How Not to Get Hacked - A Beginner's Guidebook to Online Security- Free Chapter Included!
Harsh Maurya is a software engineer by day and an ethical hacker by night. Although he states that he is not a security or networking expert, he likes to think of himself as qualified for educating the public about online security. In his book How Not to Get Hacked, he gives a beginners' overview of some best practices that would help you protect yourself from online threats. We grabbed Maurya for a quick interview, and got a free chapter from his book How Not to Get Hacked, exclusively for vpnMentor readers! Share
What made you write this book?
The field of online security always interested me, but the thing which bothered me most was the increasing cases of cyber crime and the amount of trouble people undergo after an incident. Interestingly, people who call themselves tech-savvy are also not aware of the most basic attacks. There are numerous articles online which tells you how to be safe online. But those are typically monotonous and gives no reasoning for their suggestions. My aim from this book is to impart an awareness among people, regardless of their technical expertise, providing the information in as creative and interesting way as possible.
What new knowledge did you gain whilst writing the book?
For me, this was my first book as an author. There was great learning both in terms of domain knowledge and soft skills. To write a book which is not boring is a very challenging task. In one hand, you have tons of information to share which might not be suited for everyone, on the other hand, you have to be creative in converting your thoughts to words. My biggest hurdle was to strike a balance between the level of technical information I am providing versus simplicity. I specifically wanted to target common people more than the tech-savvy ones.
How Not to Get Hacked can be bought online here, but it's also available as part of a 6 months promotion where you can buy it in combo with for panda antivirus.
Below is the preface of the How Not to Get Hacked, followed by a free chapter about wifi sniffing.
Preface
We live in a world where almost every aspect of our life is controlled in some way or the other by technology. Whether we like it or not, we are so much dependent on technology that we cannot imagine to live without it. Though it has definitely made our lives easier, such dependency has some serious repercussions. Security has become so much prominent that companies spend insane amount of money to protect its data from hackers. One might think that on a personal level, it is not that important to care about these things, however nothing can be further from the truth. “Ignorance is bliss” is probably just the opposite of what I am trying to convey here. Because this world of internet is huge and you will find every type of person here- one who likes you, one who hates you, one who want to steal every single penny of yours. I’ll give you numerous examples where people got scammed of their hard-earned money so I cannot stress enough on how important this awareness is. It is important that we take care of ourselves.
Getting hacked – Wi-Fi sniffing
You went to a popular restaurant for dinner with a friend. The food is taking time to reach your table. You and your friend hang out so much that you have nothing much to talk and you both are just busy playing with your mobiles. Suddenly you realize that it is the last day for paying your electricity bill. The restaurant offers free Wi-Fi. What a good luck you have today, right? So you instantly paid your electricity bill online using the restaurant’s free Wi-Fi and thereafter checked in your Facebook status – having dinner with my best friend at ***. Oh wait, the food has also come and it looks tasty as hell. What a fine night you are having. So the two of you enjoy every bit of slice and discuss how easy life has become after the advent of technology and after everything has become available online these days. The next morning, you wake up from the bed and check your phone for missed whatsapp messages when suddenly you see this text:
“$10,000 has been successfully transferred from your bank account ****** to
the account xxxxxxxx. Available balance: $12.45”
You are instantly shocked to see this. All your savings from past year just vanished in thin year. You decide to call the police but they suggest you should rather contact the cybercrime department. After a long struggle of six months, you give up the chase. Apparently the hacker was very smart and cops are not able to snatch him or at least it appears so.
What caused this unfortunate incident? The truth is, it can occur to anyone. It's human nature to assume that something which has never happened to us won't happen in the future. However, if we put in so much effort to earn money, why not take a little care to safeguard it? That's the least we can do. To shed light on what precisely occurred in this situation and how to prevent its recurrence, let's delve into understanding how it all operates.
Wi-Fi has become a very common technology used by millions of people to access the internet. However potential loopholes in the underlying technology has left a lot of room for the hackers to attack and exploit the wireless networks. Please note that securing a Wi-Fi setup is a topic on its own and I am not going to cover it here since it requires some technical skills and is outside the scope of this book. Still in one liner I would like to comment to those people who have set-up a Wi-Fi network (not the users), to follow some basic guidelines, like using WPA and WPA2, not using WEP, not broadcasting the name of the network etc.
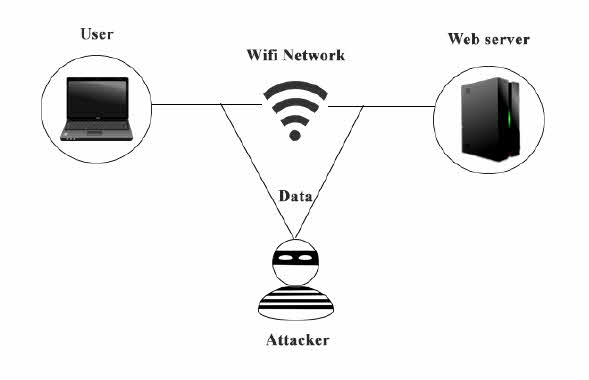
For a normal user who just uses a Wi-Fi connection to gain access to internet, here is a fact: everything you do over a Wi-Fi network is completely unsecure if you are not taking special measures to secure it. Basically, any user who is connected to the same Wi-Fi network as yours can sniff your data and use it for his advantage. For that reason, I have only single advice for this section – DO NOT use public Wi-Fi network to access your email or confidential data like banking etc. Because you do not know who all are connected to the same network. Since it is open and free, an attacker can connect to the same network and monitor all your activities. Without going into technical details, let me warn you that all your passwords are also prone to attack and can be easily hacked by the attacker. If you are like me who understands things better with a diagram, here it how it works:
As you can see, before your data reaches the server, an attacker sniffs in between and copies all the data to his computer which he can later manipulate in different ways like grabbing passwords and other sensitive information from it. So, follow this thumb of rule – NEVER use public Wi-Fi for sensitive work. You can browse the internet in general but try not to login to your online accounts. That’s it for this chapter.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!