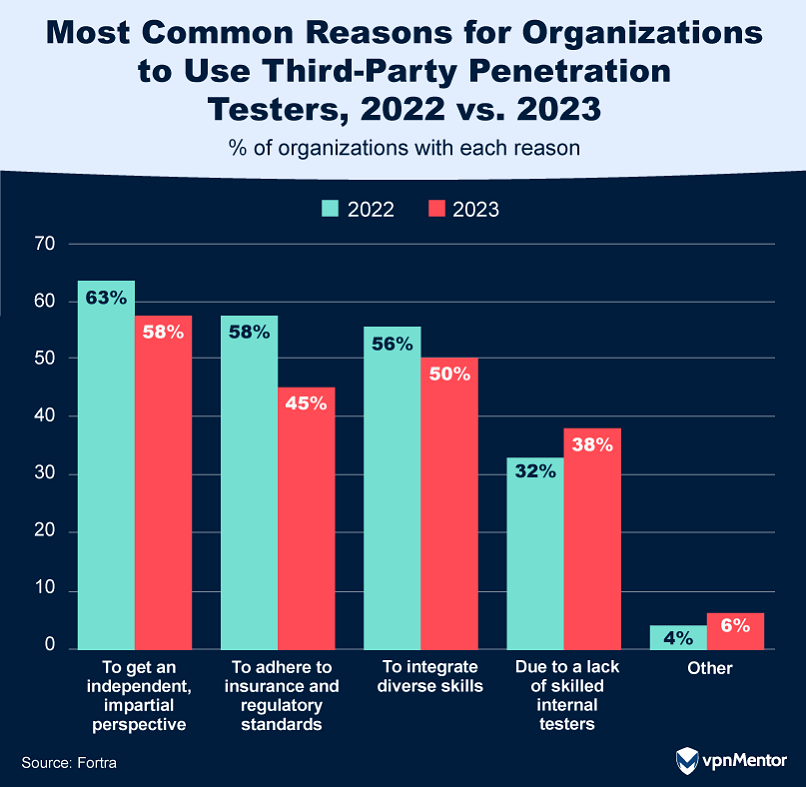
Most organizations — 78% to be exact — still use outside experts for penetration testing to check their security. But there's a growing trend to also do this testing with in-house teams. The best approach seems to be a mix of both. Why? External teams offer a fresh, unbiased look at security, which is the top reason companies hire them. They also bring specialized skills to the table.
Interestingly, fewer companies are using these third-party services just to meet compliance rules, possibly because they're handling those requirements themselves. While these external teams are often used to test network and software security, they're also uniquely qualified to test physical security measures like door locks and surveillance cameras.
39. International Regulations on Penetration Testing
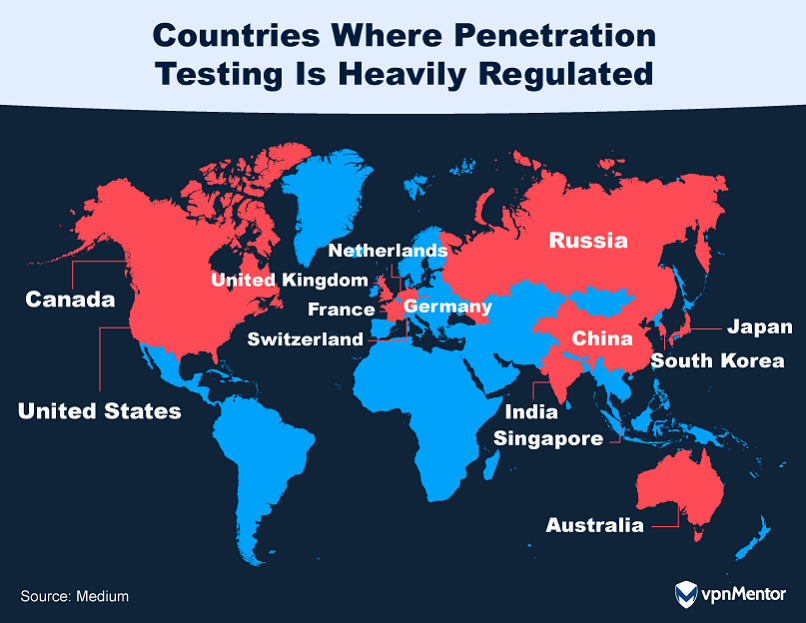
The legal landscape for penetration testing can be complex, as regulations vary significantly from country to country. For instance, Germany requires explicit permission under its Criminal Code and Federal Data Protection Act, while the UK's Computer Misuse Act of 1990 sets clear boundaries on unauthorized access.
In the United States, the Computer Fraud and Abuse Act and the Electronic Communications Privacy Act both have provisions that could make unauthorized penetration testing illegal. Countries like India, Singapore, and Australia also have stringent regulations requiring prior authorization. Even in countries like China and Russia, where cybersecurity is state-controlled, explicit permissions and licenses are mandatory.
Bug Bounties
Bug bounties offer ethical hackers a compelling incentive for uncovering digital vulnerabilities. In this section, we chart the trajectory of the bug bounty landscape, examining market forecasts, bounty averages, and notable payouts from leading tech giants.
40. Bug Bounty Market Forecast
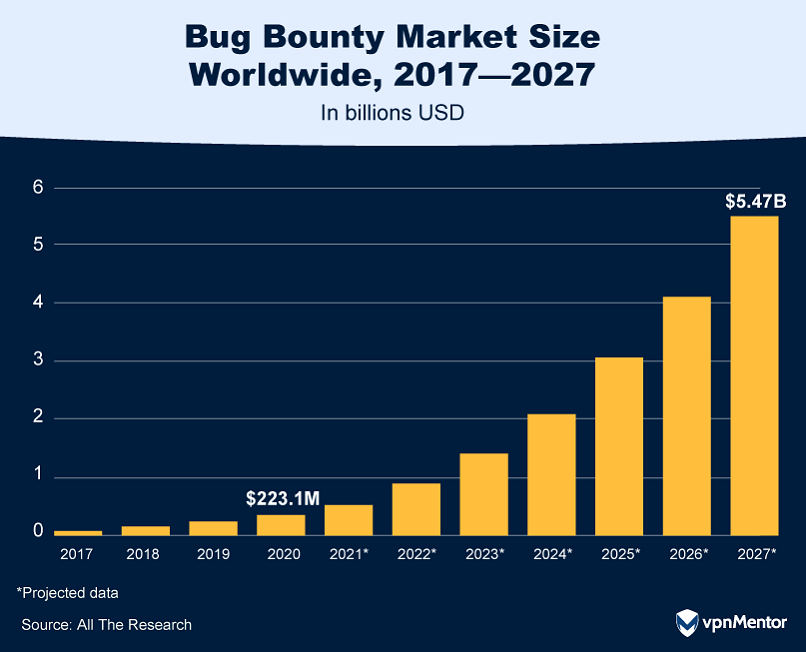
The global bug bounty market is experiencing explosive growth, from a valuation of $223.1 million in 2020 to a projected $5.465 billion by 2027, with a CAGR of 54.4%.
For those unfamiliar, a bug bounty is essentially a cash reward offered to developers who identify critical vulnerabilities in software, effectively crowdsourcing a system’s flaw detection. These bounties are often facilitated through specialized platforms designed to manage such programs.
As the tech landscape has evolved, so has the market for bug bounty platforms, with newer technologies gaining prominence over older ones. Amid a sluggish global economy, consumer price sensitivity could also play a role in shaping this burgeoning market.
41. Which Industries Have the Highest Bounty Payouts?
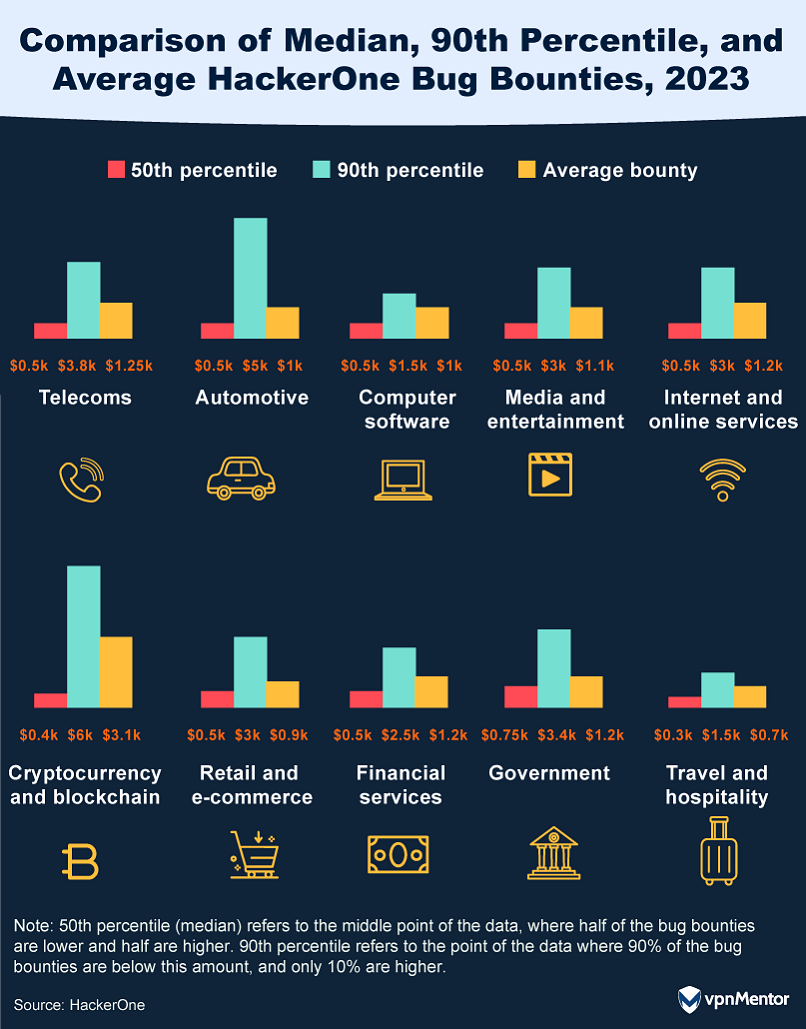
The bounty landscape in 2023 presents an intriguing picture of industry acknowledgment, with ethical hackers seeing a significant rise in potential earnings. The median bounty on the HackerOne platform increased to $500 from $400 the previous year, and the highest rewards, in the 90th percentile, climbed from $2,500 to $3,000.
The automotive sector saw a notable surge, with its highest rewards jumping to $5,000, underscoring the industry's increasing focus on digital protection. Cryptocurrency and blockchain continue to offer some of the most lucrative rewards, with an average payout of $6,000 — a figure that jumps to over $100,000 for high and critical vulnerabilities.
42. Why Hackers Spend More Time Bug Bounty Hunting

The pandemic's social distancing rules and temporary job retention schemes led to an unexpected surge in the practice of ethical hacking as a hobby. According to a 2022 survey by Intigriti, 59% of respondents spent more time bug bounty hunting compared to before the pandemic began. This newfound interest wasn't limited to the pandemic; the hobby has stuck.
When asked about their motivation for dedicating more time to bug bounty hunting, 74% cited a desire to increase their skills, while just over half (53%) were driven by financial incentives. This trend highlights how ethical hacking was not only a productive way to use free time in the pandemic, but also became a means to enhance professional skills and financial prospects.
43. Meta’s Bug Bounty Breakdown
Since its inception in 2011, Meta's bug bounty program has been a cornerstone in bolstering the company's cybersecurity measures. With a whopping $16 million paid out in bug bounties between 2011-2022, the program has processed more than 170,000 reports. Of these, over 8,500 were deemed significant enough to warrant a bounty.
In 2022 alone, Meta awarded more than $2 million to researchers hailing from 45 different countries. The company saw around 10,000 reports, with bounties issued on more than 750 of them. The leading countries in terms of bounties awarded in 2022 were India, Nepal, and Tunisia.
As Meta continues to expand into virtual and mixed reality technologies, the bug bounty program is expected to remain a critical part of its cybersecurity strategy, with new payout guidelines offering bounty amounts as high as $300,000.
44. How Google Spent $12 Million on Bug Bounties in 2023
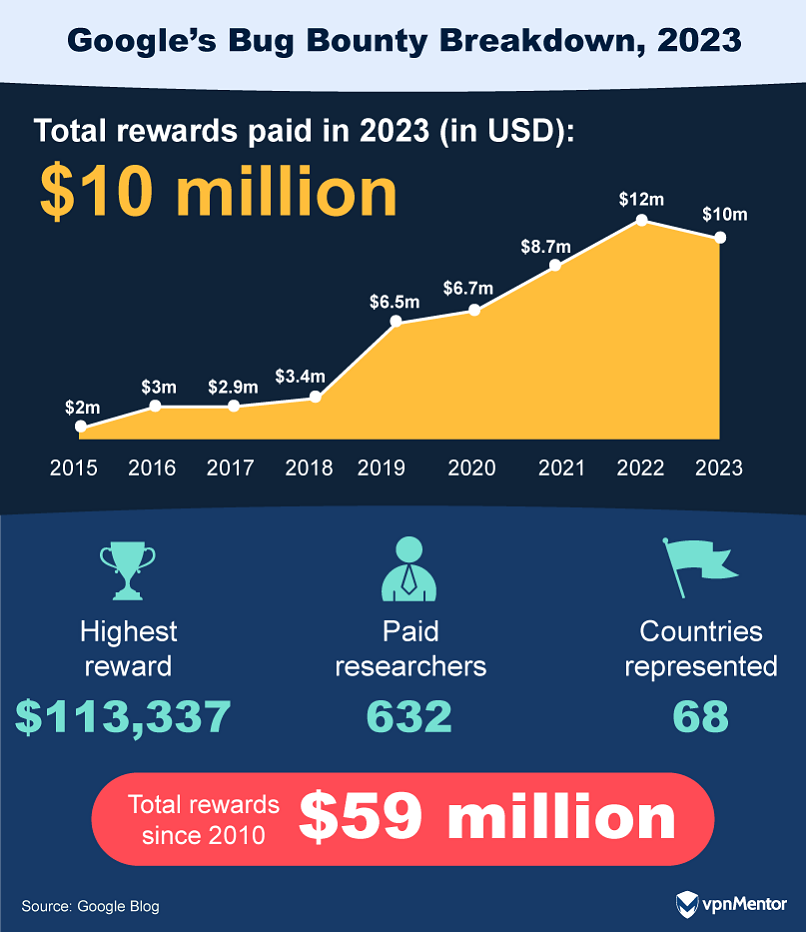
Google shelled out a whopping $10 million in bug bounty rewards in 2023, a slight decrease from the $12 million paid in 2022. The Android ecosystem alone accounted for $3.4 million of these rewards.
The inclusion of Wear OS in the VRP incentivized further research into wearable technology. The ESCAL8 conference hosted a live hacking event, where over 20 critical vulnerabilities were uncovered in Wear OS and Android Automotive OS, leading to $70,000 in rewards. Additionally, the hardwear.io security conferences lead to the discovery of over 50 vulnerabilities in Nest, Fitbit, and Wearables.
Chrome's VRP wasn't far behind, with $2.14 million in payouts for roughly 359 valid security bug reports. 2023 also saw a focus on Generative AI security, with the bugSWAT live-hacking event leading to significant findings and refining security criteria for AI products in line with Google's AI commitments.
Safeguarding Today’s Digital Landscape for a Safer Tomorrow
The landscape of ethical hacking has undergone a remarkable evolution. In the early days, hacking was often synonymous with cybercrime, but the last two decades have witnessed a significant shift.
Today, ethical hackers are recognized and even celebrated for their critical role in safeguarding digital infrastructures. Their diverse backgrounds and skills have proven invaluable in navigating the complexities of cybersecurity, with their efforts saving industries billions of dollars and driving advancements in the field.
As we look to the future, the ethical hacking community will continue to expand as it adapts to new challenges and technologies. In this dynamic digital age, ethical hackers stand as vital guardians, their expertise and dedication shaping a safer online world for all.
Glossary of Terms
| Attack Surfaces | The points in a computer system, a network, or software where unauthorized users might try to enter or extract information. |
|---|---|
| Blockchain | A digital system records transactions across many computers, similar to a chain of digital "blocks" containing records. Every transaction is verified and added to a collective ledger, making it secure and hard to alter. |
| Bug Bounties | Financial rewards are offered to hackers who identify and report software vulnerabilities. |
| Cloud Platforms | Computing services and infrastructure hosted over the internet, often involving data storage, servers, databases, networking, and software. |
| Cryptocurrency | Digital or virtual currency that uses cryptography for security, like Bitcoin and Ethereum. Unlike traditional currencies, it operates independently of a central bank and uses decentralized systems for secure financial transactions. |
| Cross Site Scripting (XSS) | A web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. |
| DeFi (Decentralized Finance) | Financial services operate online using blockchain, without traditional banks, where financial transactions are done directly between people, securely and openly. |
| Generative AI (GenAI) | Advanced AI technologies, like generative pre-trained transformers (GPTs), can create content (text, images, music, etc.) based on data it’s been trained on. |
| Improper Authentication | A security flaw in which a system incorrectly verifies the identity of a user, allowing unauthorized access. |
| Improper Authorization | A security issue in which a system incorrectly grants access rights to users. |
| Penetration Testing | A simulated cyber attack against computer systems to identify vulnerabilities. |
| Reconnaissance | The initial phase of an attack in which hackers gather information about a target system to find weak points. This can involve collecting publicly available information or using tools to scan systems for vulnerabilities. |
| Social Engineering Attacks | Techniques that manipulate users into revealing confidential information or performing certain actions, such as typing their password into the wrong website or clicking a link that contains malicious code. |
| Vulnerability Management Programs | Structured approaches to identifying, classifying, and addressing IT vulnerabilities. |
| Vulnerability Scanning | The use of automated software to scan a system for known vulnerabilities. |
| Web Application Testing | The process of testing web applications for security vulnerabilities. |




Please, comment on how to improve this article. Your feedback matters!