Report: Financial CRM Leaks Private Financial Data from Banks and Credit Unions Across the USA
Led by Noam Rotem and Ran Locar, vpnMentor's research team recently discovered an exposed database belonging to financial services CRM platform BankSight.
BankSight's CRM software provides small banks and credit unions with numerous tools and resources to boost customer relations and increase revenue.
The exposed database was connected to the CRM and, thus, leaking highly sensitive client data from numerous client businesses. Unfortunately, a few months after it managed to secure the server, another server leaked similar data.
As a result, by not securing this database, BankSight compromised the privacy, security, and financial welfare of customers at any business using its software.
Data Breach Summary
| Company | BankSight |
| Headquarters | San Francisco, USA |
| Industry | Finance; CRM |
| Size of data in gigabytes | 440+ GB as of 19th May; 15-40GB of data uploaded daily |
| Number of records | 301,636,596 |
| No. of people exposed | Estimated to be 100,000s |
| Geographical scope | USA and Australia |
| Types of data exposed | Financial records; PII data; business statements; much more |
| Potential impact | Financial fraud; phishing; identity theft |
| Data storage format | Elasticsearch |
Company Profile
Founded Oct 2015 and based in San Francisco, BankSight "enables retail bankers, business bankers, and wealth managers to deliver meaningful experiences to customers through timely, intelligent and actionable customer insights and a single view of the customer."
Built on the Microsoft Business Applications Platform, it claims to be the "First Intelligent Banking CRM 100% purpose-built for banks and credit union."
In 2019, BankSight combined with Bottomline Technologies, an early investor in the company, to expand across the USA and overseas.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what's at stake or who's leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the owner of the database was not initially clear. However, based on our team's investigation, we concluded that BankSight was the most likely candidate for the following reasons:
- The database’s TLS certificate contained ‘BankSight’
- Logs are full of references to subdomains of BankSight.net
- Logs contain references to class names in the package com.BankSight: “logger_name":"com.BankSight.common.extension.script.Invoker"
Once we confirmed BankSight, we contacted the company to disclose our findings and provide details to help them close the breach.
- Date discovered: 19th of May 2020
- Date vendors contacted: 25th of May 2020
- Date of 2nd contact attempt: 4th of June (Banksight + Microsoft)
- Date of Action: 30th June 2020
- Date new server discovered: 9th September 2020
- Date vendor contacted about the new leak: 9th September 2020
- Date of vendor response: 10th September 2020
- Date server closed: 11th September 2020
Banksight never got back to us, we saw the server closed on June 30. A few months later on September 9, we saw another one of their servers open and reached out to them again. BankSight responded on September 10, 2020 and the server was closed on September 11, 2020.
Example of Entries in the Database
BankSight states on its website that:
"We follow generally accepted industry standards to protect the personal information submitted to us, both during transmission and once we receive it. No method of transmission over the Internet, or method of electronic storage, is 100% secure, however. Therefore, we cannot guarantee its absolute security."
Based on our discovery, the company had not taken sufficient steps to protect its users' data.
The exposed database was live at the time of our investigation, with new logs being uploaded daily. While the number of records varied, the combined size of the uploads ranged from 15-40 GB every day.
The origins of the data can explain the amount being uploaded. The database was storing records from every business using BankSight's CRM in one place.
Whenever somebody working at one of Banksight's clients input information into the CRM or connected with them via email, it was uploaded and logged into the exposed database.
As a result, these logs contained vast amounts of information on individuals and businesses across the USA, as well as banks in Australia.
Alongside financial forecasts, statements, and assessments, the records also included significant Personally Identifiable Information (PII) data about the people exposed.
This included:
- Full names
- SSNs
- Email addresses
- Phone numbers
- Home and business addresses
- Employment and business ownership details
- Financial data for businesses and individuals
- Personal notes from people looking for loans or postpone on loan payments, exposing private family and business information
Many of the entries in the database were explicitly related to Coronavirus. For example, customers asking for loans due to the impact on their businesses. Others were asking for a postponement of loan payments for the same reason.
All of this information was completely exposed, as the database was unsecured, publicly accessible, and the entries poorly masked.
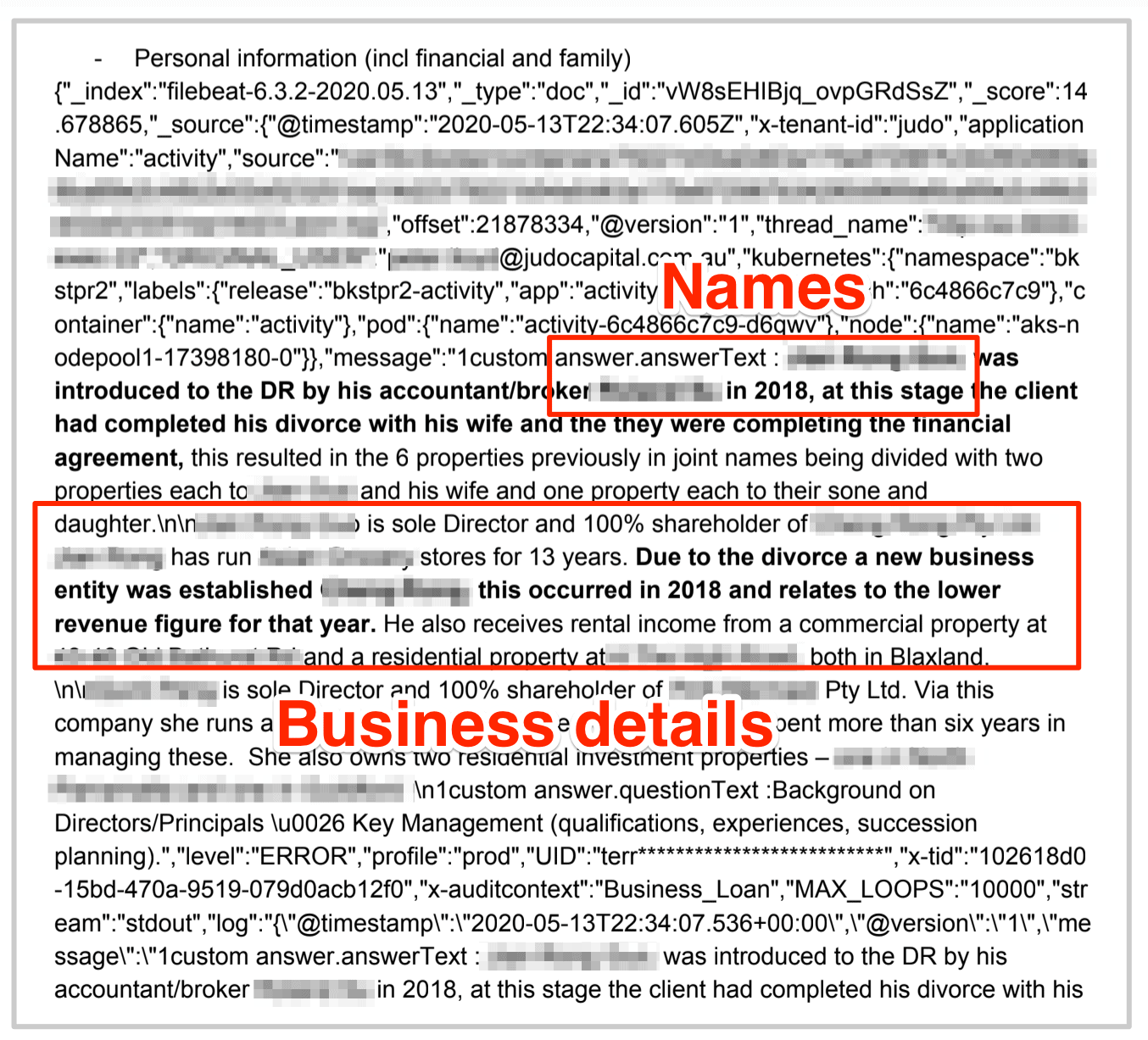
Pulling data points from a sample of entries, we were quickly able to identify individuals and businesses with a simple Google search.
Thanks to the combination of PII data and personal details, alongside publicly available data sourced on Google, Banksight's database would be an absolute goldmine for malicious hackers and cybercriminals.
Data Breach Impact
By combining the financial information contained within BankSight's database with the matching PII data and publicly available records, cybercriminals could create highly sophisticated and effective fraud schemes to target customers of Banksight's clients.
Hackers rarely get such detailed summaries and insights into an individual's or small business's finances. BankSight could have provided that opportunity, leading to devastating consequences for potentially 100,000s of people.
However, they wouldn't need to just rely on complex schemes, as a simple phishing campaign could prove just as effective. By sending phishing emails imitating a business using BankSight's CRM software, criminals could easily trick the potential victim into any of the following:
- Providing credit card details
- Providing access credentials for private financial accounts elsewhere online
- Clicking a link that will embed malicious software on their devices, such as ransomware, malware, and spyware
Nearly 50% of cyber attacks committed in 2019 targeted small businesses - exactly the kind of companies that depend on small banks and credit unions for financing - as they're seen as easy targets by cybercriminals. By not securing its CRM database, BankSight could have made it even easier.
Aside from cybercriminals, this database was also a potential goldmine for black and grey market money lenders. Gaining insight into who is applying for loans, and who's rejected, would allow them to create incredibly exploitative and micro-targeted marketing campaigns. Doing so, they could trap small businesses and private individuals in high interest, unfair, and morally dubious loans.
Coronavirus has created an enormous strain on households and businesses, and many people exposed in this breach were applying for financial assistance as a result.
If turned down by a BankSight client, they may resort to taking loans from short term lenders at a much higher rate for many months and years.
Unfortunately, this puts even more people at risk from cybercriminals and dishonest lenders, who could exploit their private data to devastating effect.
By not securing its CRM's database, BankSight created a huge security risk that compromised the financial and personal welfare of many people across North America and Australia.
For BankSight
With such a large group of people potentially impacted by this data breach, BankSight also faces numerous adverse outcomes.
Most immediately, it may lose current clients and partners if banks and credit unions don't trust the company to protect their customers' data adequately. They may also struggle to gain new business, due to the publicity the leak will attract.
A growing majority of small business owners rank cybersecurity and data protection as two of their biggest concerns and may now be reluctant to use Banksight's software.
Banksight's competitors may exploit the leak by taking advantage of the bad publicity the company is going to receive and enticing its customers to rival platforms.
Finally, the company may face regulatory action, investigation, and fines from the governments of countries in which it operates.
All of these outcomes would create numerous headaches for the company and potentially impact its revenue considerably in the short term.
Advice from the Experts
BankSight could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn't require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For BankSight Users
If you are a customer of BankSight and are worried about the potential implications of this breach on you or your clients, it would be advisable to directly reach out to the company. Inquire about the measures they are implementing to safeguard the data of your customers.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in BankSight's database as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
BankSight was using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database owner, usually a commercial company.
As ethical hackers, we're obliged to inform a company when discovering flaws in their online security. We reached out to BankSight, not only to let them know about the vulnerability but also to suggest ways to make their system secure.
These ethics also mean we carry a responsibility to the public. BankSight users and their customers must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the data of 10,000s of American energy sector workers. We also revealed that a website built to promote India’s BHIM epayments technology had compromised the privacy and security of millions of people across the country. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect the Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: 22.10.2020 ]
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!