Android's Online Privacy Guide: How to Protect Your Privacy Online in 2026
- What Are the Biggest Threats to Your Online Privacy and Data Security?
- Government Intelligence
- Browser and Website Data Sharing
- Search Engines
- Non-Secure Websites
- Malware
- Cloud Storage
- What Steps Can You Take to Protect Your Online Privacy?
- Use a VPN for Enhanced Online Privacy and Security
- Boost Your Online Anonymity Using the Tor Network
- Create Secure Passwords and Enable Two-factor Authentication
- Use Secure Payment Methods for Identity Theft Protection
- Optimize Browser Settings for Safe Browsing and Online Privacy
- Change Your Search Engine for Better Online Anonymity
- Secure Your Cloud Storage to Protect Data
- Protect Personal Information by Securing Your Email
- Improve Cybersecurity with Anti-Malware and Firewall Software
- Manage Your Digital Footprint by Staying Informed on Social Media Privacy Policies and Settings
- Only Download Trusted Apps and Regularly Review Permissions to Ensure Data Security
- VPNs Help Safeguard Your Online Privacy
It's time to do something about the risks you face every time you use an Android phone or tablet. Protecting your privacy doesn't have to be complicated. I'll help you identify issues and find solutions to protect yourself. Share
Since the Edward Snowden leaks revealed the extent to which government bodies can monitor and gather data on users all over the world, learning how to protect your privacy online is more important than ever. But with all of the different threats out there, you may struggle to figure out where to even start.
Maybe your social media account was hacked. Maybe you're sick of those disturbingly specific online ads following you wherever you go. Maybe you just decided to finally face the fact that your online privacy may be at risk.
Whatever your reason, protecting your privacy online can seem like an overwhelming task.
The good news is that protecting your privacy doesn’t have to be complicated. In this online privacy guide, I'm going to cover the biggest threats to your online privacy when using an Android device and provide you with simple steps you can take to safeguard your personal information.
What Are the Biggest Threats to Your Online Privacy and Data Security?
 An infographic with information on the biggest threats to online privacy.
An infographic with information on the biggest threats to online privacy.
1. Government Intelligence
One of the biggest threats to internet privacy is the far-reaching 14-Eyes Alliance.
The Edward Snowden leaks paint a worrying picture of widespread international intelligence-sharing agreements that allow governments to bypass their own privacy protection laws. We now have a better understanding of how easily many government bodies can gather information on their citizens.
Data that passes through one of the countries in the 14-Eyes Alliance can no longer be assumed to be private. This is one reason that many people rely on online privacy guides to learn how to protect their privacy online and encrypt their data.
But considering the fact that government bodies like the NSA have played a role in creating some of the most popular encryption algorithms, does encrypting your data really keep it secure? To answer this question, let’s go over the basics of how encryption works.
How Does Data Encryption Protect Your Online Privacy?
At its most basic level, encryption is a math equation combined with a secret password or key.
The mathematical algorithm used to turn plain data into an encrypted message is called a cipher. The algorithm works by using a unique key known only by the sender and receiver.
For example, imagine that you send the number 2387 to your friend. You tell him that all you did was multiply two numbers together to get 2387. In other words, he knows that you used the following cipher:
X * Y = Encrypted number
Using only the cipher and the encrypted number, will he be able to figure out the two numbers you used? He could find every combination of numbers that 2387 is divisible by, but he still couldn’t be sure which two numbers were the ones you originally used.
In this scenario, your friend is missing the key you used with your cipher. But what if you and your friend agreed that in this equation, Y = 7? Now your friend knows that:
X * 7 = 2387
He should now have no trouble figuring out that the other number is 341.
This is a simplified example, but the important piece to understand is that the cipher is only one piece of the encryption puzzle. Modern encryption algorithms are so complex that they're essentially unbreakable without knowledge of the unique key used.
Does Encryption Protect Your Data from Government Surveillance?
Modern encryption methods will keep your data secure even from government bodies. However, encrypted data can attract government attention that may be unwanted.
One downside of encryption is that it stands out to government intelligence organizations. According to leaked NSA documents, most data collected is deleted after a maximum of five years. However, the NSA reserves the right to collect and keep encrypted data for as long as it takes to decode the information. This applies to both foreign and domestic data.
On the other hand, modern ciphers are so sophisticated that it may not matter whether or not the NSA has your encrypted information. I'll go into encryption methods in more detail when I discuss steps you can take to protect your online privacy.
2. Browser and Website Data Sharing
Fingerprints, trackers, cookies... it seems the list never ends. Mobile web browsers routinely collect and retain information about your internet connection and online activity. Some of this information is reported to websites to help them load faster and format correctly, but there are other factors at play.
Browser Fingerprinting
Your mobile browser may be handing out much more information than you think. You can visit sites like Webkay and Cover Your Tracks (formerly Panopticlick) to test out the kinds of information your browser makes available to the websites you visit.
 An infographic with information on the variety of data your web browser may share with other parties.
An infographic with information on the variety of data your web browser may share with other parties.
Even though a lot of this information doesn’t mean much by itself, the combination of this data can give your browser a unique fingerprint that compromises your online privacy and allows websites to identify you.
Similar to how the unique lines and dips of a human fingerprint can be matched to a single individual, the small pieces of information that servers can gather about your browser and device can be used to identify you as a unique user.
For example, your browser may be the only one on Australian Eastern Daylight Time with the same set of browser plugins, cookie settings, and display resolution. A site can use this knowledge to keep track of your browsing habits, even if you’ve taken steps to limit tracking such as clearing your cookies.
Third-party analytics can even track your online activity across different websites.
The scariest thing about browser fingerprinting is that when you change your default browser settings to improve privacy, such as by turning off HTML5 web storage or blocking cookies, you may actually make your browser fingerprint more unique and easier to identify.
One positive use for browser fingerprinting is identity theft and fraud prevention.
Have you ever gotten an alert from your bank after logging in to your account from a new location or device? Your bank’s website noticed that the person logging in didn’t have your usual browser fingerprint, and they took steps to make sure your account hadn’t been hacked.
On the other hand, advertisers love to take advantage of browser fingerprinting. The more information they're able to gather about your mobile browsing habits, the better they're able to create targeted ads for you.
Cookies
In addition to giving out information, your mobile web browser also stores information from the websites you visit in the form of HTTP cookies.
Cookies are small files that websites store on your device. The purpose of cookies is to create a customized browsing experience and decrease loading times.
For example, a shopping website may store HTTP cookies on your browser to keep track of what items you placed in your shopping cart so they'll load automatically the next time you visit the website.
Partners of the website, such as advertisers or analytics companies, are also able to place third-party cookies on your browser. Once stored on your web browser, cookies can do things like monitor your internet behavior or display targeted ads, potentially compromising your privacy online.
Security-conscious users should be aware of two unique kinds of cookies: Flash cookies and HTML5 web storage.
Similar to regular HTTP cookies, Flash cookies are small files stored on devices that use Flash. They contain information about your experience with the Flash elements on the website, impacting your data privacy.
On PCs, Flash cookies aren't stored in the same location as regular cookies, but are instead stored in a separate Adobe file. This means they aren’t deleted automatically when you clear your cookies.
Instead, they must be deleted using your Adobe Flash player settings. Sometimes undeleted Flash cookies can even respawn HTTP cookies after you delete them, making it easier for websites and third parties to track you.
If you're using Android version 4.1 (Jelly Bean) or higher, you don't have to worry about Flash cookies, as Flash is no longer supported. However, if you're using an older device, you may still have Flash installed. You'll want to uninstall it or go into Flash Player settings and opt to never have Flash cookies saved.
HTML5 web storage behaves similarly to traditional cookies, but the data is stored on your browser rather than your device. While this can enhance your online privacy settings, you still have the option to turn off web storage in your browser settings.
ETags
Entity tags (ETags) are a method that web servers use to validate web caches, and they play a role in both internet security measures and potential online privacy concerns. When you visit a website, your browser saves certain data to your device so the browser doesn’t have to reload it again.
For example, your browser may save a copy of large images on a website homepage so you don’t waste time and bandwidth loading them again next time you visit. This saved data is called a web cache.
ETags are a kind of HTTP header. When they're included in a website, they assign a unique value to each cache element to help the website figure out whether any cached files need to be redownloaded each time you visit the site.
The downside of ETags is that they're unique identifiers assigned to cache resources, so they can be used to track you. They're also very hard to detect and avoid because they're included as part of the website’s HTTP response header, threatening your online anonymity and digital privacy.
3. Search Engines
Think of how often you and the people around you use Google. No wonder Google and many other search engines are able to collect so much information about us, impacting our online privacy. Some basic information that search engines store about you includes:
- Your IP address
- The time and date you visited
- Search terms you used
- A unique identifier that may be stored in cookies called a Cookie ID
This data is passed along to web pages and advertisers, who can then use the information to personalize your experience and create targeted ads. This explains why you started seeing ads for cat food everywhere you went online right after you visited that pet adoption site.
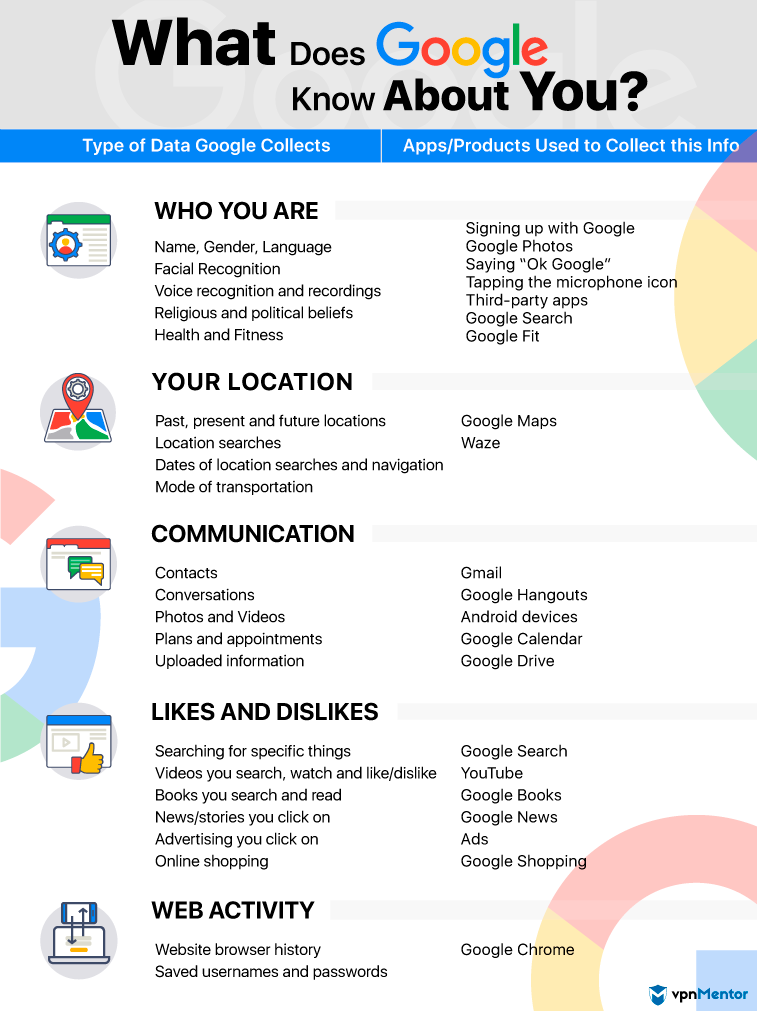
Even worse, most search engines are required to hand over the information they've collected if it's requested by a court or government agency. Considering the intimate role search engines play in many of our lives, this is alarming in terms of privacy protection.
Think about what this means for you. How often have you searched for something out of curiosity without thinking about possible ramifications? Are these searches things you would be willing to disclose to the world? Do you think your online searches should be used as evidence of your behavior or personality? This raises significant concerns about how to protect your privacy online.
It seems silly to think that you could find yourself explaining to a jury that you only searched “how to get rid of a body” because you were watching Breaking Bad, not because you were planning to murder your neighbor.
However, there have been real cases where search histories have been used in legal situations. In a 2023 arson case, the Colorado Supreme Court issued a keyword search warrant to help identify suspects. In states with strict anti-abortion laws, prosecutors have sometimes subpoenaed search data to gather evidence about women suspected of having an abortion.
4. Non-Secure Websites
Secure websites use the HTTPS encryption protocol to protect any data exchanged between you and the secure server.
HTTPS stands for HTTP Secure and is also known as HTTP over TLS (Transport Layer Security). You may also see it referred to HTTP over SSL (Secure Sockets Layer), which is the predecessor TLS.
Luckily, the encryption protocol used by HTTPS is very secure, and the majority of websites you visit will be using it. You can easily check whether a website is protected by HTTPS just by looking at the beginning of the URL. Many web browsers will also notify you if you are visiting a non-secure server.
For example, this is what Google Chrome for Android displays when you visit a secure website:
And this is what is displayed when you visit a non-secure website:

Watch out for non-secure HTTP websites. Your internet service provider (ISP) or any third-party spying on you, can view any information you exchange with a non-secure website.
This means anything you write or submit to the website can be easily stolen, including sensitive information like your social security number or credit card information. Protecting your online privacy is crucial in these situations to avoid potential data breaches and identity theft.
5. Malware
Malware is any kind of malicious software intended to damage or spy on your device, server, or network in some way. Many types of malware can harm your Android device or steal your info. Viruses, worms, ransomware, adware, and spyware are some of the most common.
One of the scariest things malware can do to threaten your privacy online is to create a backdoor that allows third parties to bypass the security features protecting your software.
A backdoor installed by malware could give cybercriminals access to your device system, allowing them to steal your personal data, modify your files, or even control your device remotely.
Malware can be very difficult to detect. A trojan horse, for example, is malware that pretends to be trustworthy in order to trick you into installing it or providing it with sensitive data. You may think you're downloading or opening a trusted app, so when the hidden malware asks for your master password, security question, or financial information, you don’t think twice.
Software with a legitimate purpose, knowingly downloaded by the user, can also contain privacy-invading features the user isn’t aware of. This kind of software is sometimes known as grayware, and it poses a serious risk to digital privacy.
A real-life example of this occurred when a group of popular Mac apps was caught stealing and sharing users’ private browsing history without their knowledge or consent.
6. Cloud Storage
Even if your cloud storage service encrypts your data, your privacy online isn’t guaranteed. Since the company encrypts your data, it also holds the key to unencrypting it.
If you look closely at the terms and conditions, most popular cloud storage service providers explicitly reserve the right to share your files and data with authorities if they receive a court order. Many of them have also been known to cooperate with the NSA.
If the NSA has the ability to access it, your data is no longer truly private.
What Steps Can You Take to Protect Your Online Privacy?
Many people put a lot of time and effort into beefing up the security measures on their computers but forget to think about mobile devices. This is a big mistake that can leave a lot of your most sensitive information vulnerable, jeopardizing your online privacy.
Ask yourself, in how many of the following ways do you regularly share information or data about yourself with your phone or tablet:
- Texting
- Making phone calls
- Making voice calls using Voice over Internet Protocol (VoIP)
- Searching with Google or other search engines
- Loading websites
- Sending and receiving email
- Posting on social media accounts like Facebook, Twitter, Instagram, and Snapchat
- Storing photos, files, apps, and other data using Dropbox, Google Cloud Storage, Microsoft’s OneDrive, or Amazon Drive
- Mobile banking or payment methods
Most of us share a lot of sensitive information with our mobile devices on a daily basis. Including these devices in our privacy protection efforts is now more important than ever.
You might be feeling overwhelmed after reading about some of the biggest threats to your online privacy. Take a deep breath.
There are lots of things you can do to protect your privacy online, and the best part is that many of them are simple.

1. Use a VPN for Enhanced Online Privacy and Security
If you're looking for one simple step you can take to get comprehensive online privacy protection, the single best thing you can do is invest in a high-quality VPN.
Many of the premium VPNs you trust for your PC or laptop can also be used on Android devices, including mobile phones and tablets.
VPNs are easy to set up, but they can provide you with some of the most comprehensive protection online from the scariest threats to your online privacy.
Some of the steps you can take to protect your online privacy are intended to correct damage after the fact. A VPN, on the other hand, will protect your internet connection to stop privacy breaches before they happen. Preventing a security problem is much easier than fixing one.
A VPN can combine multiple layers and methods of protection to ensure that your connection is secure, anonymous, and private. Here are a few of the major privacy protection features that most VPN services offer.
Encryption
There are two main pieces to consider when it comes to encryption strength. The first piece is the cipher, otherwise known as the mathematical algorithm used to encrypt the data. The most popular and secure cipher out there at the moment is AES. This is the cipher that the US government uses to encrypt its data.
The second piece to consider is the encryption key length. The two most common encryption key lengths you're likely to see with AES encryption are 128-bit and 256-bit encryption, with most reputable VPNs offering 256-bit.
Data is encrypted and decrypted using a unique key. The only way third parties can read your encrypted data without that unique key is by randomly trying every possible combination. This is called brute force.
An 8-bit encryption key has only 256 possible combinations, so brute force is likely to be successful. Now consider how many combinations are possible with a 128-bit key and then further with a 256-bit key.
Where technology is at the moment, even using the most advanced supercomputer in the world, cracking 128-bit encryption with brute force would take billions of years, and cracking 256-bit encryption would take an inconceivable number of years.
OpenVPN
OpenVPN is open-source software that offers a secure protocol used by many VPN providers. OpenVPN essentially routes your VPN connection through the secure channels it creates to protect you from data leaks. It provides a very secure layer of privacy protection.
Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) is an extremely valuable method of encryption for those concerned about how to protect your privacy online. With a typical encryption tool, your data is secured using a single encryption key. If that key were to be compromised, your data would no longer be secure.
PFS instead encrypts your data using temporary and constantly changing encryption keys. This significantly increases your security, because even if one key were to be compromised, at worst it would only reveal a small piece of information. The rest of your data would remain secure.
Escape 14-Eyes Alliance Spies
Some worry that although VPNs offer some of the best online privacy protection out there, they don’t truly allow you to be anonymous. This is because the VPN provider could be compelled to hand over your information to authorities.
That’s why many of the best VPN providers have a strict no-logs policy and operate entirely outside the jurisdiction of countries in the 14-eyes alliance. In these cases, not only does a VPN provider not retain any of your data, but it also cannot be obligated to provide data it might have to government agencies.
These are only a few of the benefits and privacy protocols that VPNs have to offer. Many VPN services allow you to easily personalize your protection configuration to address your specific privacy concerns.
You can also easily combine VPN security with any of the other methods in this online privacy guide to create a comprehensive privacy protection strategy.
2. Boost Your Online Anonymity Using the Tor Network
One of the most popular methods of getting online securely and anonymously on a computer is to use the Tor network. Now, this option is available for Android users, too.
Tor stands for The Onion Router, which is a nod to the software’s origins as a US naval research project called The Onion Routing program.
Compared to a VPN, using the Tor network has both advantages and disadvantages.
If you're connected correctly to the Tor network, you're completely anonymous. None of your online activity or data can be traced back to you.
Tor encrypts all your data, including your IP address, several times before directing your connection through a random series of nodes or relays. The nodes are run by volunteers who themselves have no way of detecting any of your data or the path your connection is headed to because a layer of encryption is removed each time you reach the next node.
This process of creating multiple layers of encryption and then removing one layer at each node is where the name The Onion Router comes from.
To connect to Tor on Android, you need to use its Orbot package. This allows you to access instant message services, email, and the web without your ISP or others snooping. Your connection is completely anonymous to the websites you visit.
3. Create Secure Passwords and Enable Two-factor Authentication
Creating and maintaining secure passwords is one of the simplest yet most effective ways to protect your online privacy. For Android users, this includes creating and using a master password that locks your phone, tablet, or other mobile device.
I know you’ve probably been told a million times before that reusing passwords for multiple accounts is a bad idea, but it’s worth repeating. According to a 2018 Psychology of Passwords survey, the majority of people reuse the same password for multiple accounts.
vpnMentor offers a digital privacy tool to help you generate highly secure passwords.
Here's a quick list of general dos and don’ts for secure password habits:
 Do:
Do:
- Use multifactor authentication, otherwise known as two-factor authentication. It's extremely effective and doesn’t take much work.
- Change your passwords regularly, particularly when there may have been a data breach.
- Create long passwords. Length is even more important than complexity. Passwords become exponentially more difficult to crack with each additional character that is added.
- Create a master password for your device. While a PIN is one option, an alpha-numeric password offers more security.
Don’t:
- Use the same password for multiple accounts.
- Create passwords using easily available information like your birthday or pet’s name.
- Use simple or obvious terms, such as "password" or "12345."
- Rely on easy-to-guess password recovery security questions.
Note: Signing in with your fingerprint on a touchscreen is a popular option due to its speed and convenience. However, until recently, the law was murky when it came to whether law enforcement could compel you to unlock your device using your fingerprint. A recent federal ruling says the act is unconstitutional, but there's a possibility it may be overruled.
Legalities aside, fingerprint technology can be faulty. Reports have surfaced of some Samsung Galaxy devices allowing any fingerprint to unlock a device. To ensure your device and personal information stay secure, choose a PIN or alpha-numeric password that can't be easily compromised.
If you're relying on the same password for all your accounts because you're afraid of forgetting new ones, consider using a secure password manager. LastPass and Dashlane are some reliable examples.
Password managers are apps that keep track of all your passwords in an encrypted database and fill them in automatically when you need them. If you're using a computer, you can also find them as browser extensions.
Many mobile browsers, including Chrome and Firefox, offer built-in password managers. While these password managers do securely encrypt your passwords, they may be more vulnerable to security risks than third-party password managers.
Recent cybersecurity research has suggested that the auto-fill feature used by Chrome and other browser password managers may not be totally secure. For now, sticking with a secure third-party password manager may be best.
4. Use Secure Payment Methods for Identity Theft Protection
We all love online shopping, but you can leave yourself vulnerable to credit card and identity theft if you aren’t using secure payment methods. While you should only provide payment information to secure websites, that by itself can’t guarantee your data protection.
Taking measures to secure your connection before you pay, such as using a VPN, is a good first step toward protecting your privacy online. If you want to be extra careful, or if keeping your payment anonymous is important, the best choice is to use cryptocurrency like Bitcoin.
Bitcoins are easy to purchase and use. You can also purchase Bitcoins anonymously if you don’t want any link to your credit card information, such as by using a prepaid credit card or buying locally with cash.
Some banks offer extra levels of security for online shopping. For example, Bank of America generates temporary credit card numbers (known as virtual travel cards) to help customers keep their real credit card numbers secure. Citi gives virtual account numbers to disguise users' real data, also helping protect their data online. France's Societe Generale takes cryptosecurity one step further by offering users CVV numbers that update periodically.
PayPal is another option for protecting online payment. Although PayPal isn’t anonymous, the company has strong security measures in place and is committed to finding and strengthening any weaknesses in the service. They even have a Bug Bounty Program that offers financial rewards to anyone who can discover and report any site vulnerabilities.
5. Optimize Browser Settings for Safe Browsing and Online Privacy
Internet browsers routinely gather and hand out information on their users in a number of ways.
Even if you’re committed to your current web browser, you can take steps to limit the data you allow to be stored and made available to the websites you visit.
Regularly clearing your DNS cache and cookies can limit your risk of being fingerprinted and tracked through your browser. Look for a guide online for your specific browser and Android device. Many browsers also have options that allow you to limit the cookies that you accept.
The downside of constantly clearing your cache or turning it off altogether is that it can have a big impact on your loading times and overall browsing experience.
Taking time to properly review and configure your browser can do a lot to protect you from tracking. The website Cover Your Tracks (formerly Panopticlick) can tell you how well your browser settings protect your online privacy.
Here is what it had to say about my personal Google Chrome browser:
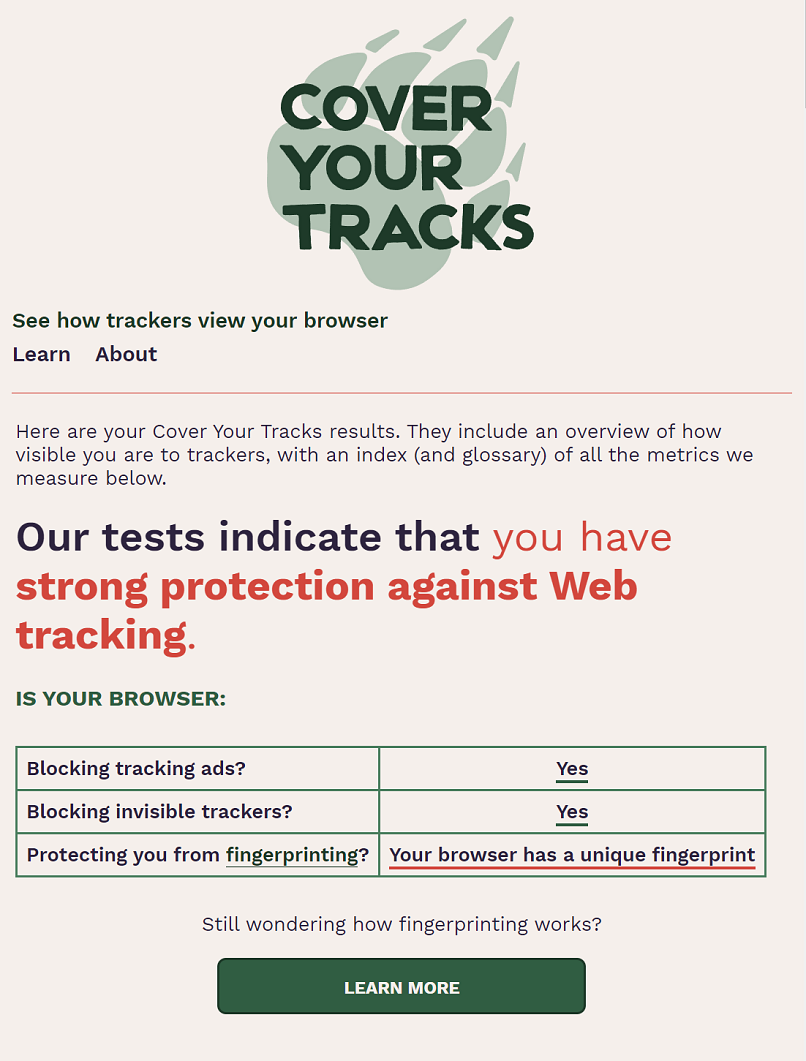
Run the test for yourself to see how your results stack up. If you're failing multiple tests, you can take some steps to improve results:
- Clear all cookies
- Clear the web cache
- Select Send a “Do Not Track” request with your browsing traffic
- Block all cookies
However, take note that none of these steps will do much to improve browser fingerprint. Unfortunately, taking steps to limit online tracking can actually make your Android browser appear more unique to the websites you visit.
Using the Tor network is one effective way to lower your risk of browser fingerprinting.
6. Change Your Search Engine for Better Online Anonymity
Search engines, and Google in particular, collect and store a good deal of information about us, some of which gets passed to third-parties. Luckily, there are some great alternatives to Google that don’t force you to give up so much of your online privacy.
One of the most popular search engines for PCs and Android that doesn’t collect user data is DuckDuckGo. Another advantage of using this search engine is that it doesn’t use your previous search history to structure your search results.
7. Secure Your Cloud Storage to Protect Data
If you're going to rely on a cloud storage service to store your files, you should choose a provider that automatically encrypts your files before they're uploaded to the cloud.
However, as I discussed earlier in this online privacy guide, there are downsides of trusting your cloud storage provider to encrypt your data for you.
The provider holds the key to unlocking your files and therefore may be able to access your data or even hand it over at the request of government authorities. This doesn’t mean you have to give up on cloud storage altogether, though.
One way to ensure your privacy online is to manually encrypt your files before uploading them to your cloud storage service. The advantage of this is that you're ultimately the only one who holds the key to decode your files. Your cloud storage provider will have no way to access your data.
Be sure not to upload your encryption keys with the files. You're the only one who should have access to these.
How to Protect Your Privacy Online through Data Encryption
Wondering how you can encrypt your data manually? I'm going to walk you through the steps. By manually encrypting your files, you can ensure that your cloud storage service can’t access your data.
1. Choose an encryption program
You can choose from many free apps to manually encrypt your data—even if you’re new to data encryption. When choosing your software, keep in mind that some encryption programs are compatible with specific cloud storage providers, so you may want to check if yours is supported.
This example will walk you through how to encrypt your data using the mobile app Boxcryptor. You can choose any software that meets the following criteria:
- Works with your cloud storage provider
- Is compatible with your Android device
- Uses end-to-end encryption, meaning that files are encrypted before they leave your machine and can’t be decrypted until you access them again
- Doesn’t store your password
That last point is very important. The program you choose shouldn’t store the password you use to encrypt your data. You're the only one who should have access to this password. Look for a statement like this one from Boxcryptor:
 2. Create a secure password—and don’t forget it!
2. Create a secure password—and don’t forget it!
When you first open Boxcryptor, it prompts you to create an account. As part of this process, you'll be asked to choose a password.

This is extremely important. The password you choose is your key to encrypting and decrypting your data. It should be unique, private, and secure.
You also need to take steps to make sure you'll never forget your password. Because Boxcryptor doesn't save user passwords, there's no way to recover your password if you forget it. This could lead to you losing access to your own data.

You should either save the password with your password manager or write it down somewhere safe. Don't forget to do this, or you could lose access to your data forever!
3. Add a cloud provider
Boxcryptor will ask you to set up a cloud service provider.

After you've connected to a provider, Boxcryptor lets you access your files and folders.
Note that if you're using the free version, you can only use Boxcryptor with one cloud storage provider.
4. Create an encrypted folder
If you need to create an encrypted folder, click the + sign at the bottom right of the screen. You'll see the following message:

Enter a file name and click "create" to proceed.

Your encrypted folder is denoted with a green lock. Now, any file you add to this folder is automatically encrypted and uploaded to your cloud storage.
8. Protect Personal Information by Securing Your Email
Most popular email services are extremely secure. Besides providing a safe HTTPS connection, many providers go the extra mile to protect your data from leaks because they know how important security is to customers.
Major email services put a lot of effort into creating robust security measures and quickly fixing vulnerabilities.
However, none of these security protocols do anything to protect your email if a government agency compels your provider to hand over your information. If you’re not comfortable with the idea of government authorities potentially reading your email, you'll need to take extra steps to protect your online privacy.
The problem is that most methods of encrypting your email are far from practical. For example, end-to-end encryption is only possible if the recipient is knowing, willing, and able to participate in the process. After all, you need your recipient to decrypt your message in order to read it.
Pretty Good Encryption (PGE) is likely the most secure method of sending an encrypted email, but it's also extremely complicated to set up manually.
The practical solution is to use a privacy-oriented email provider that offers a dedicated encrypted webmail service. One option that I recommend is ProtonMail. It’s both easy to use and also offers an extra level of protection by encrypting your email’s metadata in addition to its contents, which PGE alone doesn’t do.
9. Improve Cybersecurity with Anti-Malware and Firewall Software
Anti-malware and firewalls aren't just for computers anymore. As mobile technology advances, it's more important than ever to protect yourself from malicious apps, processes, and programs that attempt to steal your data, money, or identity.
Anti-malware apps continually scan your Android device to find and alert you of suspicious or harmful files, offering a layer of data protection. If you visit a website that tries to download a malicious file, redirect you somewhere dangerous, or otherwise compromise your internet security, your anti-malware will block it.
Firewalls monitor the traffic coming to and from your device. As you have little control over how apps behave once you download them, a firewall can help you keep them in check. They monitor app actions to ensure that no unauthorized data is being downloaded or sent by your device.
Based on your settings, the firewall will block certain traffic automatically and help you monitor the traffic that is let through.
While a one-way firewall will help protect your phone or tablet from malware, a two-way firewall will do more to protect your privacy online. Two-way firewalls stop unwanted traffic from reaching your device and also prevent apps on your device from accessing the internet without permission. This can make it impossible for invasive malware to share your private information, strengthening your privacy protection.
10. Manage Your Digital Footprint by Staying Informed on Social Media Privacy Policies and Settings
There have been some big controversies in recent years surrounding the privacy policies of popular social media platforms. Facebook, for example, has received a lot of criticism for selling all kinds of personal information about users to advertisers.
Don’t underestimate how much can be learned about you from your social media accounts. Even if each piece of information you give out may not seem private, when third parties put all of this data together it can paint a detailed picture of your life. This data could even be used to threaten or harm you.
There have been several cases of burglars and scammers taking advantage of the seemingly meaningless information given out by people’s social media accounts.
Many people regularly make posts that reveal their exact location through geotags without even realizing this information is being shared. The more information that's available about you online, the greater your risk for identity theft and other malicious activities.
If you aren’t ready to give up social media altogether, there are two steps you should take to protect your online privacy. The first is to spend some time reading and researching the privacy policies of the companies that control your accounts. You may want to be especially careful with what you share on platforms that share your information regularly with third parties.
The second thing you should do is monitor your privacy settings. Limit the number of people who can view what you post, and don’t give the platform permission to post on your behalf or access your location. Check these settings regularly to make sure that nothing has changed as the platform updates.
11. Only Download Trusted Apps and Regularly Review Permissions to Ensure Data Security
There are apps for everything these days. The Google Play store offers over 3.3 million options, with choices from games and social media platforms to weight loss aids and productivity tools. And as with anything that you download, apps may contain malware or other issues that can put your online privacy at risk.
To protect your online privacy, before you download an app consider these points:
- Only download apps from trusted app sources and developers. While there's always the chance that something bad will sneak through, it's less likely when you use verified sources.
- If you're downloading an unfamiliar app, read its reviews and check out its ratings to see what other users think about it. Read carefully to determine whether reviews are genuine or possibly written by bots to put you at ease. Stay away from apps that seem suspicious, as they could compromise your personal information security.
- Carefully review the permissions an app requests. Think hard about those that request info that's unnecessary. For example, be wary of a game that needs access to your address book.
- Regularly double-check the permissions on any apps you've downloaded to ensure nothing has changed.
If it's not necessary for the function of an app, consider disabling the location permission to keep from unintentionally broadcasting your movements. Some apps may track your behavior, such as where you like to shop or how often you travel, to sell that info to third-parties or display targeted ads.
VPNs Help Safeguard Your Online Privacy
Protecting your online privacy is more important than ever, and this online privacy guide emphasizes the steps you can take to safeguard your personal information. With technology playing a more prominent role in our everyday routines, we face potential vulnerabilities that could compromise our privacy and overall safety.
Taking the time and effort, and spending the money, to protect your privacy is worth it, when you consider the costs of dealing with a catastrophe after your identity is stolen or your personal information is leaked.
Trying to address all the possible threats to your security may feel overwhelming, but keep in mind that not everyone needs to be concerned about every single privacy threat.
Instead of trying to do everything, you should take the time to consider which threats are of most concern to you and target them. VPNs for Android devices make it easy to personalize your protection and address your biggest privacy concerns directly.




Please, comment on how to improve this article. Your feedback matters!